Overview
You can use Radius to authenticate users into the Palo Alto Firewall. You can also use Radius to manage authorization (admin role) by defining Vendor-Specific Attributes (VSAs).
The article describes the steps to configure and verify Palo Alto admin authentication/authorization with Cisco ISE.
If you want to use TACACS+, please check out my other blog here
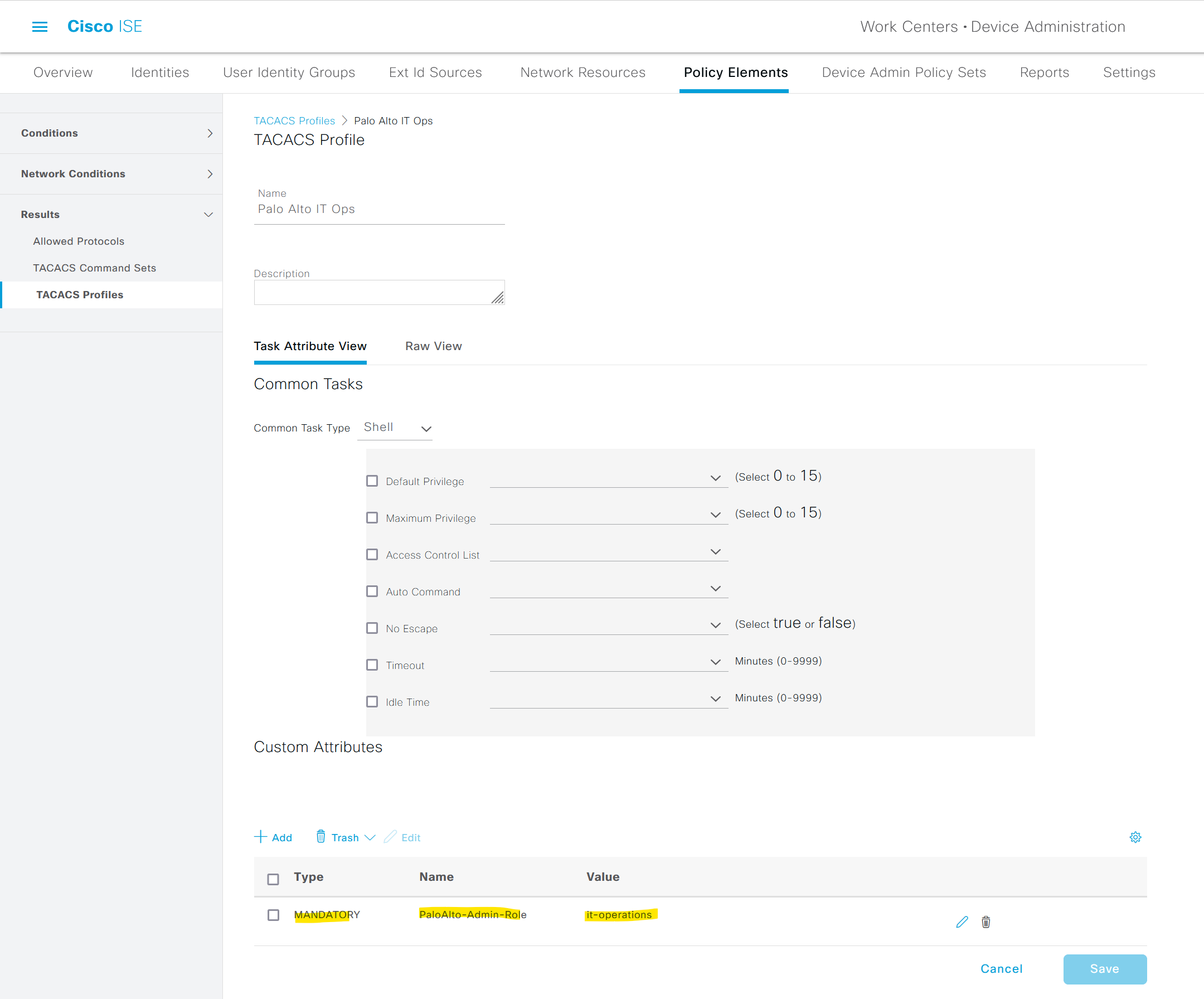
Diagram
Software Version
- Palo Alto - 9.0.0
- Cisco ISE - 2.6
Overview
- noc-admin should have superuser access
- noc-user should have superuser read-only access
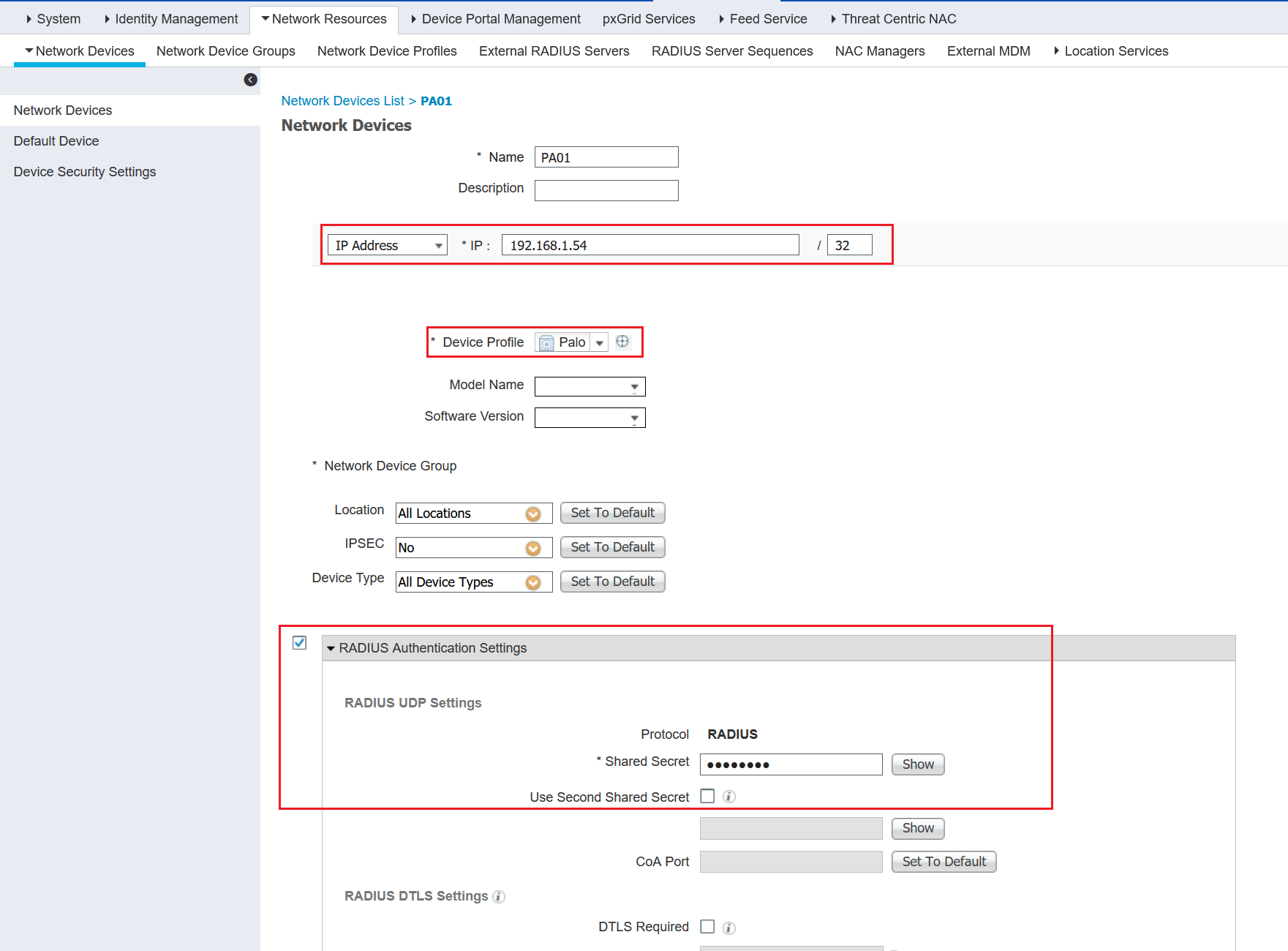
Please make sure that you have connectivity between Cisco ISE and PA Management Interface or Service Route Configuration.
Palo Alto Configuration
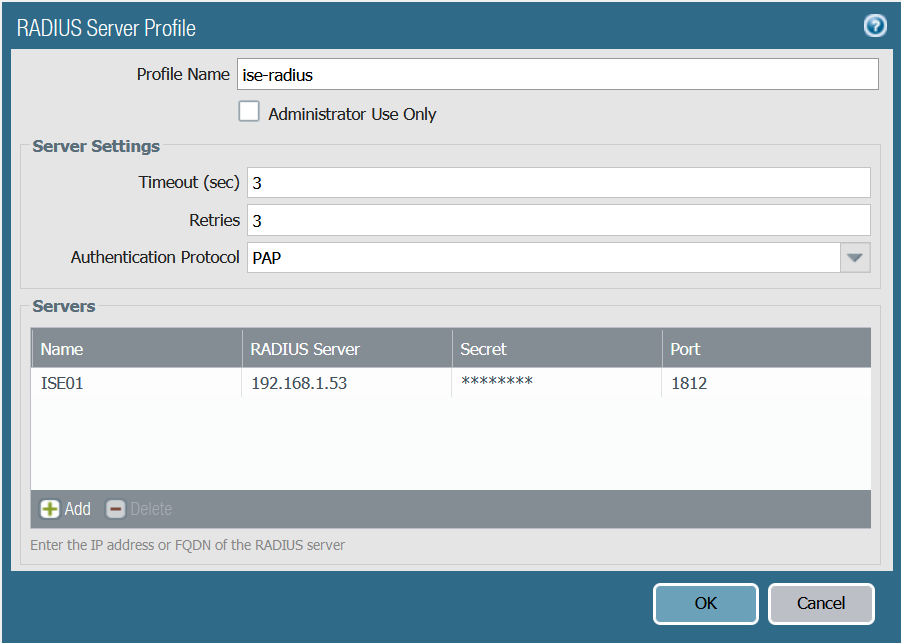
1. Configure Radius Server
Select the appropriate authentication protocol depending on your environment. I'm using PAP in this example which is easier to configure.
PEAP-MSCHAPv2 authentication is shown at the end of the article.
Device > Server Profile > Radius
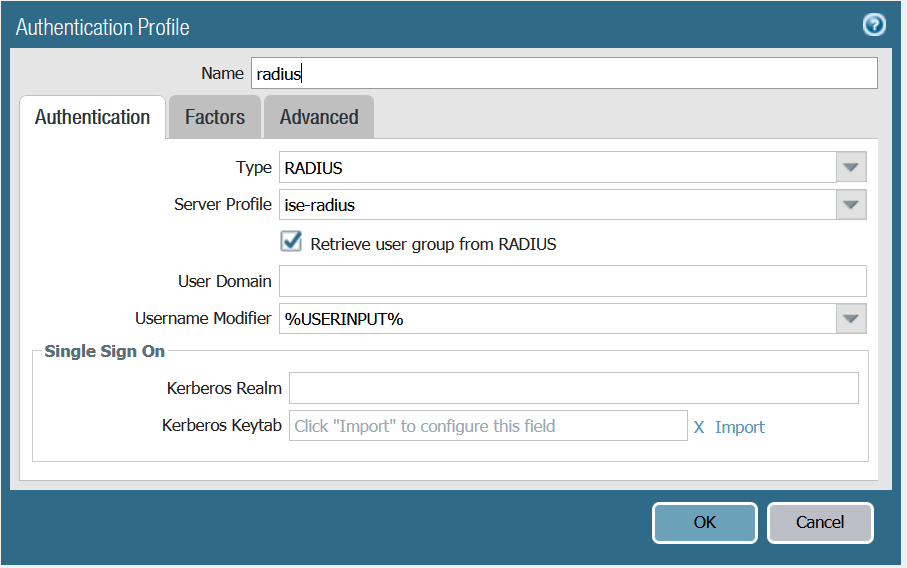
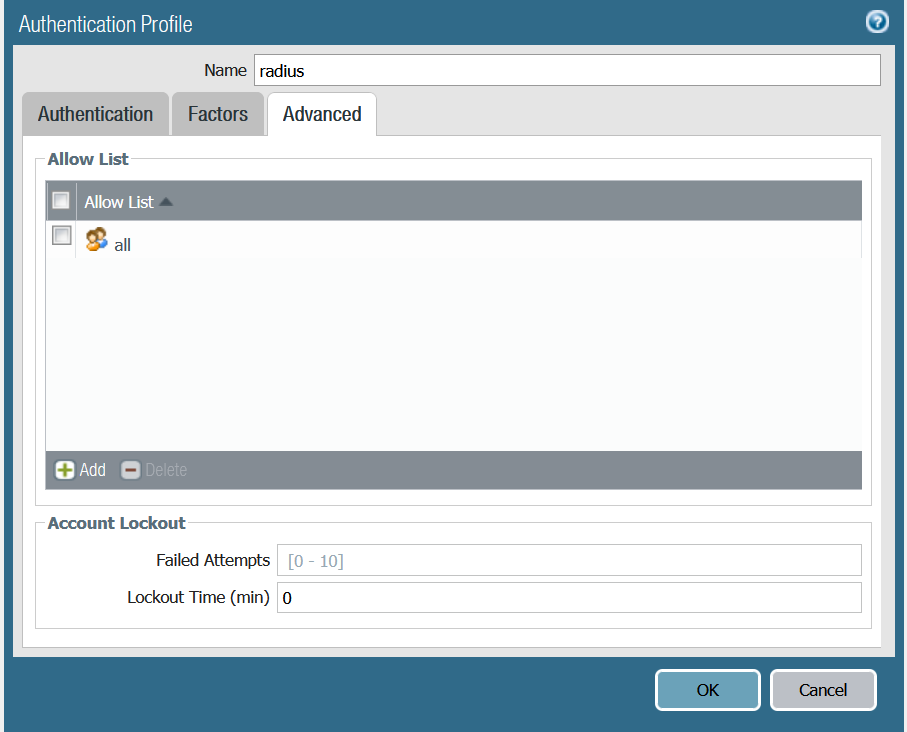
2. Create Authentication Profile
Device > Authentication Profile
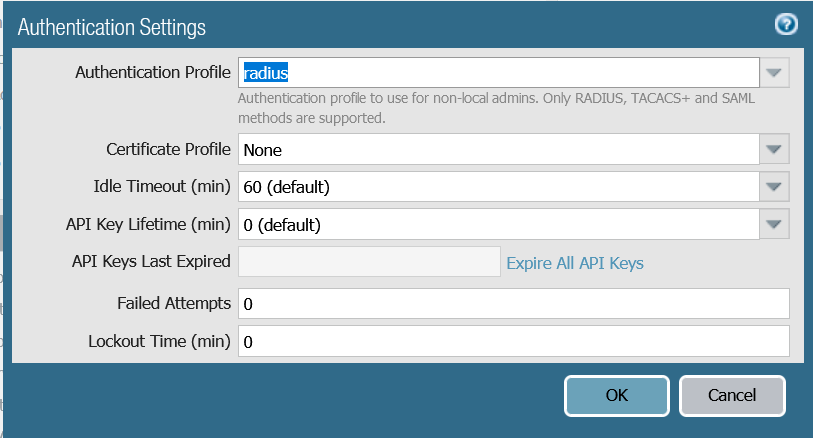
3. Authentication Settings
Device > Setup > Management > Authentication Settings
Cisco ISE Configuration
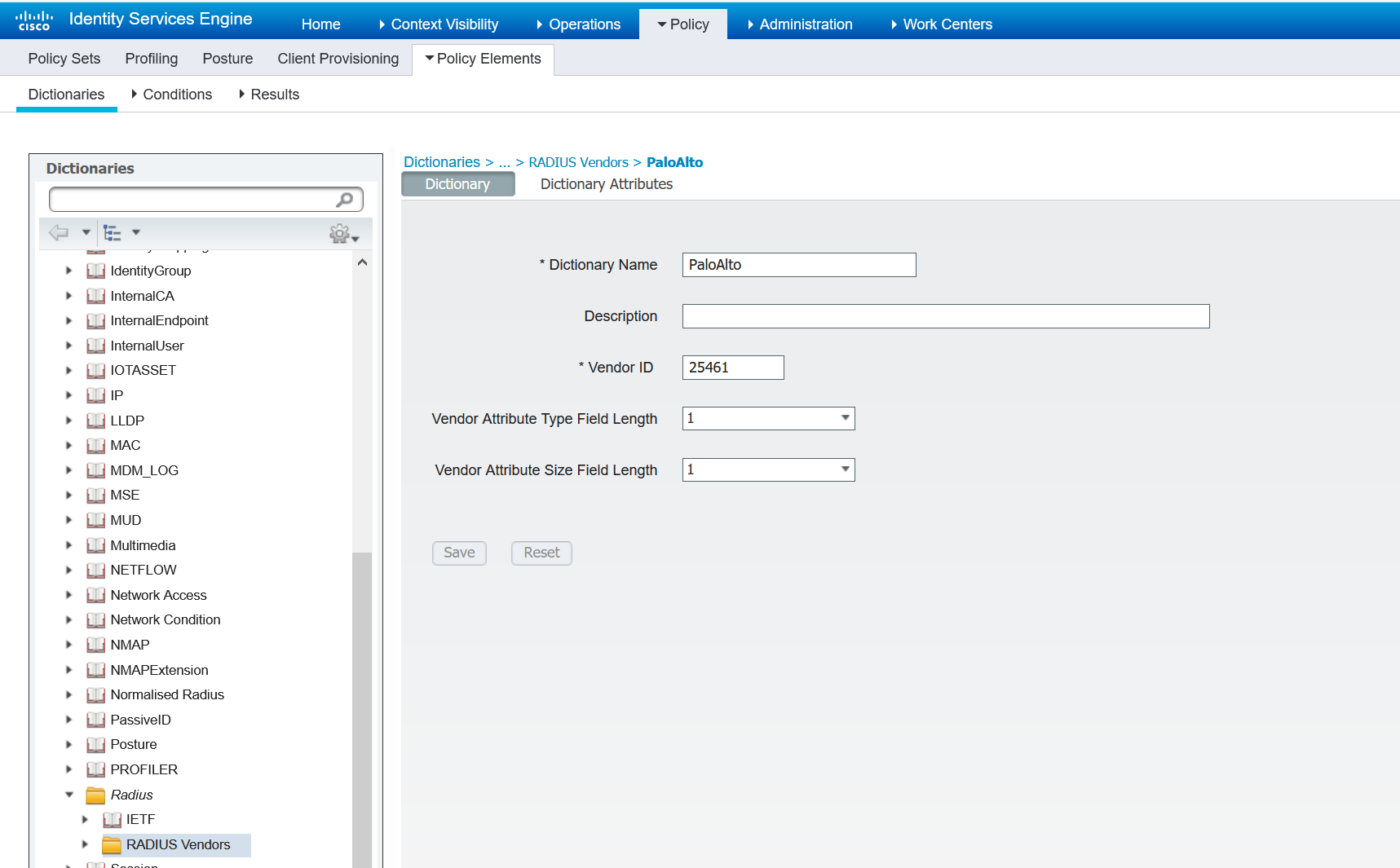
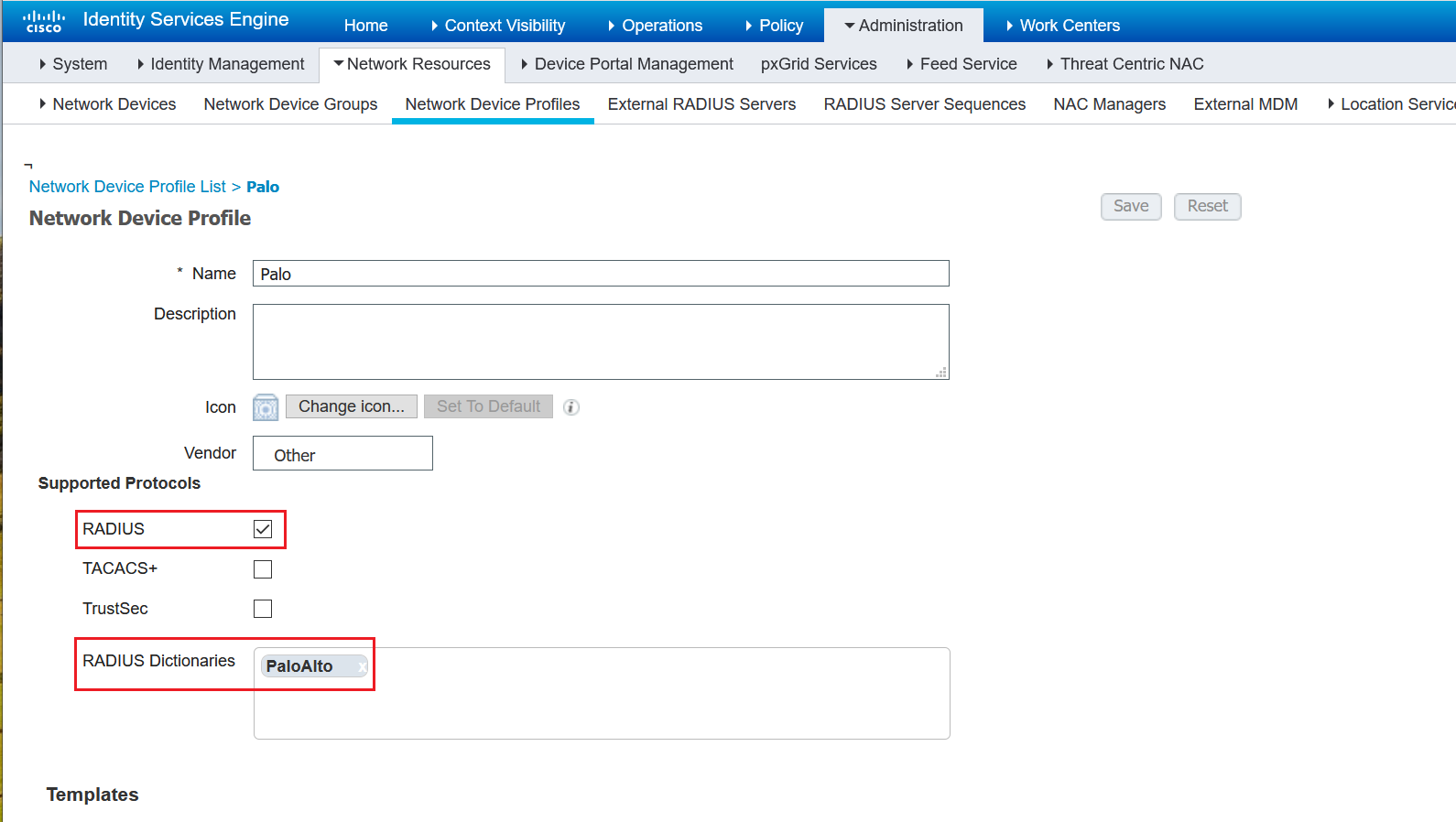
1. Create Palo Alto Radius Dictionary
The Palo Alto Radius dictionary defines the authentication attributes needed for communication between a PA and Cisco ISE server. You can download the dictionary from here: https://docs.paloaltonetworks.com/resources/radius-dictionary.html
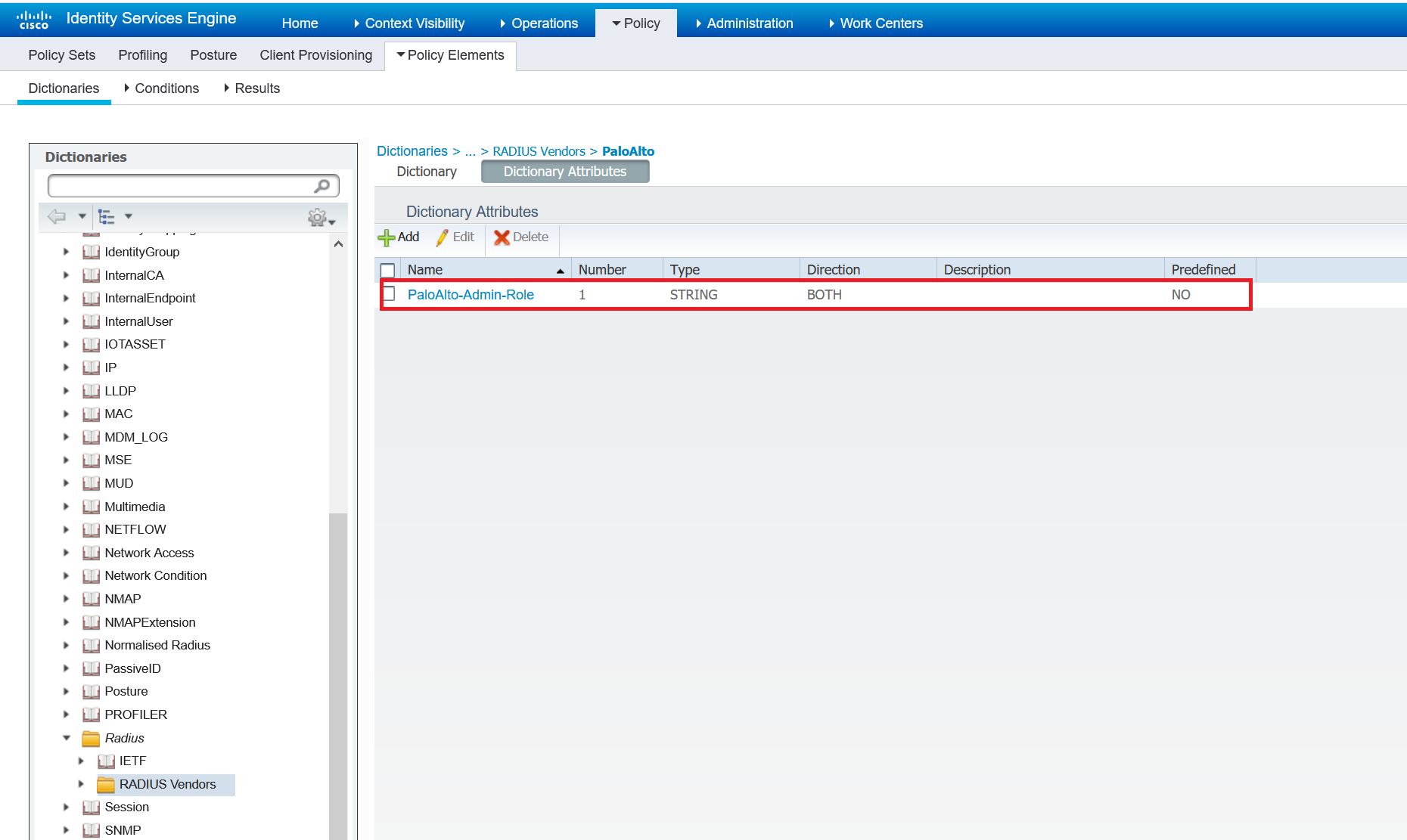
2. Configure Dictionary Attributes
I'm only using one attribute in this exmple. You can see the full list on the above URL.
PaloAlto-Admin-Role is the name of the role for the user. It can be the name of a custom Admin role profile configured on the firewall or one of the following predefined roles:
- superuser : Superuser (used in this example)
- superreader : Superuser (read-only) (used in this example)
- deviceadmin : Device administrator
- devicereader : Device administrator (read-only)
- vsysadmin : Virtual system administrator
- vsysreader : Virtual system administrator (read-only)
3. Create a Network Device Profile
4. Add the Network Device
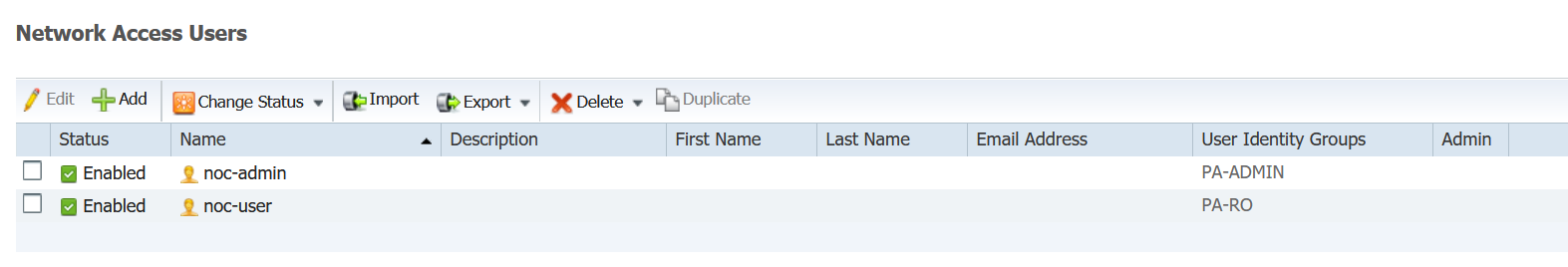
5. Create users
I created two users in two different groups. The names are self-explanatory. In a production environment, you are most likely to have the users on AD. For this example, I'm using local user accounts.
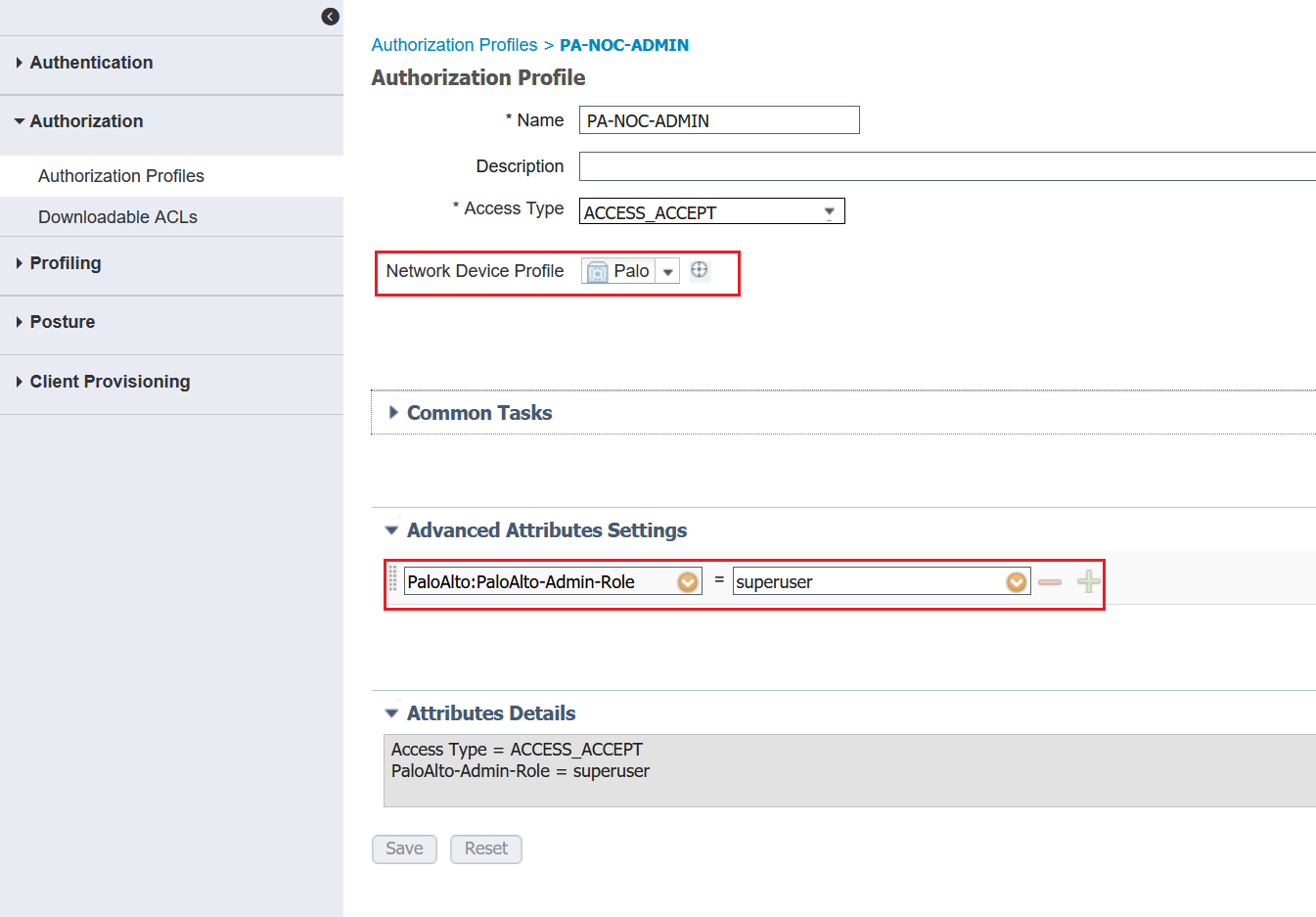
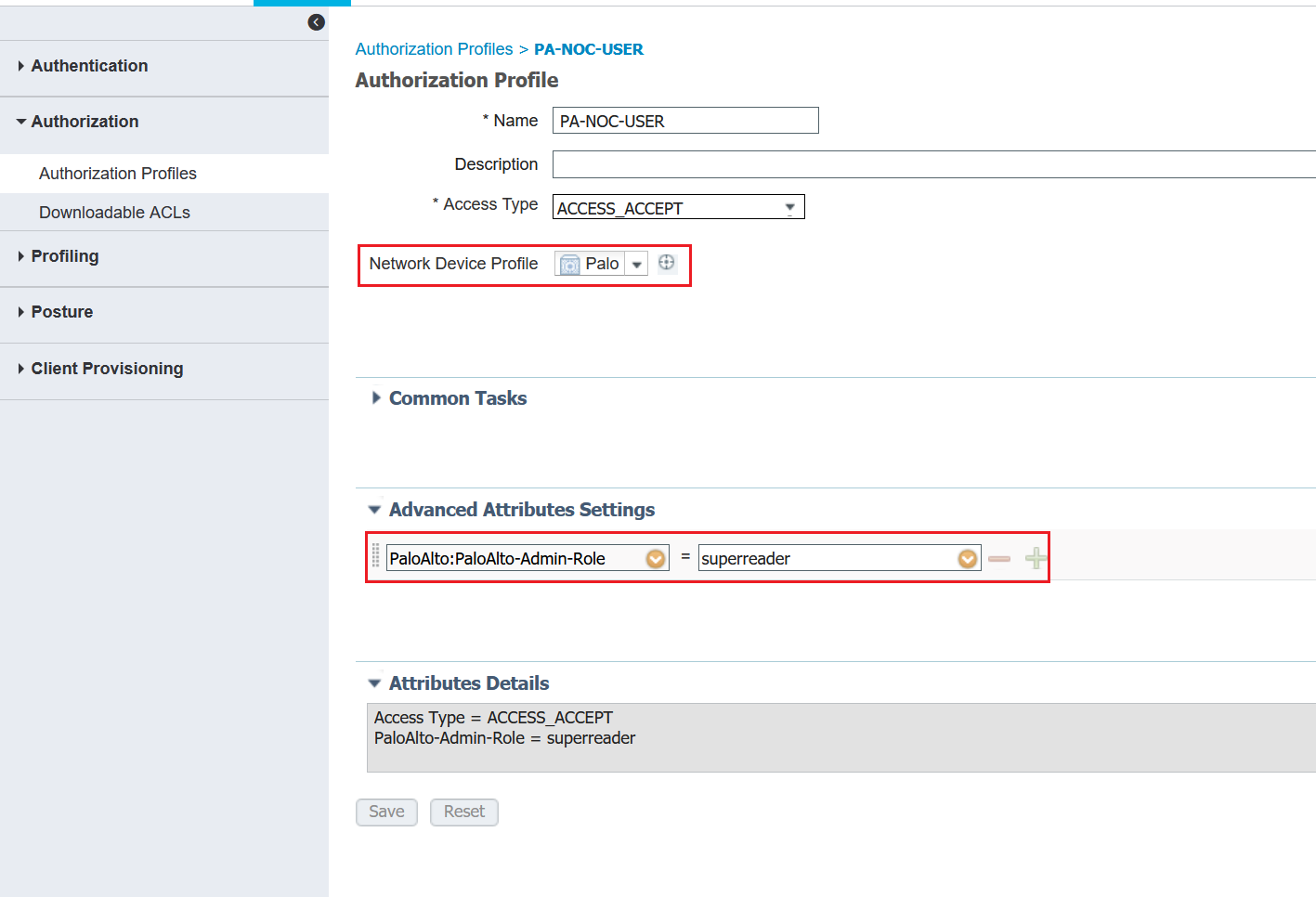
6. Authorization Profile
I created two authorization profiles which is used later on the policy. As you can see below, I'm using two of the predefined roles. (superuser, superreader). Please make sure that you select the 'Palo' Network Device Profile we created on the previous step.
If you want to use custom Admin Roles, the names must match on the PA and Cisco ISE.
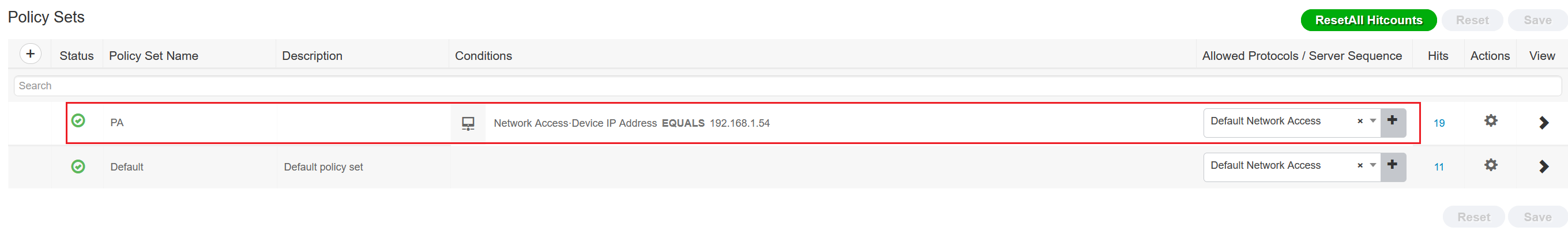
7. Policy Sets
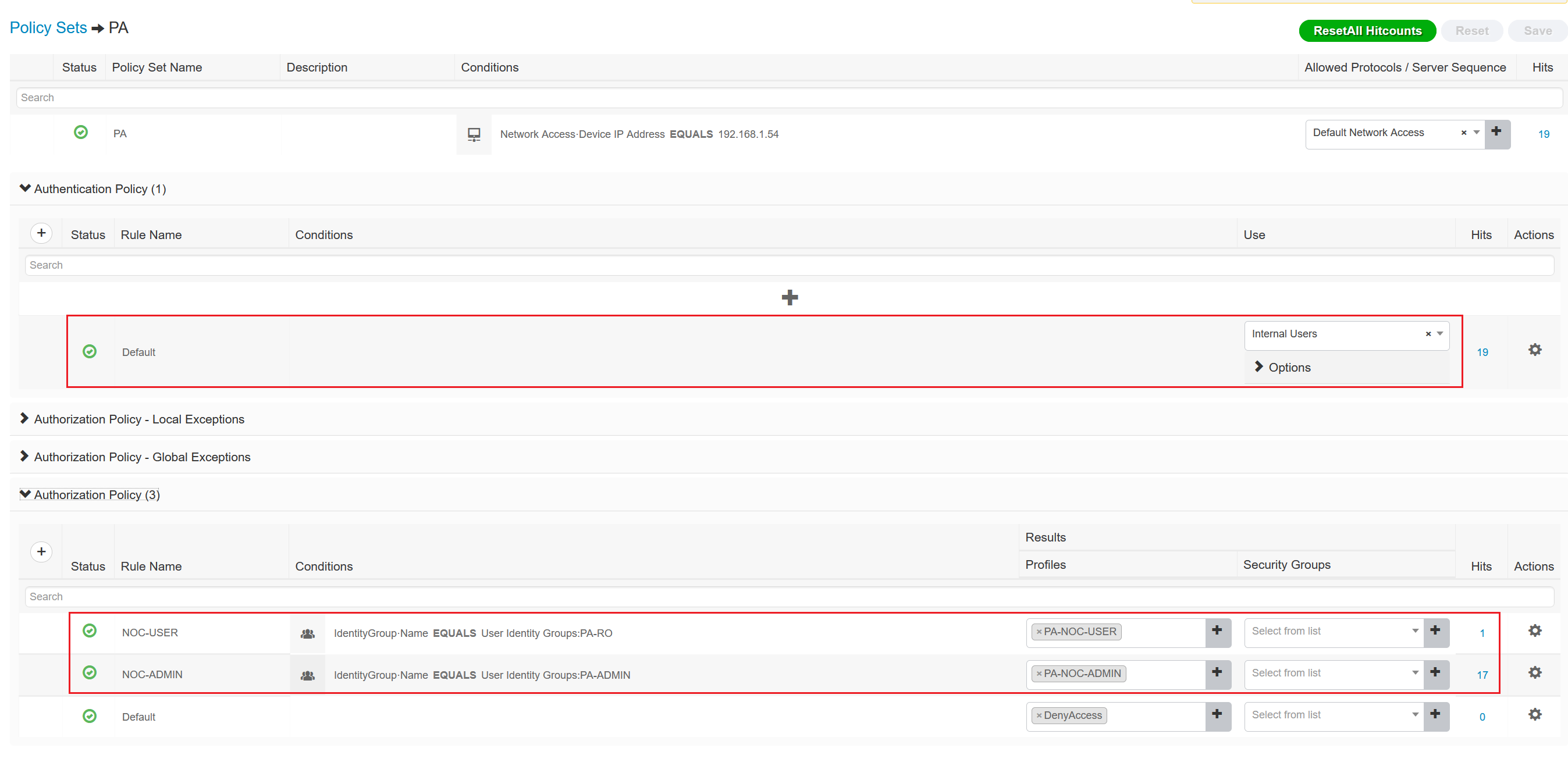
Verification
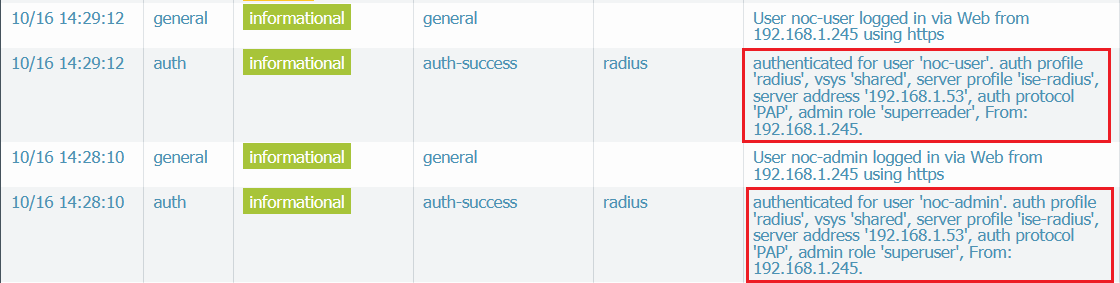
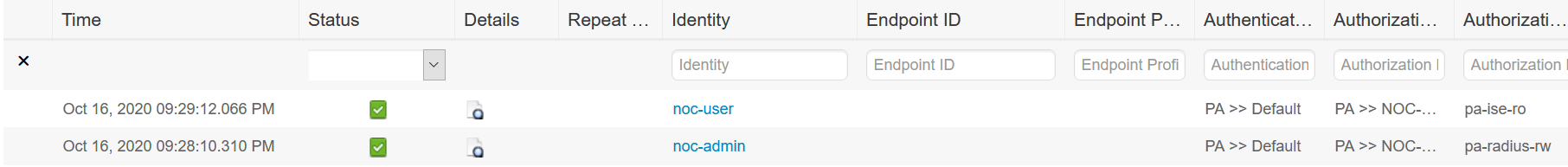
I can also SSH into the PA using either of the user account.
Last login: Sat Oct 17 09:26:29 2020 from 192.168.1.245
Number of failed attempts since last successful login: 0
noc-admin@PA-VM> configure
Entering configuration mode
[edit]
noc-admin@PA-VM# exit
Exiting configuration mode
noc-admin@PA-VM> Custom Admin Role
So far, I have used the predefined roles which are superuser and superreader.
1. Let's create a custom role called 'dashboard' which provides access only to the PA Dashboard. The role also doesn't provide access to the CLI.
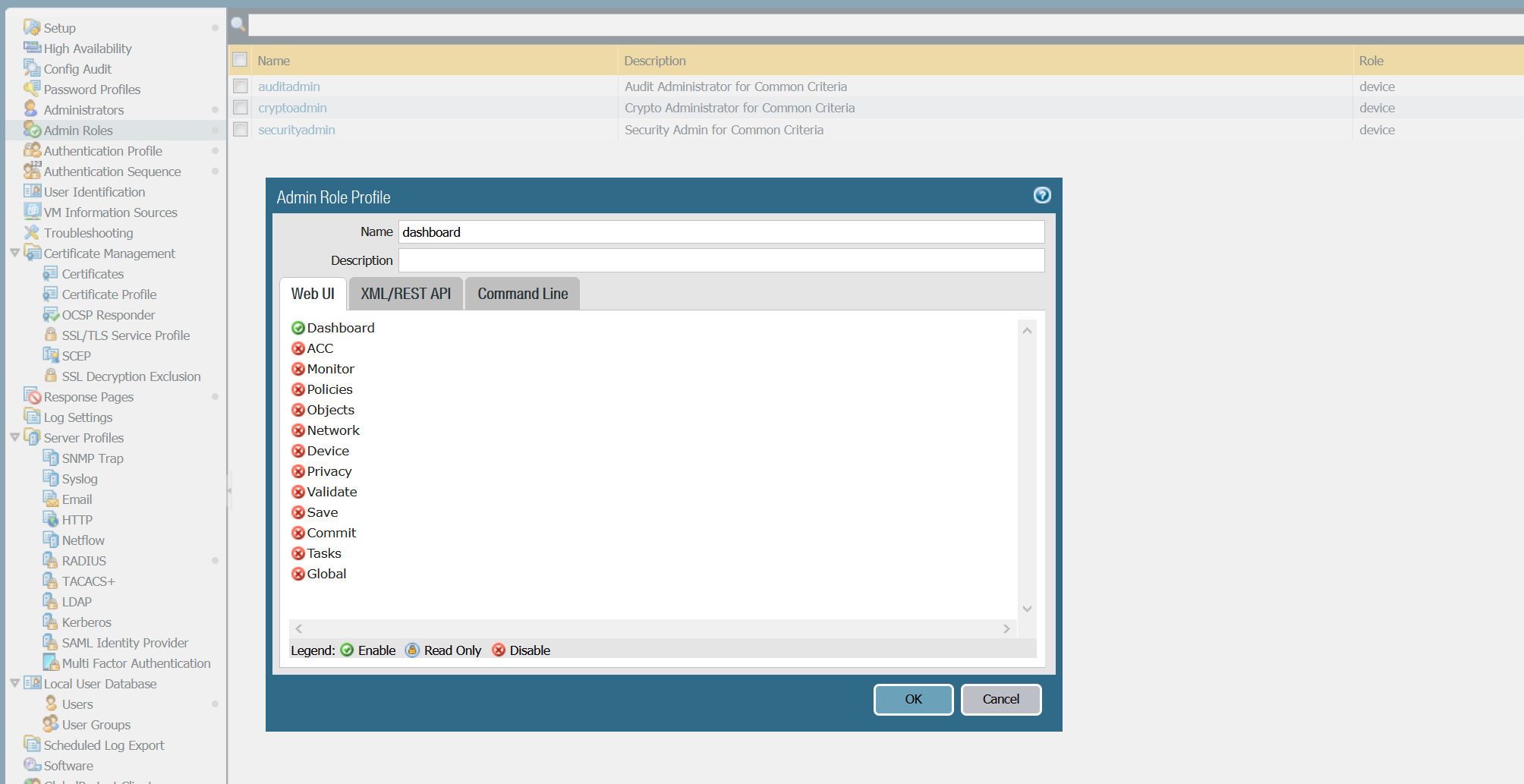
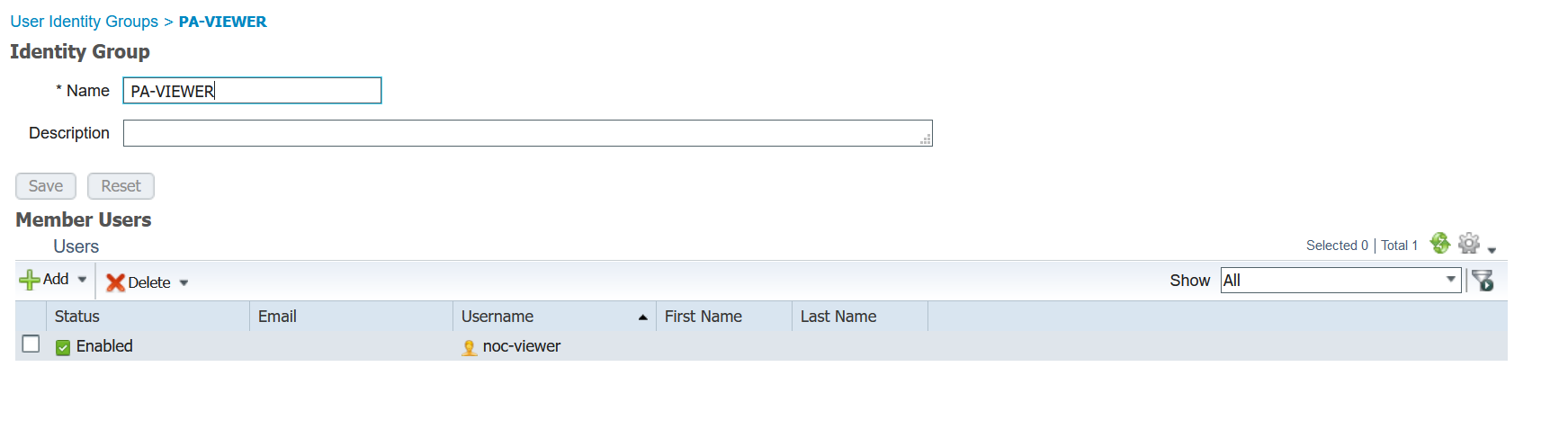
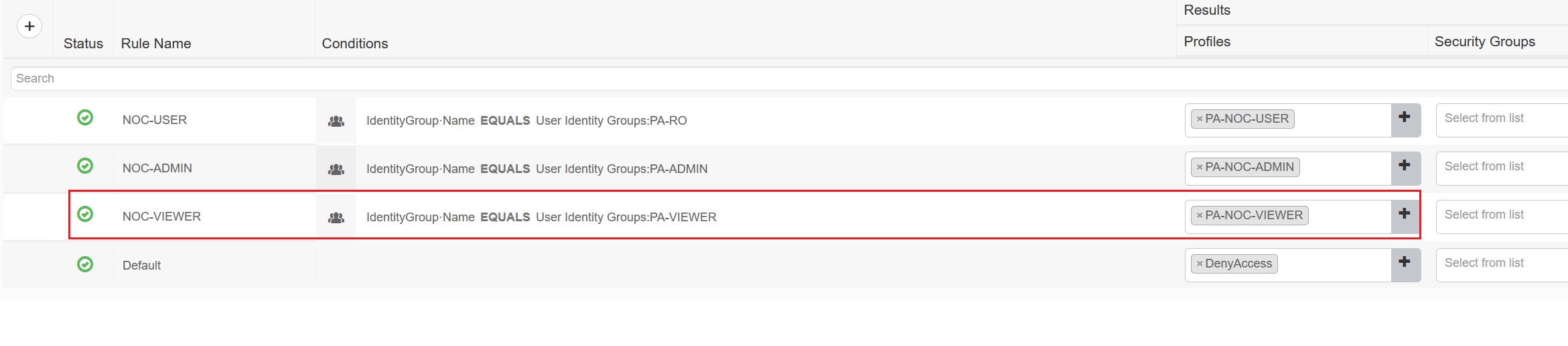
2. I created a new user called 'noc-viewer' and added the user to the 'PA-VIEWER' user group on Cisco ISE.
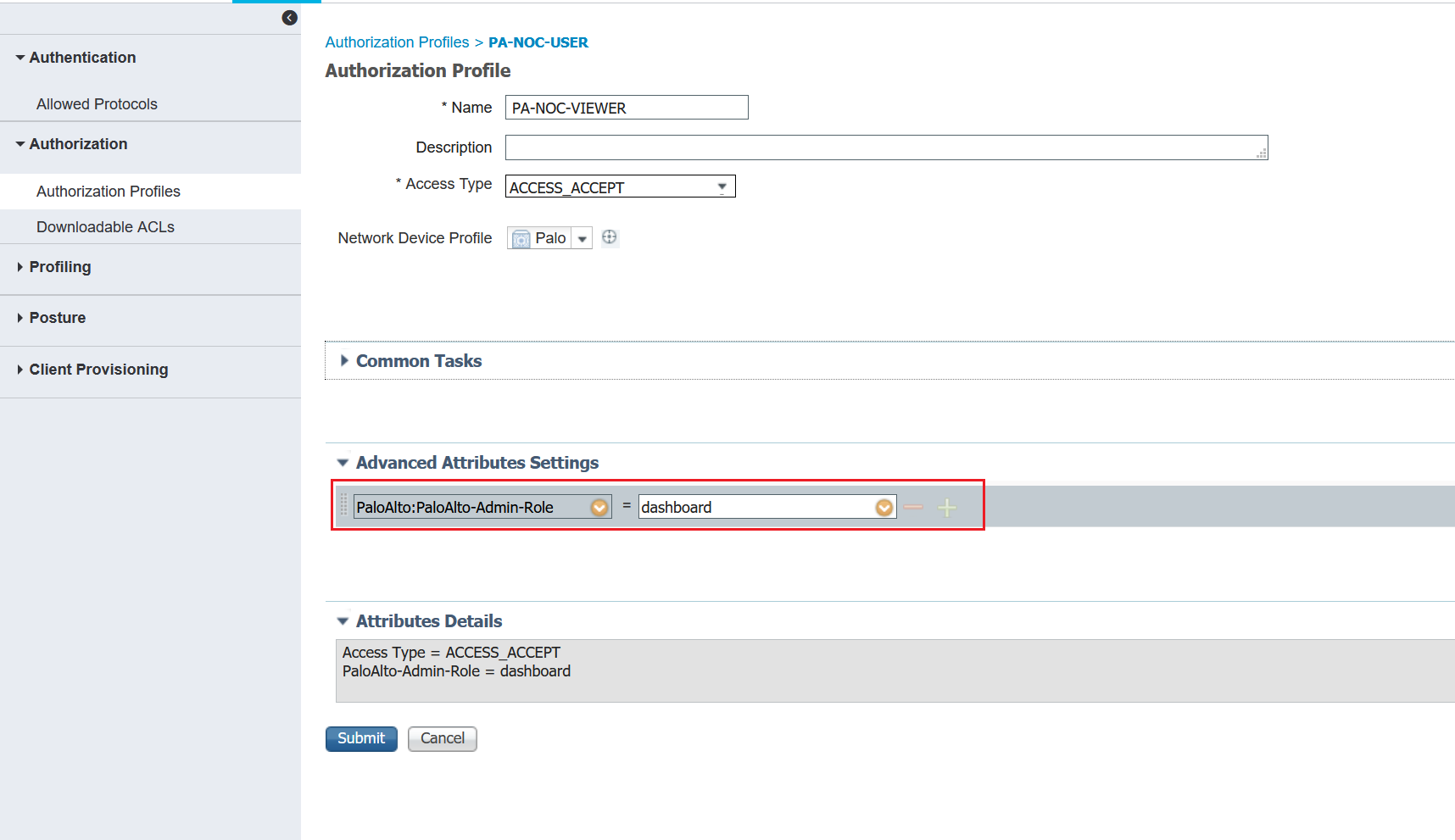
3. Create a new 'Authorization Profile'.
Please note that the admin role name should match in the PA and ISE.
4. Create a new Authorization Policy
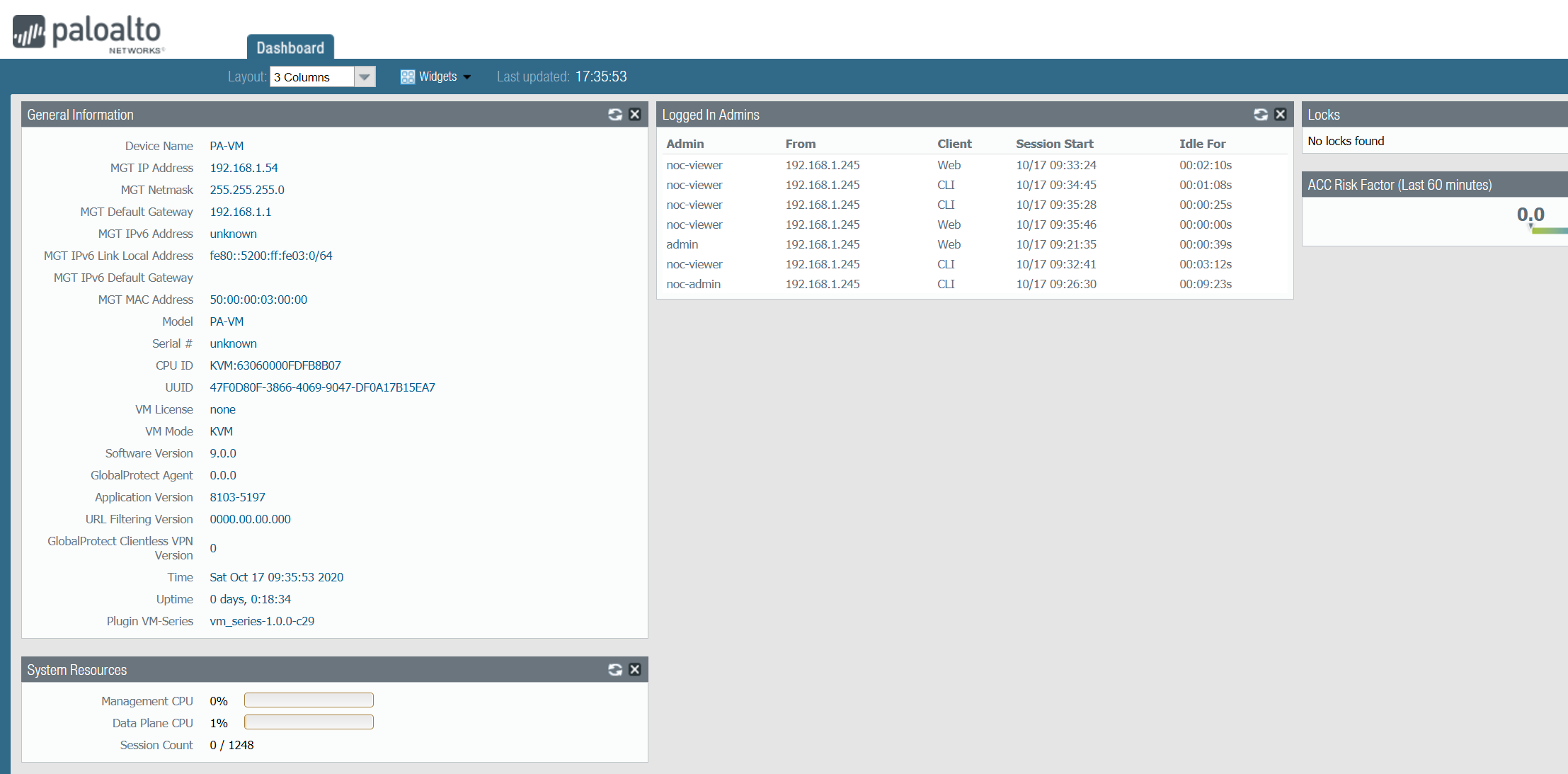
As you can see below, access to the CLI is denied and only the dashboard is shown.
Last login: Sat Oct 17 09:32:41 2020 from 192.168.1.245
Invalid user. Please login using a valid account.
PEAP-MSCHAPv2
PAP is considered the least secure option for Radius. In this example, I will show you how to configure PEAP-MSCHAPv2 for Radius.
EAP-PEAP creates encrypted tunnels between the firewall and the Radius server (ISE) to securely transmit the credentials. EAP creates an inner tunnel and an outer tunnel. After the Radius server’s certificate is validated, the firewall creates the outer tunnel using SSL. After the encrypted TLS outer tunnel has been established, the firewall creates the inner tunnel to transmit the user’s credentials to the server.
EAP-PEAP uses TLS only to authenticate the server (ISE) to the client (PA) but not the client (PA) to the server (ISE). This way, only the server is required to have a certificate.
The first step is to generate a CSR from ISE and submit it to the Certificate Authority (CA) in order to obtain the signed system certificate. This certificate will be presented as a Server Certificate by ISE during EAP-PEAP authentication.
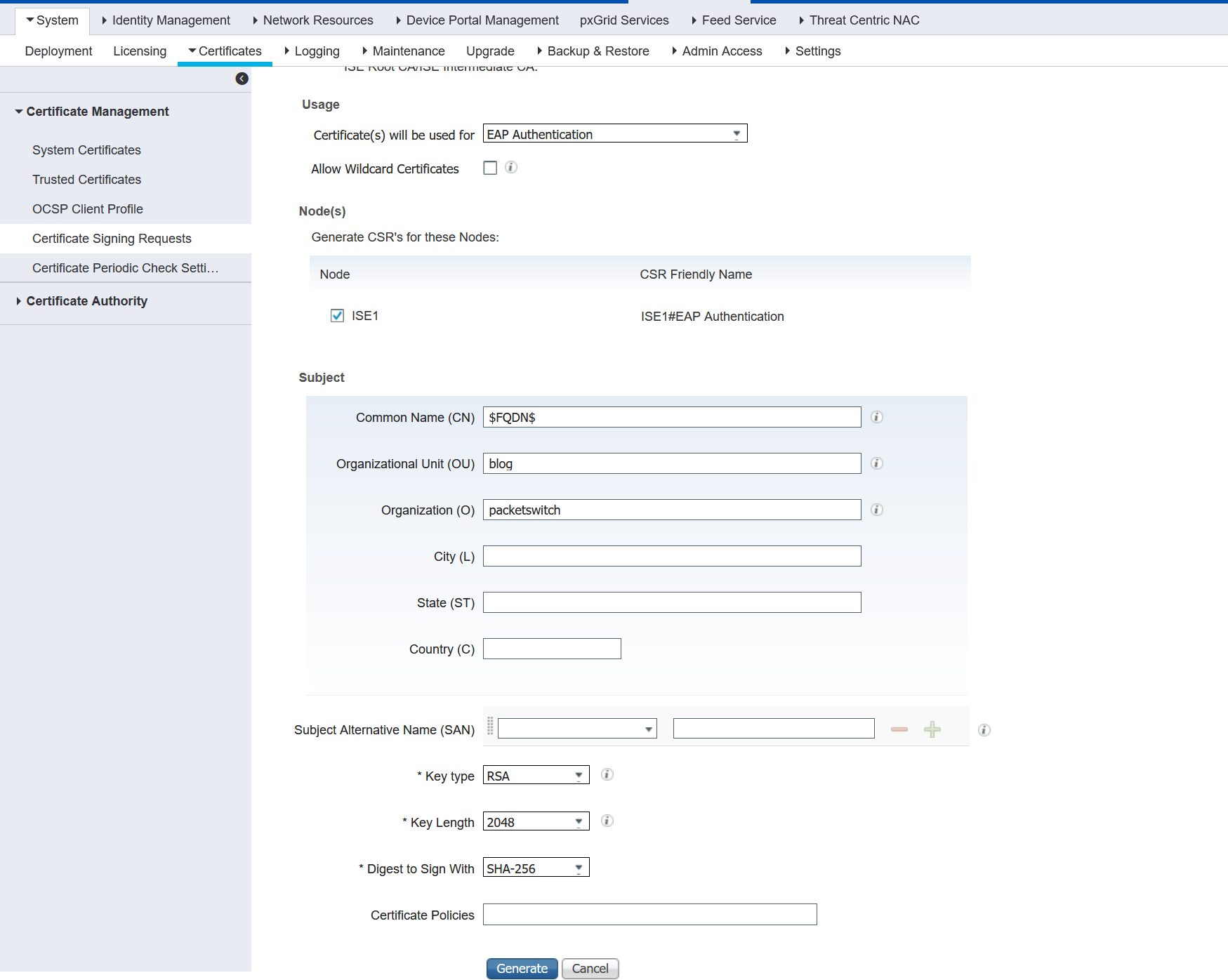
Step -1 Generate CSR
Administration > Certificate Management > Certificate Signing Request
I'm creating a system certificate just for EAP. You may use the same certificate for multiple purposes such as EAP, Admin, Portal etc.
Step - 2 Get this CSR signed by the CA.
In this example, I'm using an internal CA to sign the CSR (openssl).
If you want to learn more about OpenSSL CA, please check out this URL https://deliciousbrains.com/ssl-certificate-authority-for-local-https-development/
pi@raspberrypi:~/certs $ openssl x509 -req -in ISE1EAPAuthentication.pem -CA packetswitchCA.pem -CAkey packetswitchCA.key -CAcreateserial -out ise1.example.local.crt -days 825 -sha256
Signature ok
subject=CN = ISE1.example.local, OU = blog, O = packetswitch
Getting CA Private Key
Enter pass phrase for packetswitchCA.key:
pi@raspberrypi:~/certs $
-rw-r--r-- 1 pi pi 1106 Oct 21 11:32 ISE1EAPAuthentication.pem < CSR
-rw-r--r-- 1 pi pi 1172 Oct 21 11:36 ise1.example.local.crt < signed cert **
-rw------- 1 pi pi 1743 Oct 21 11:24 packetswitchCA.key < CA's key
-rw-r--r-- 1 pi pi 1342 Oct 21 11:26 packetswitchCA.pem < CA root certStep 3 - Import the CA root Certificate into ISE.
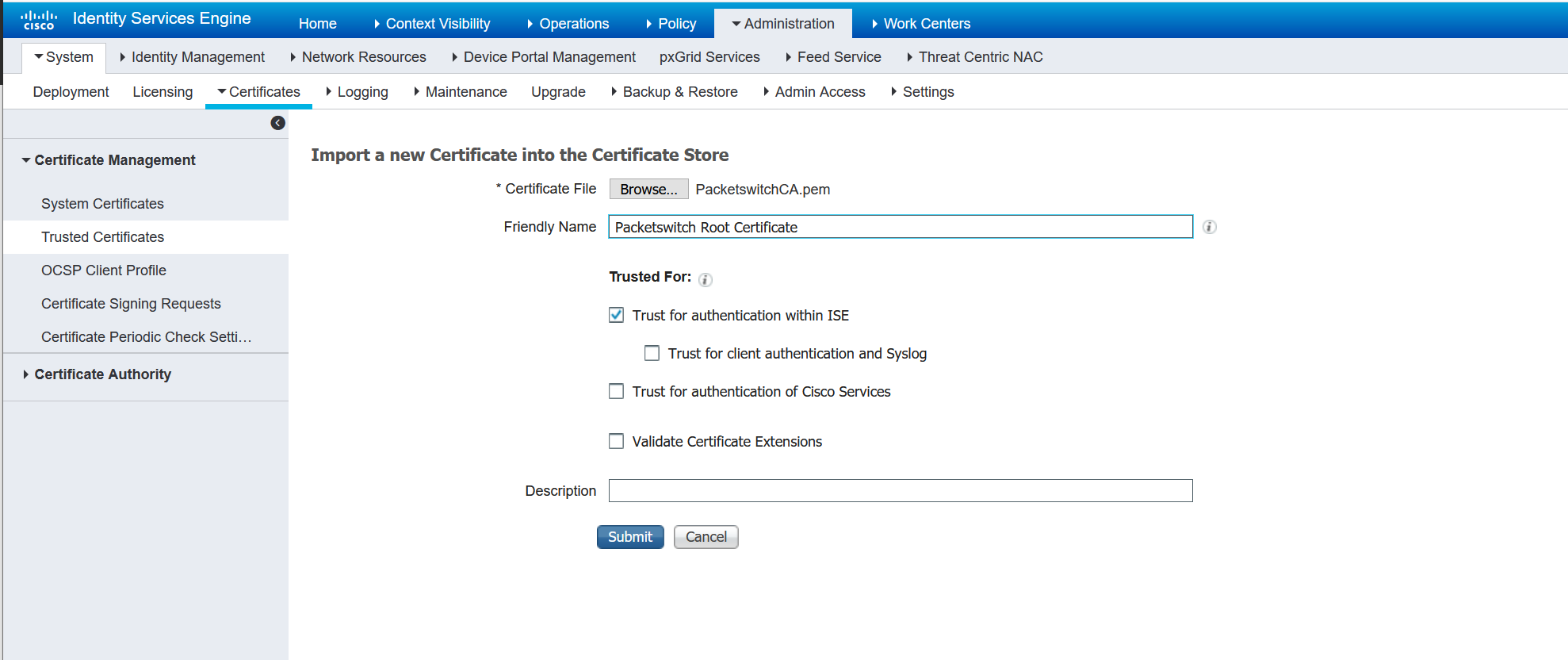
Administration > Certificate Management > Trusted Certificates
We need to import the CA root certificate packetswitchCA.pem into ISE.
Step 4 - Bind the signed certificate to the CSR
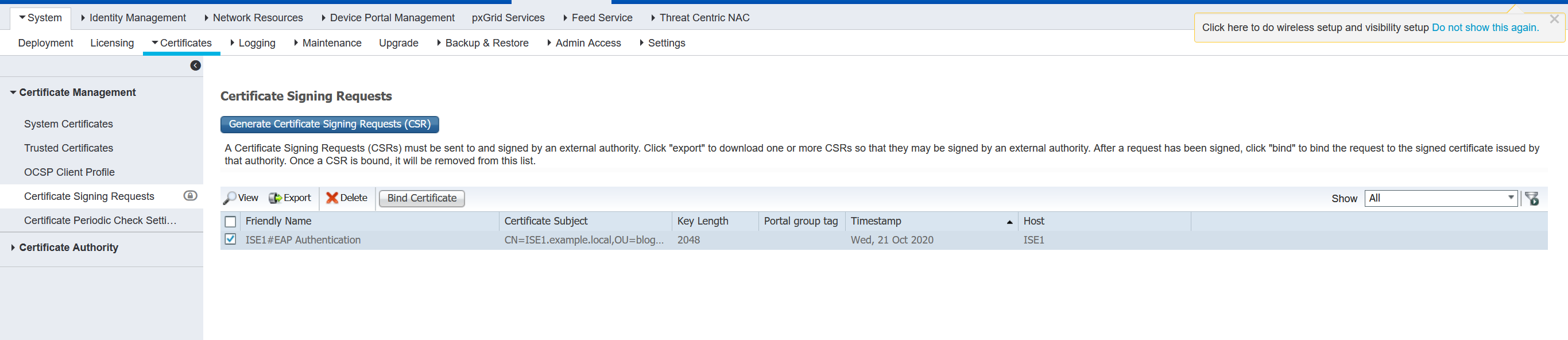
Administration > Certificate Management > Certificate Signing Request > Bind Certificate
Bind the CSR with ise1.example.local.crt which we downloaded from the CA server (openssl) on step - 2
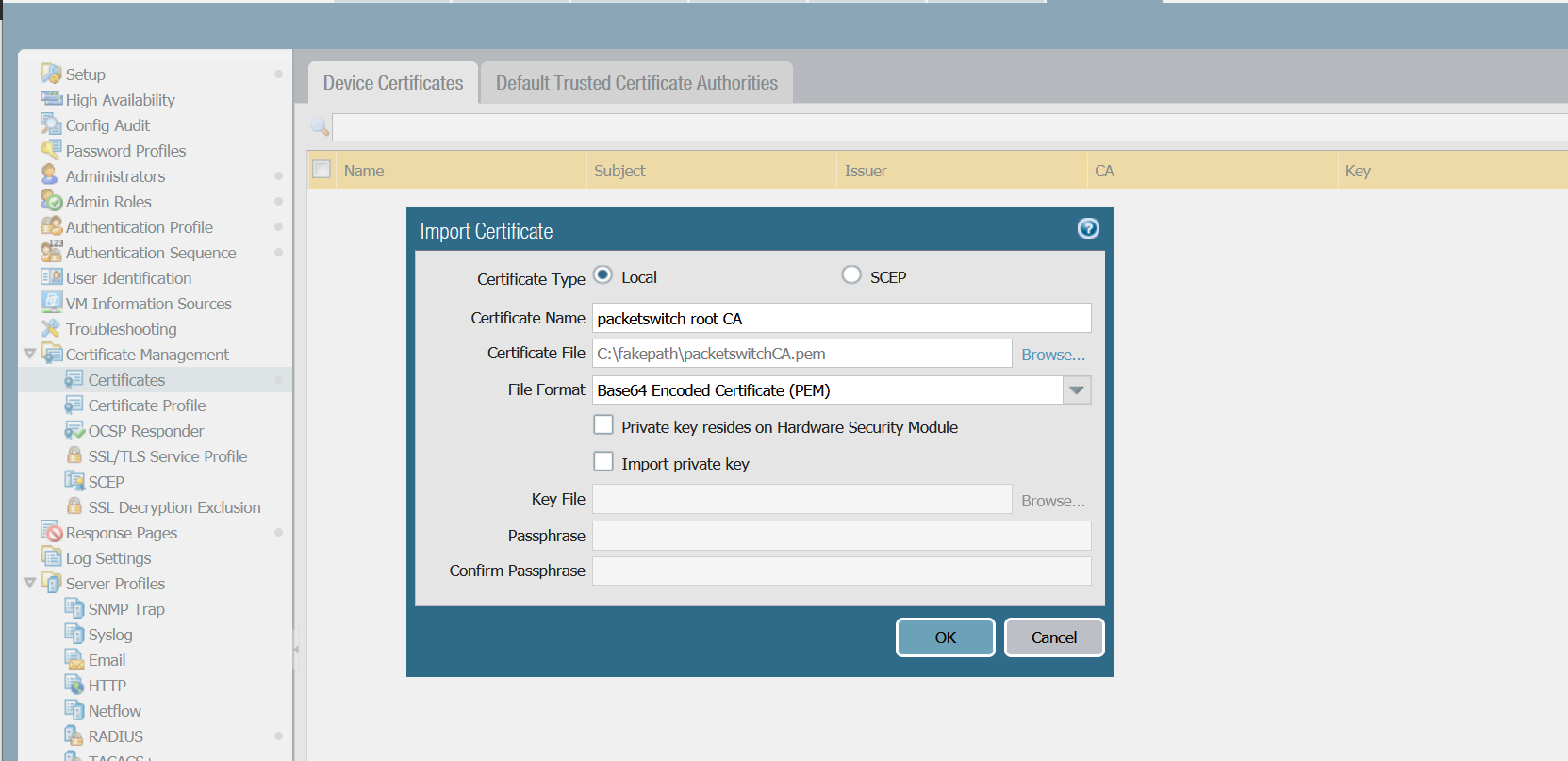
Step - 5 Import CA root Certificate into Palo Alto
EAP certificate we imported on step - 4 will be presented as a Server Certificate by ISE during EAP-PEAP authentication. The certificate is signed by an internal CA which is not trusted by Palo Alto. So, we need to import the root CA into Palo Alto.
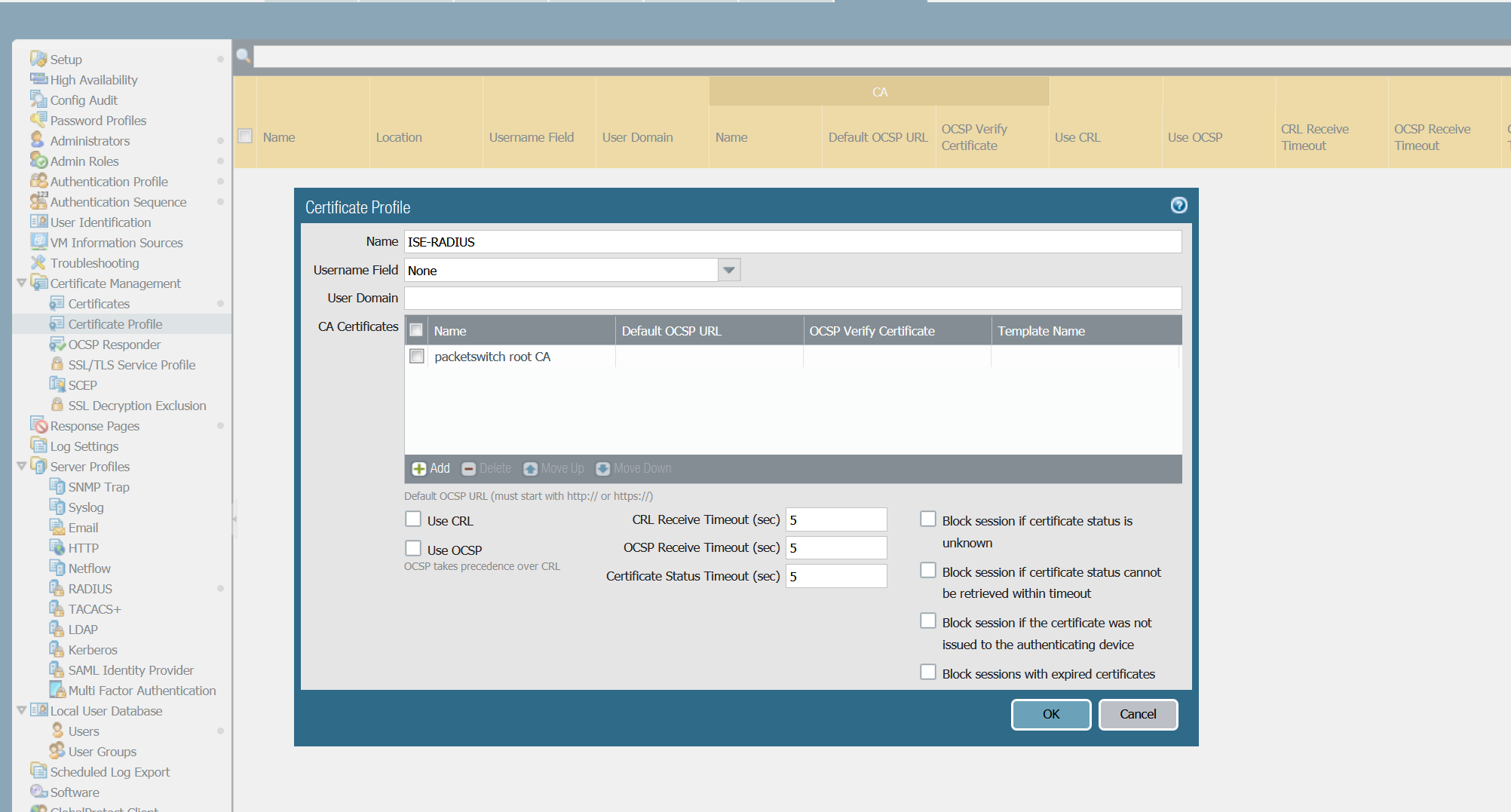
Step 6 - Create a Certificate Profile
Create a Certificate Profile and add the Certificate we created in the previous step.
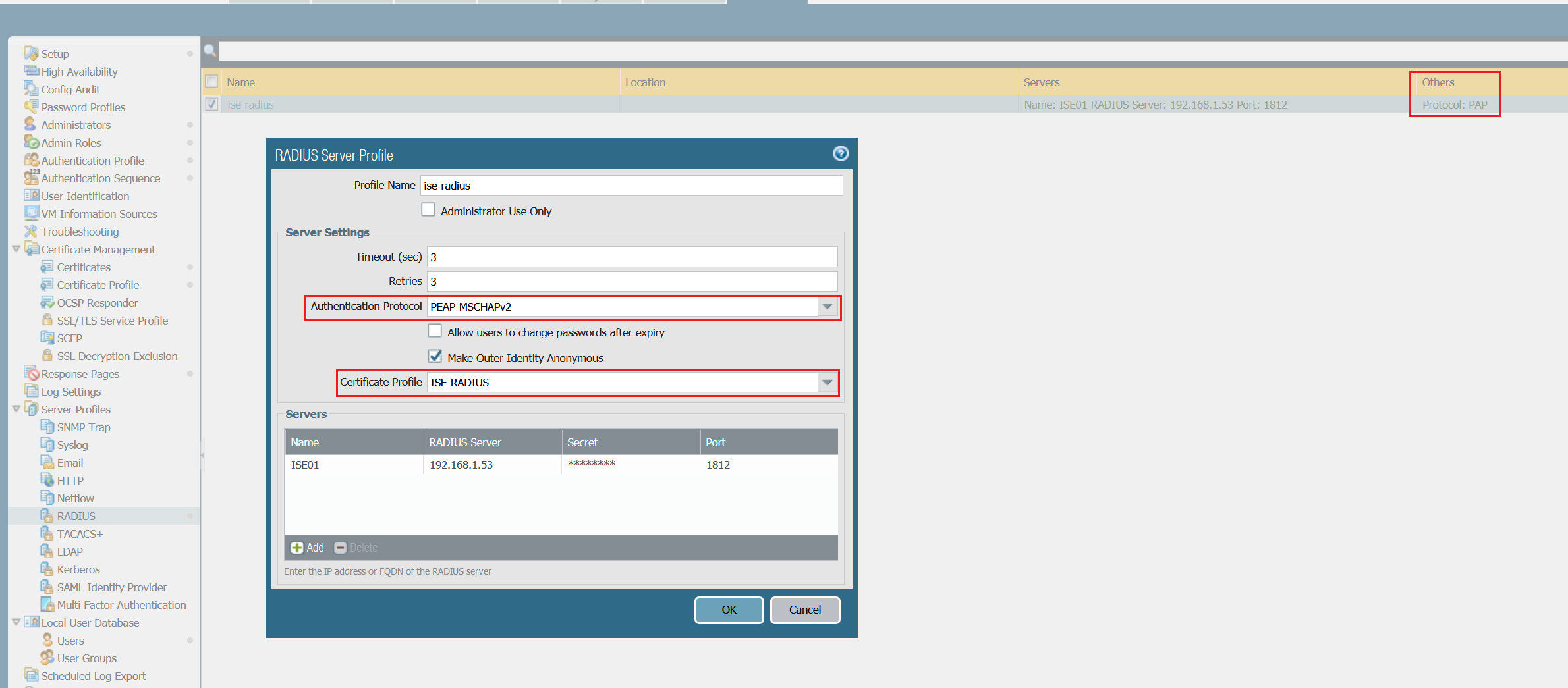
Step - 7 Configure Radius
Let's configure Radius to use PEAP instead of PAP.
Verification
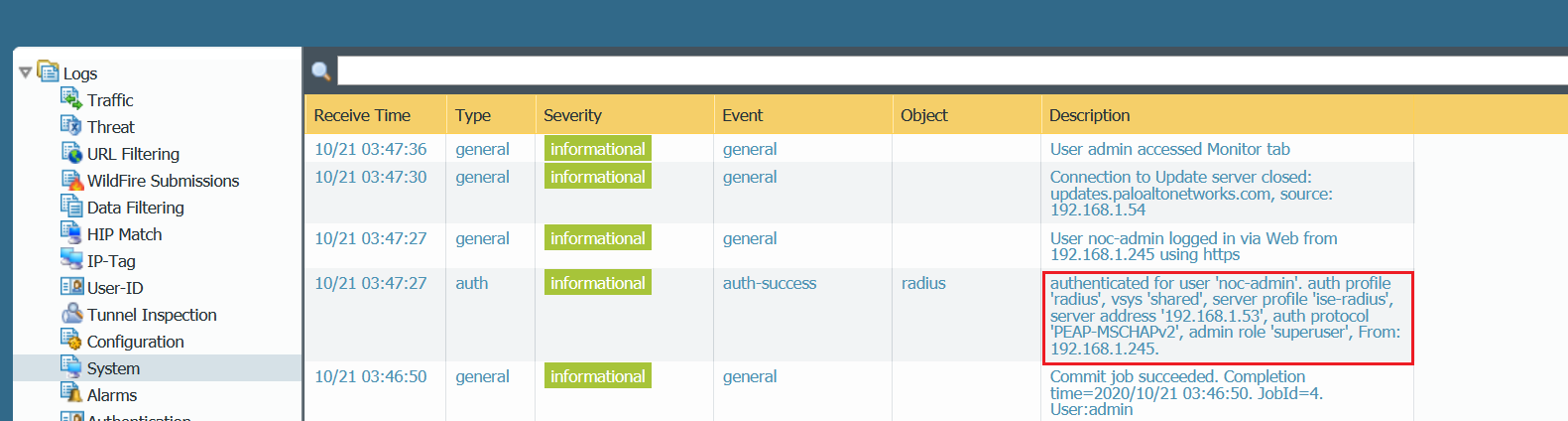
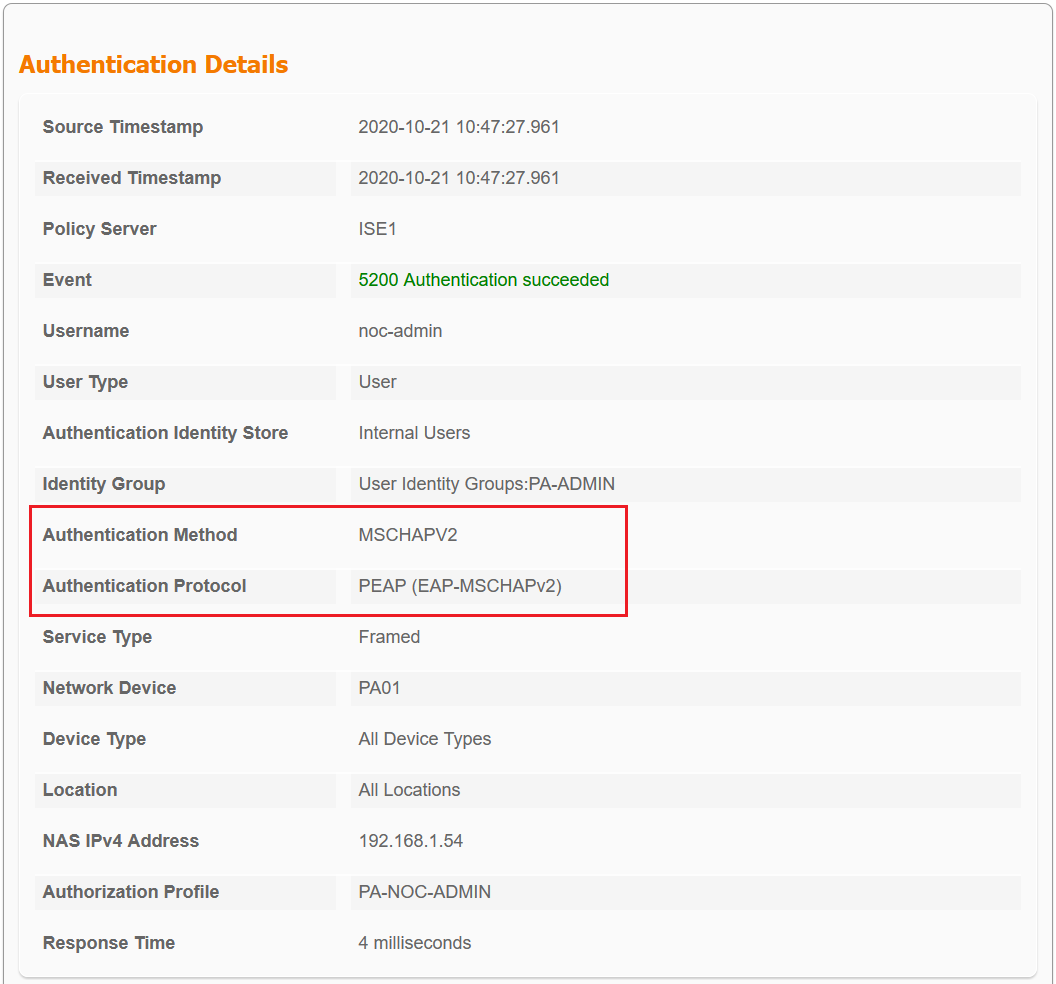
As you can see above that Radius is now using PEAP-MSCHAPv2 instead of PAP.
You can also verify Radius using the CLI
- You can use the command
test authentication authentication-profile radius username noc-admin passwordto test Radius.
admin@PA-VM> test authentication authentication-profile radius username noc-admin password
Enter password :
Target vsys is not specified, user "noc-admin" is assumed to be configured with a shared auth profile.
Egress: No service source route is set, might use destination source route if configured
Test authentication to RADIUS server 192.168.1.53:1812 for user: "noc-admin" (with anonymous outer id) using protocol: PEAP with MSCHAPv2
Successful EAPOL auth.
PaloAlto-Admin-Role: 'superuser'
Authentication succeeded against RADIUS server at 192.168.1.53:1812 for user "noc-admin"
Do post allow list check after successful authentication...
name "noc-admin" is in group "all"
Authentication succeeded for user "noc-admin"2. You can also check mp-log authd.log log file to find more information about the authentication.
admin@PA-VM> tail mp-log authd.log
2020-10-21 04:59:13.081 -0700 debug: pan_auth_response_process(pan_auth_state_engine.c:4286): auth status: MS CHAPv2 error "authentication failure"
2020-10-21 04:59:13.081 -0700 debug: pan_auth_incr_failed_attempt(pan_authd_db.c:171): increase failed attempt for user: noc-user
2020-10-21 04:59:13.082 -0700 debug: pan_auth_response_process(pan_auth_state_engine.c:4465): Authentication failed: <profile: "radius", vsys: "shared", username "noc-user">
2020-10-21 04:59:13.082 -0700 debug: finiCfg(pan_auth_eapol.c:1627): (AId:6885965566385848335) finiCfg().
2020-10-21 04:59:13.082 -0700 EAPOL has 0 objs now (-)
2020-10-21 04:59:13.082 -0700 debug: pan_auth_radius_eapol_cb(pan_auth_service_handle.c:1488): auth_svr_set_prot_spec_data(NULL) eapol ctxt for entry 4
2020-10-21 04:59:13.082 -0700 EAPOL eloop done (0)
2020-10-21 04:59:13.083 -0700 EAPOL eloop waiting (0)
2020-10-21 04:59:13.083 -0700 failed authentication for user 'noc-user'. Reason: Invalid username/password. auth profile 'radius', vsys 'shared', server profile 'ise-radius', server address '192.168.1.53', auth protocol 'PEAP-MSCHAPv2', From: 192.168.1.245.
2020-10-21 04:59:13.083 -0700 debug: _log_auth_respone(pan_auth_server.c:268): Sent MSCHAPv2_ERROR_AUTHENTICATION_FAILURE auth response for user 'noc-user' (exp_in_days=-1 (-1 never; 0 within a day))(authd_id: 6885965566385848335)Thank you for reading. As always your comments and feedbacks are always welcome






