In this blog post, we'll explore the step-by-step process of configuring Active Directory (LDAP) integration in Palo Alto. This configuration is particularly useful when you want to enable authentication for firewall administrators and VPN users by using their Active Directory credentials.
Before we dive in, let's take a moment to understand the relationship between Active Directory and LDAP. Active Directory is a Microsoft directory service that manages user accounts and resources in a network, while LDAP (Lightweight Directory Access Protocol) is a protocol used for accessing and maintaining directory information.
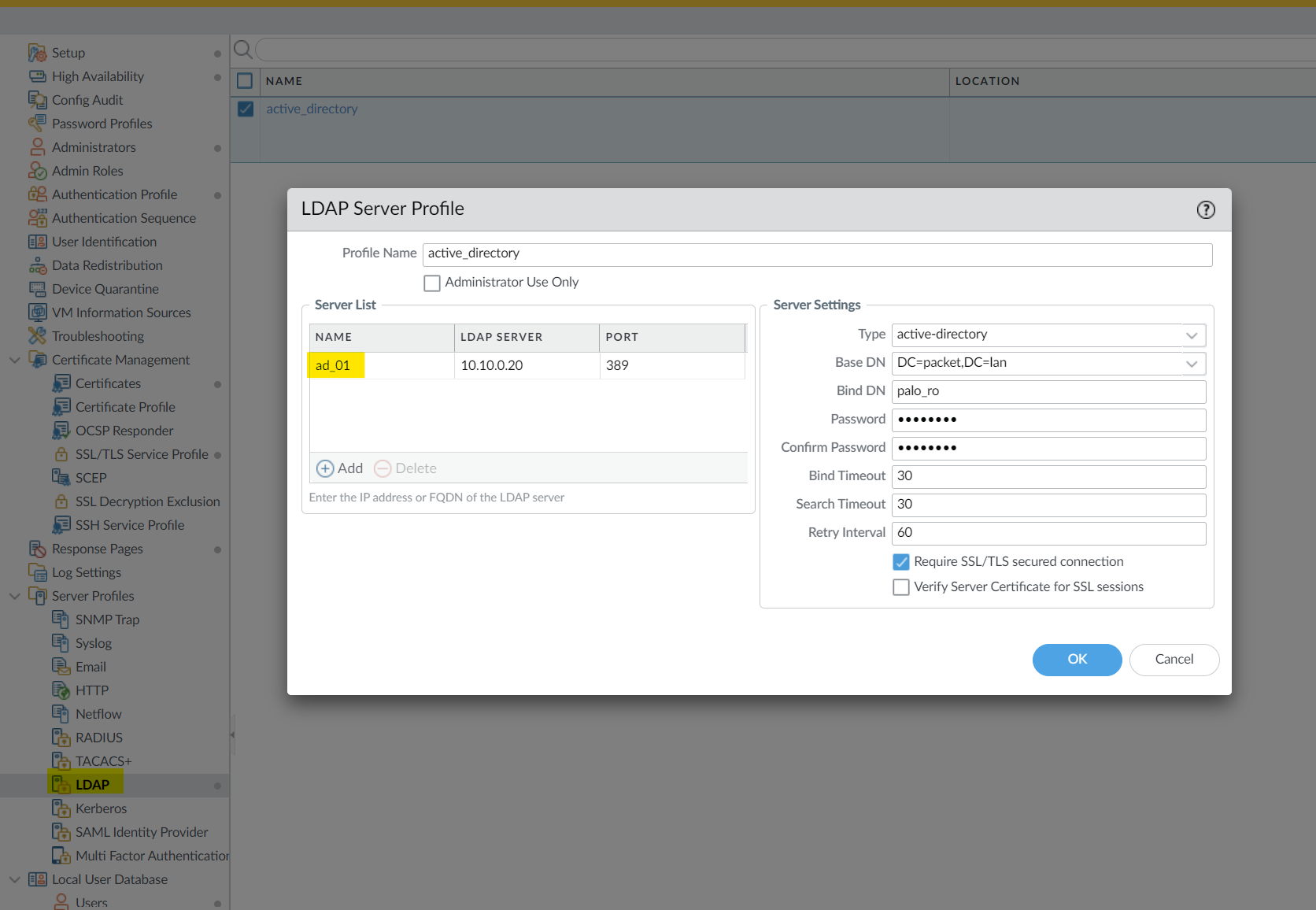
Add an LDAP Server Profile
Navigate to Device > Server Profiles > LDAP and create a new profile with the following.
- Enter a Profile Name to identify the server profile.
- Add the LDAP servers (up to four). For each server, enter a Name, LDAP Server IP address, and server Port (default 389).
- Specify the Base DN and Bind DN along with the password. The Bind DN account must have permission to read the LDAP directory.
- If you want the endpoint to use SSL or TLS for a secure connection, enable the option to Require an SSL/TLS secured connection (enabled by default).
What Exactly is the Base DN?
If you're configuring your Palo Alto firewall to talk to your Active Directory through LDAP, you'll need to tell it where to start looking for user accounts and other information. This starting point is called the Base DN.
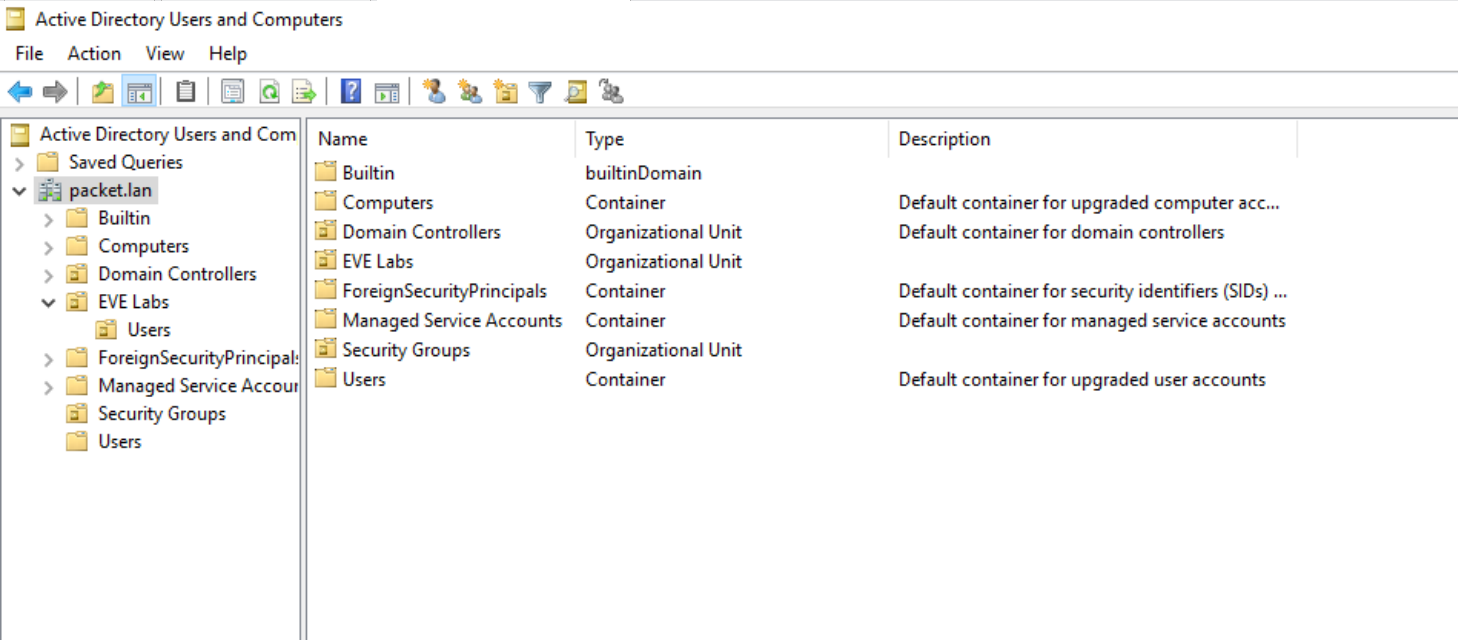
To figure out your Base DN from the screenshot, you'd look at your domain name, which here is packet.lan. Your Base DN turns into DC=packet,DC=lan
If you need to get more specific, say just the users, then your Base DN would include the folder for users, like this: OU=Users,DC=packet,DC=lan. That's like saying, "Start looking in the Users folder of the packet.lan domain."
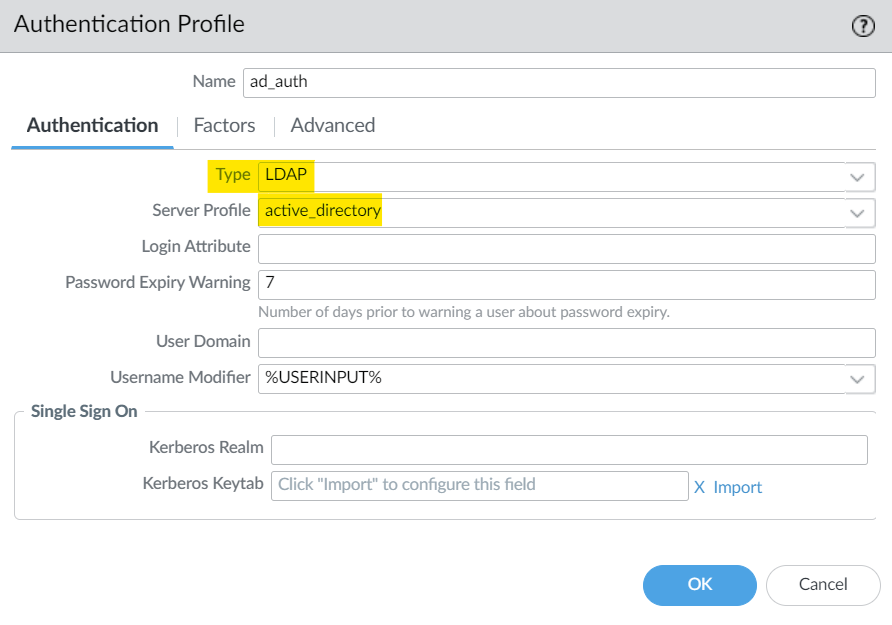
Authentication Profile
The final step is to assign the Server Profile we just created to an Authentication Profile. An authentication profile defines the authentication service that validates the login credentials.
Testing and Verification
The test authentication feature enables you to verify whether the firewall can communicate with the authentication server specified in an authentication profile and whether an authentication request succeeds for a specific user.
admin@palo-01(active)> test authentication authentication-profile ad_auth username max password
Enter password : admin@palo-01(active)> test authentication authentication-profile ad_auth username max password
Enter password :
Target vsys is not specified, user "max" is assumed to be configured with a shared auth profile.
Do allow list check before sending out authentication request...
name "max" is in group "all"
Authentication to LDAP server at 10.10.0.20 for user "max"
Egress: 10.10.20.34
Type of authentication: GSSAPI
Starting TLS at ldap://10.10.0.20:389
Starting TLS succeeded
Succeeded to create a session with LDAP server
DN sent to LDAP server: CN=max,OU=Users,OU=EVE Labs,DC=packet,DC=lan
User expires in days: never
Authentication succeeded for user "max"Parse error for maxPwdAge attr search
Parse error for maxPwdAge attr search
Authentication failed against LDAP server at 10.10.0.20:389 for user "max"In case you get the error Parse error for maxPwdAge attr search, please ensure that the Base DN you specified is in the correct format such as DC=packet,DC=lan