I've been following IP Fabric for some time now, checking out their updates and reading their blog posts. It made me curious to want to give their platform a try myself. So, I did just that and thought it'd be helpful to share my thoughts and experiences with you.
If you're curious about IP Fabric too, they offer a 90-day lab license, which is a great way to get hands-on with the platform. The nice people over at IP Fabric set me up with a trial license and I found the setup process to be very straightforward. In fact, it took me less than an hour to get everything up and running.
What we will cover?
- What is IP Fabric?
- Installation
- Automated Network Discovery
- What is a Snapshot?
- Topology Visualization
- Intent-based Verification
- Compliance and Security Checks
- Other Useful Features
- Closing thoughts
What is 'IP Fabric Automated Network Assurance Platform'?
IP Fabric is a platform designed for automated network assurance. It aims to provide network engineers with a comprehensive understanding of their network infrastructure through automated network discovery, verification, and documentation. This helps in identifying inconsistencies, compliance issues, and potential risks within the network infrastructure.
The platform supports a wide range of vendors, including but not limited to Cisco, Juniper, Palo Alto, Arista, F5 etc. It offers features such as.
- Automated Network Discovery - IP Fabric automatically discovers all devices and their configurations across the network.
- Topology Visualization - It provides a visual representation of the network topology, making it easier to understand the relationships and dependencies between devices.
- Intent-based Verification - The platform can verify that the network is operating as intended, based on predefined policies and configurations.
- Compliance and Security Checks - IP Fabric can automate the process of ensuring the network complies with internal policies and industry standards
- Change Management - It can track changes in the network over time, helping in troubleshooting and understanding the impact of modifications made to the network.
It would definitely make things clearer to see or visualize how all these features work, right? So, let's take a closer look at each one of them.
Installation
As I mentioned before, getting IP Fabric up and running is pretty smooth, and there's a great video guide that walks you through how to get started. First, you'll need to get in touch with the team to request a trial or lab license. They'll send you a link to download the OVA image.
After you've downloaded the OVA image, load it into your virtual machine tool (I used VMware Workstation) and power it on. You'll then set up basics like the IP address, DNS, and CLI admin credentials.
Once the initial setup is done, just open a browser and go to https://YOUR_IP:8443. Here, you'll create a local admin account for the GUI. Log in with this new account, upload the license file they provided, and you're ready to go.
Automated Network Discovery
After you've set up IP Fabric and logged into the GUI, you're ready to start with automated network discovery. So, what does this mean? It's all about letting IP Fabric get to know your network (after all, that's what we are after right?)
First up, IP Fabric needs to know how to access your devices. It only needs read access, so there's no need for full admin rights. If you're using TACACS+, for example, a read-only (RO) account will do just fine. You also have the flexibility to use different credentials for different parts of your network. In my situation, I had two separate lab networks, 10.10.50.0/24 and 10.10.20.0/24, and I used different credentials for each. This setup lets IP Fabric know it should treat these subnets separately.
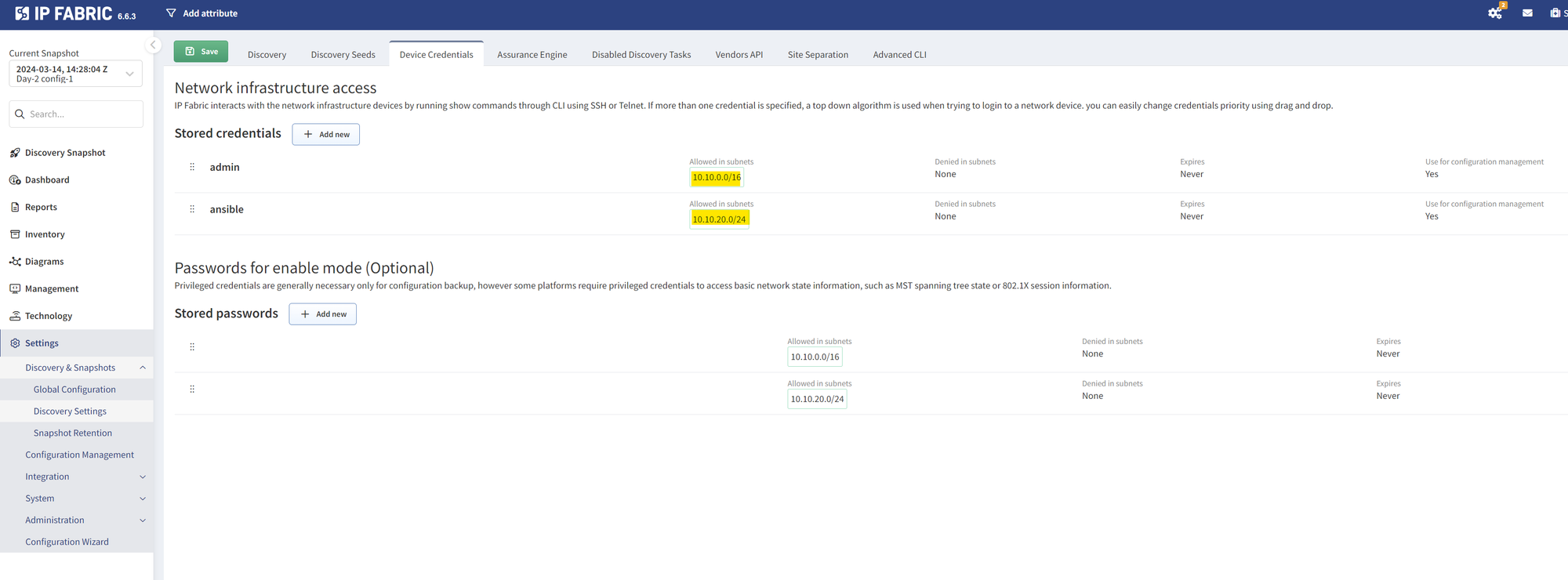
Next, you'll head over to the discovery section. Here, you get to fine-tune how IP Fabric explores your network. You can tell it which IP networks to skip and which ones it should discover. You can also start the discovery with a "seed" — this is a starting point for IP Fabric. From this seed, if IP Fabric can log in and read data (think ARP records, CDP, LLDP, routing protocols, and more), it then knows where to go next to gather the information it needs. This way, it systematically works through your network, learning everything it can.
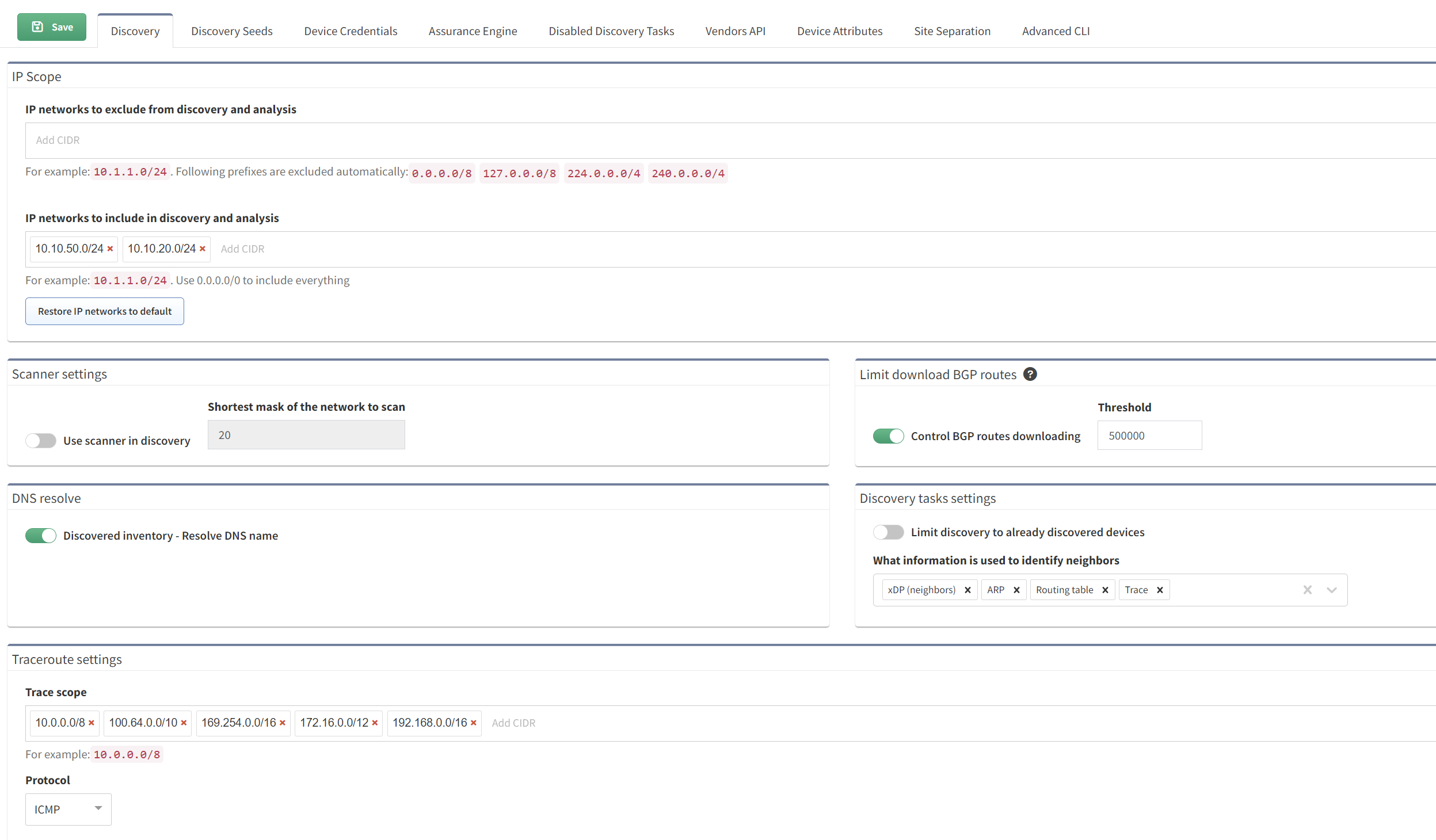
It took me just a few minutes for the discovery to complete (of course this depends on how big is your network)
Here is a really good guide on how network discovery works and how to troubleshoot if you have any issues.
Snapshots
Before diving into the specifics of IP Fabric, let's talk about an essential feature, Snapshots. Think of a snapshot as a photo capturing the state of your network at any given moment. If you're taking these snapshots daily, you're essentially keeping a detailed diary of your network. This allows you to look back in time, see historical information, and pinpoint when and how network changes occurred.
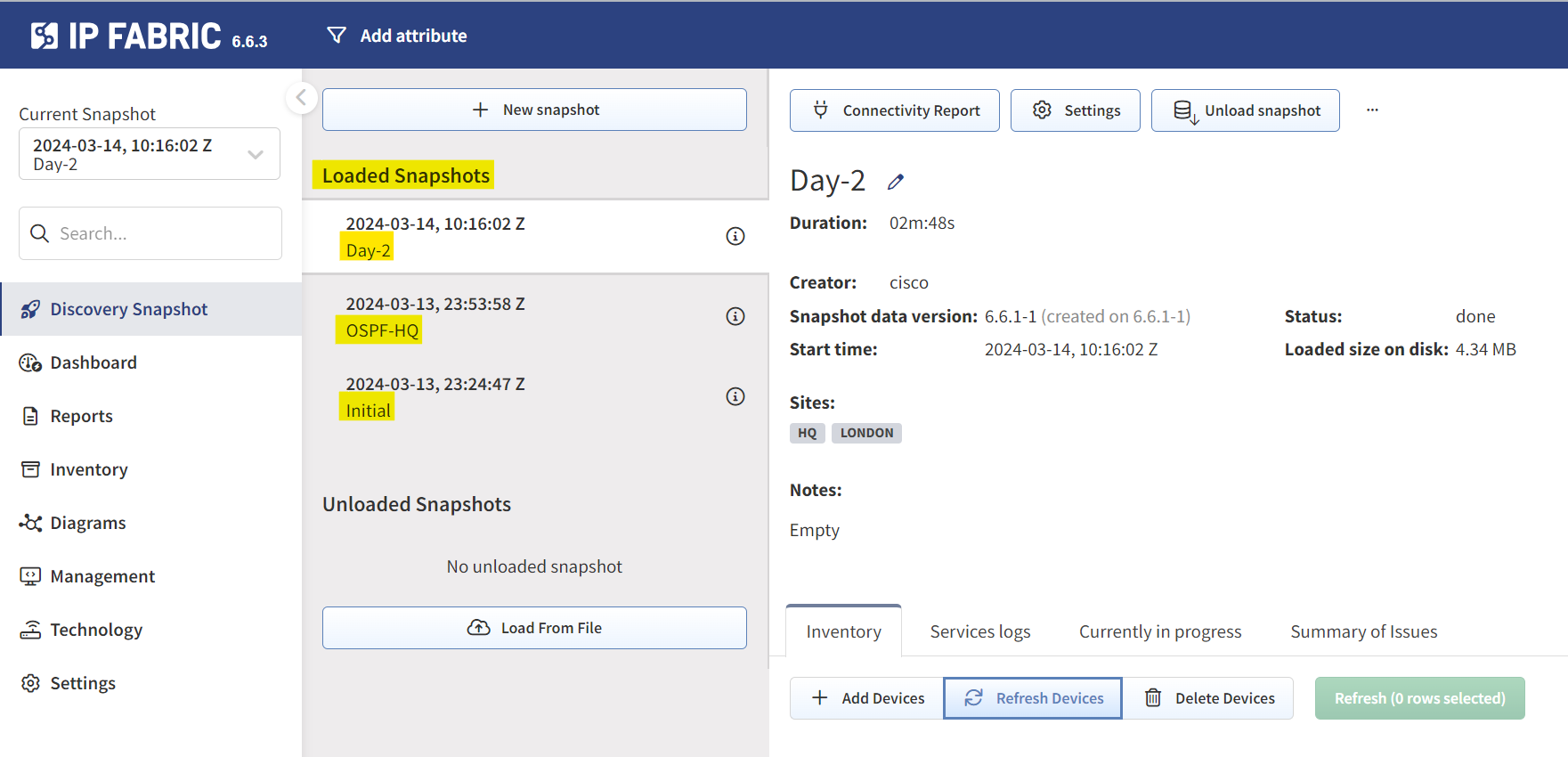
A quick note on Sites
A 'Site' is essentially a separate collection of devices, which could represent a branch, a shop, a campus, or any other logical grouping. For my use case, I organized devices based on their hostnames, using a naming convention that includes a site identifier at the beginning of each hostname.
Within IP Fabric, you can use regular expressions (RegEx) to automatically group devices into sites based on these identifiers. For instance, using a capture group like (^\w+) in the RegEx helps in extracting the site identifier from the hostname. So, a device named HQ-router_01 would automatically be grouped under the 'HQ' site as shown below.
(^\w+) matches the beginning of a string and captures one or more word characters (like letters, digits, or underscore) that appear right at the start. So, if you have something like HQ-router_01, this expression would match and capture HQ before the dash, identifying it as the site identifier in this context.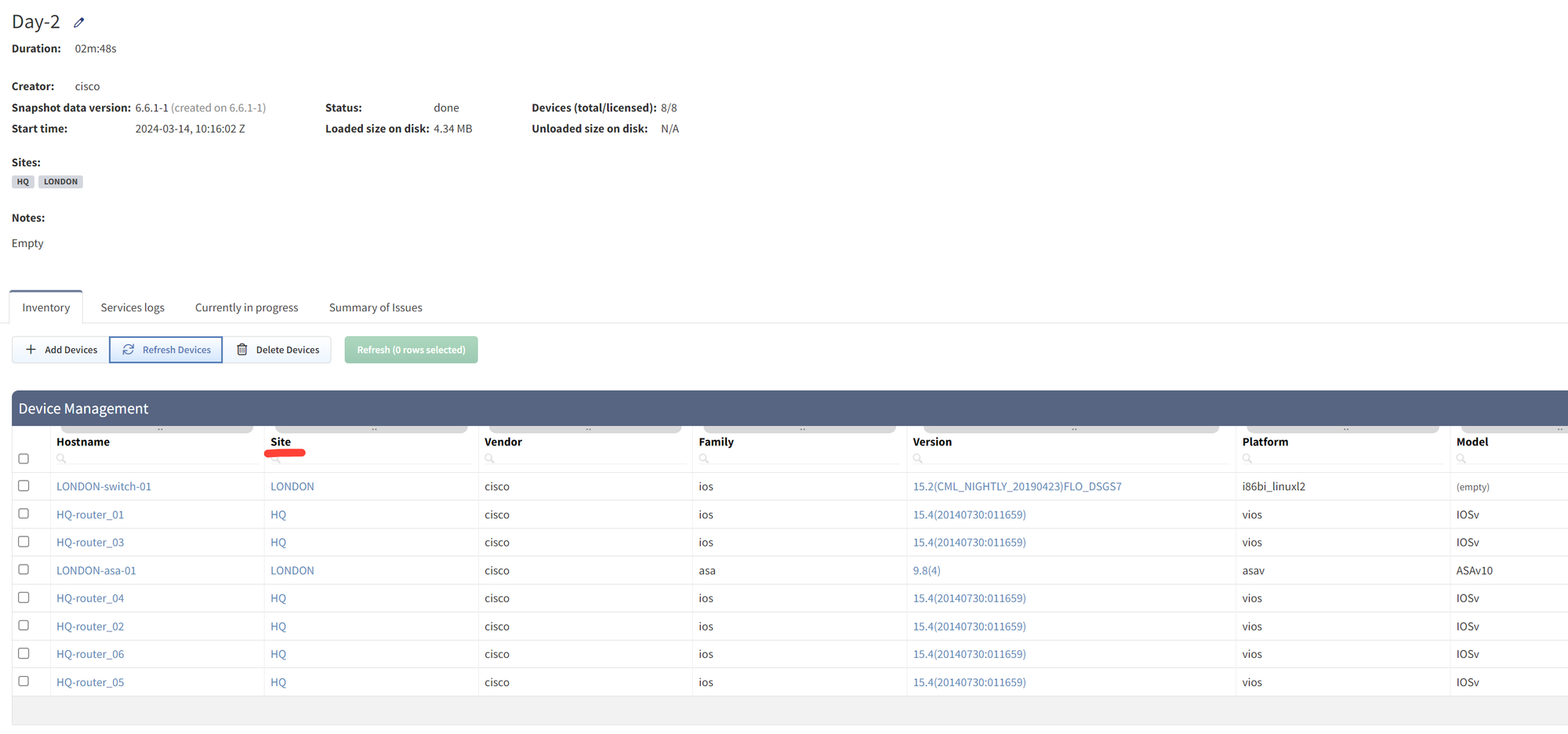
Topology Visualization
In each snapshot, IP Fabric goes beyond just capturing data, it actively models your network's forwarding and policy behaviour. It does this by analyzing configurations and outputs from various show commands such as routing protocols or how Spanning Tree Protocol (STP) neighbours are connected, IP Fabric provides a comprehensive view.
This means you're not just seeing your network as a static set of devices and connections, you're getting a dynamic, in-depth look at how information flows through it and how policies are applied. This full picture of your network helps in making informed decisions and troubleshooting.
In my lab, which includes two sites, HQ and London, I have several devices. (my lab is a mess). If I navigate to the Diagrams section, I can visually separate and understand the network structure for each site. IP Fabric allows for filtering based on sites, routing, or switching, making it easier to focus on specific areas of the network.
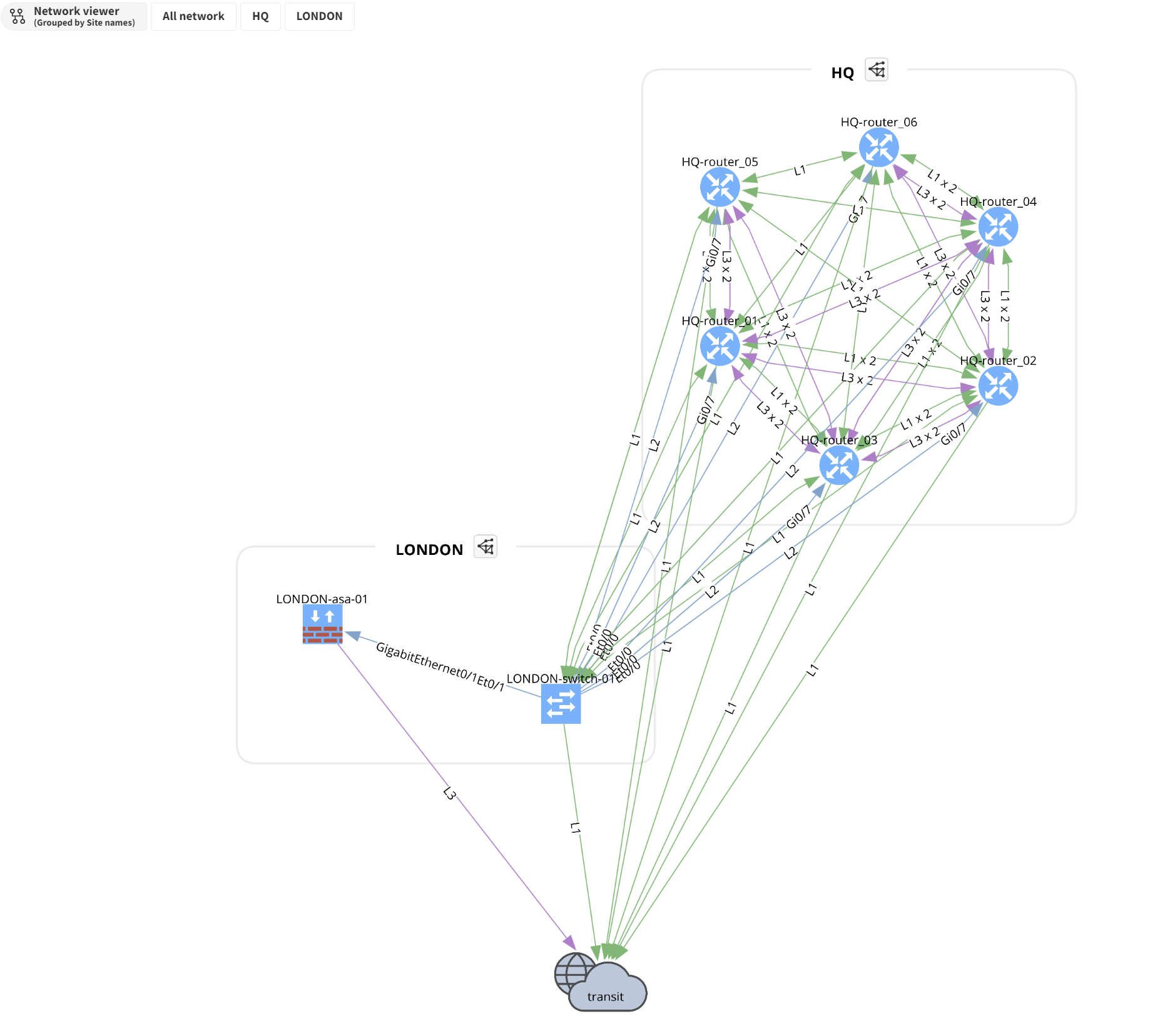
What's even more impressive is the ability to visualize end-to-end paths. By simply providing a source and destination IP, IP Fabric shows how data travels across the network. This feature is incredibly useful for troubleshooting and understanding how your network handles traffic.
Intent-based Verification
This feature is, by far, my favourite. So, what exactly is Intent-based Verification? It does exactly what it sounds like. You set up rules that reflect your network's intended state or policies, and if anything doesn't match up, IP Fabric highlights these discrepancies for you.
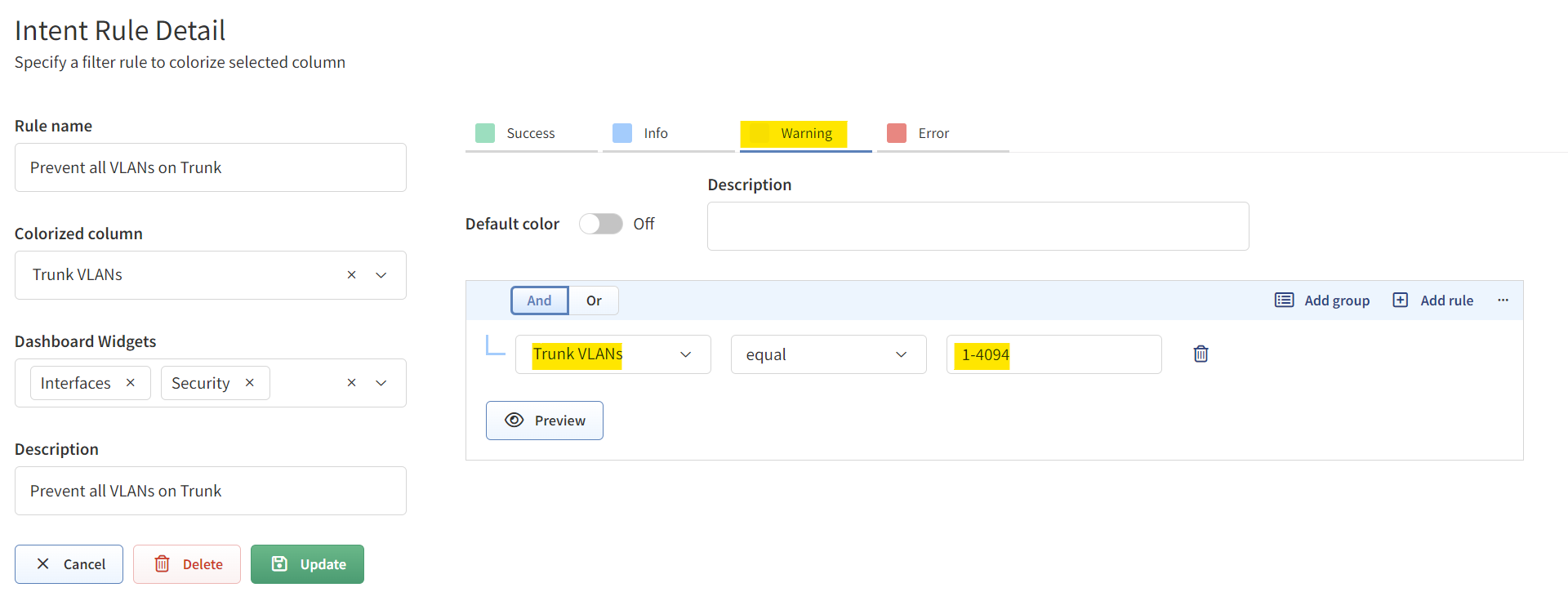
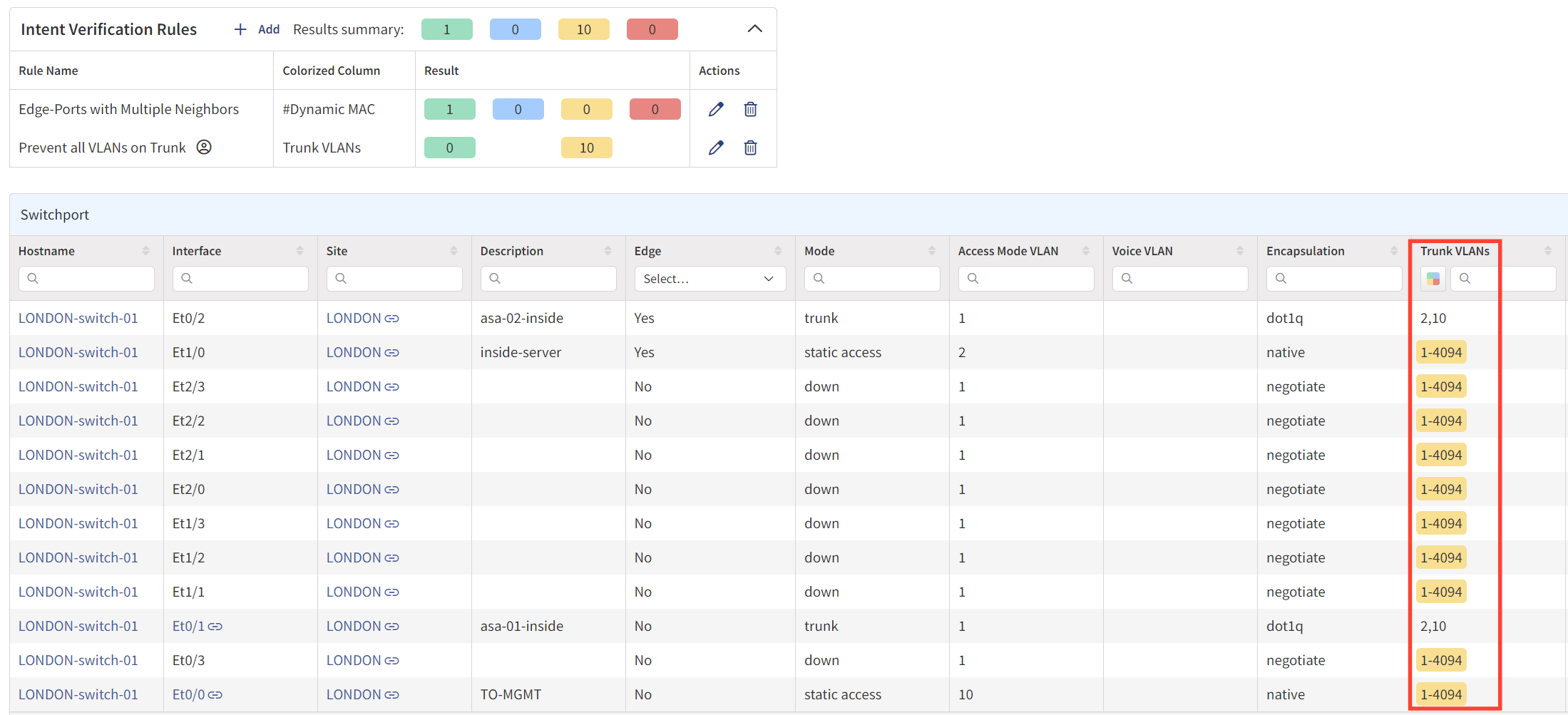
Let's go through a simple example to illustrate how useful this can be. Let's say our network security guidelines dictate that we shouldn't allow all VLANs on a trunk port. However, in reality, it's easy to overlook such guidelines. There might be instances where all VLANs are unintentionally allowed on a trunk port, and we never go back to correct this oversight.
Traditional Network Management Systems (NMS), which rely on SNMP, might not flag this issue, allowing it to go unnoticed. In IP Fabric, all you need to do is navigate to Technology > Interfaces > Switchport and set up an intent rule. If the 'Trunk VLANs' column shows the value 1-4094, it means all VLANs are allowed, and IP Fabric will highlight these rows to indicate non-compliance with our guidelines.
Another scenario could involve AAA configurations. Say our policy requires a 'LOCAL' backup authentication method in case the primary Radius server is unreachable. How many times have we found ourselves locked out because of this oversight? With Intent-based Verification, you can easily set up a rule to flag any device missing this crucial backup method.
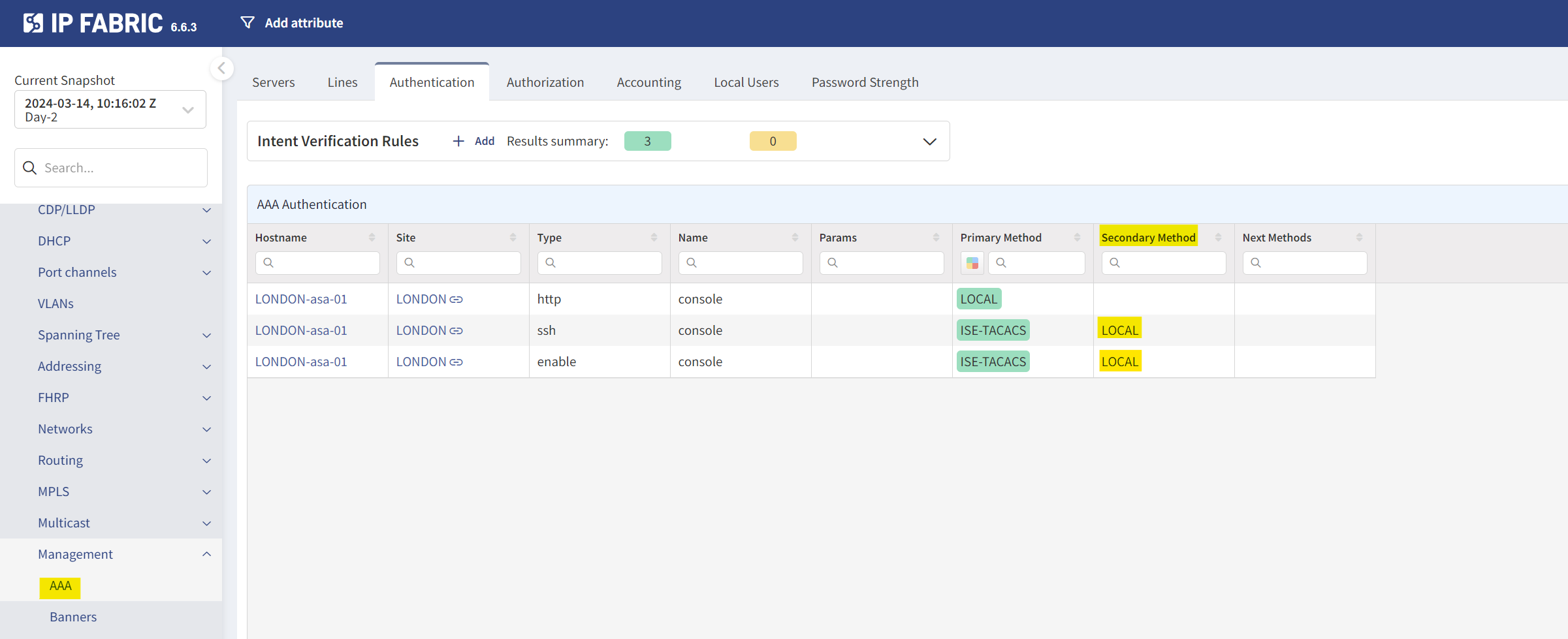
The possibilities here are virtually endless. You can use IP Fabric to monitor a wide array of configurations and policies specific to your network's needs. Although I wanted to set up a rule to check for OSPF Authentication and ensure it's enabled across the network, this option wasn't available at the time of writing. Still, the flexibility and potential of Intent-based Verification in keeping your network aligned with best practices and security guidelines is truly impressive.
Compliance and Security Checks
I'll keep this part brief but focus on a couple of key points. IP Fabric does a great job scanning your network to keep you in line with the necessary standards. For example, it can check your devices against publicly available End-of-Life (EoL) data. If any of your devices need replacing, IP Fabric can flag it.
It doesn't stop there. IP Fabric also checks the version of the operating system your devices are running. This is super useful to ensure everything is up-to-date and secure.
I remember working in a place where we had to follow loads of compliance rules. Everything from ensuring all ports used 802.1X, to having an Access Control List (ACL) for SNMP. Just like we discussed in the Intent-based Verification section, if something in your network doesn't meet these standards, IP Fabric will flag it. This way, you're always in the know about where your network stands with compliance and security.
Other Useful Features
Saved Config Consistency
One handy feature I came across involves configuration management. Let me explain through a scenario that many of us might find relatable. There have been times when it was crucial to ensure our configurations were saved properly (as in running copy run start). Think about situations like a power down for a building. Despite our best efforts to save configurations after every change (using copy run start or wr), it's always a good practice to double-check.
IP Fabric offers a neat solution for this. It has a feature that can tell you whether or not your configurations have been saved. To put this to the test, I added a new address-object in an ASA but intentionally didn't save the configuration. When I went to Management > Saved Config Consistency in IP Fabric, it flagged this up. Not only does it alert you about unsaved configs, but you can also see what has changed.
LONDON-asa-01(config)# object network ANOTHER-DUMMY
LONDON-asa-01(config-network-object)# ho
LONDON-asa-01(config-network-object)# host 2.2.2.2
LONDON-asa-01(config-network-object)# end
LONDON-asa-01# 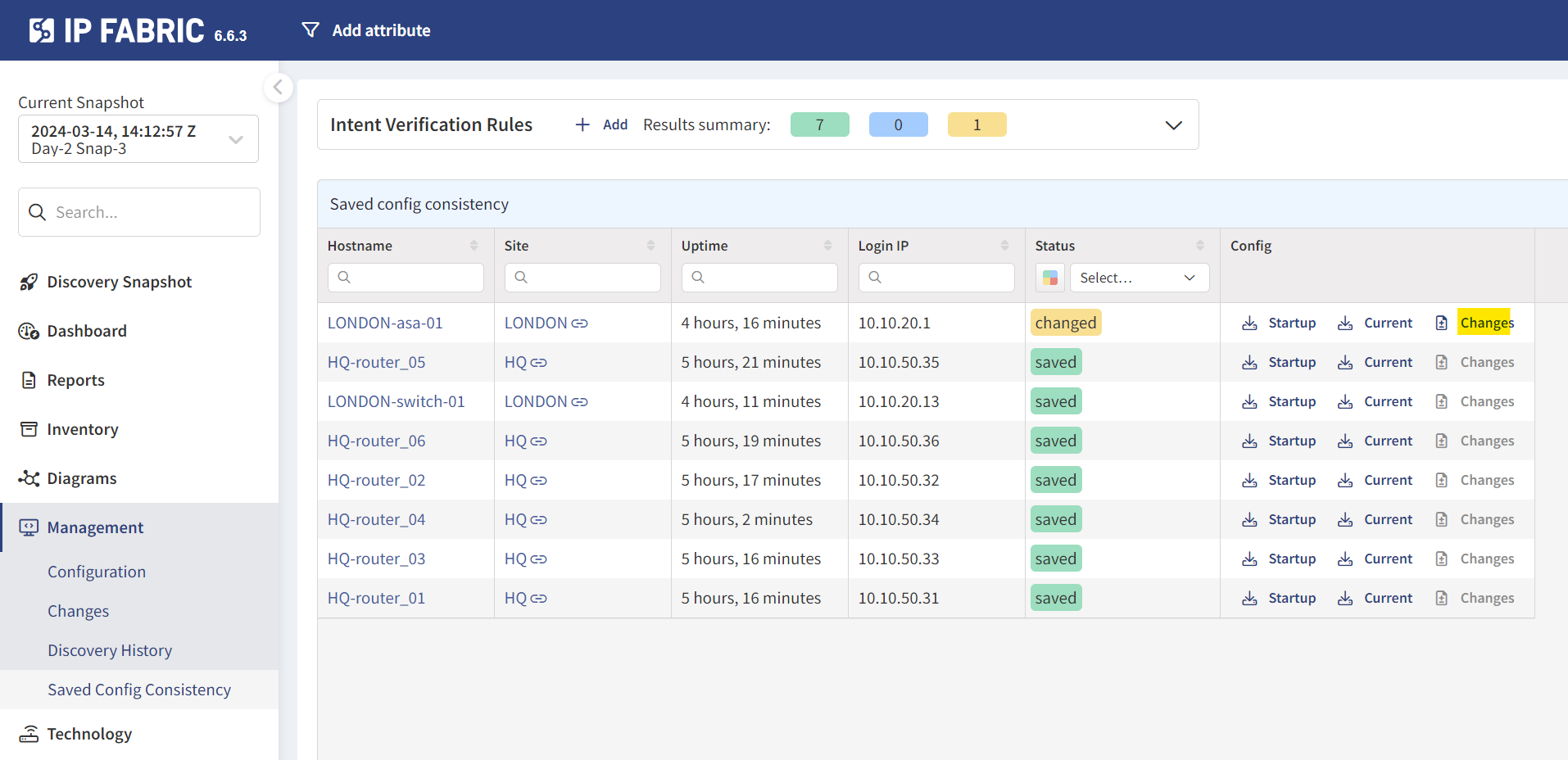

Configuration Backup
Surprisingly enough, it also backs up the configs during snapshots. This means you might not need to rely on a separate Network Configuration Manager (NCM) for backups.
However, I couldn't find a way to view the 'config diff' between two snapshots. This feature would be incredibly useful for quickly identifying what's changed in your network over time, I must be missing something here so, please let me know in the comments on how to do it.
Closing thoughts
That wraps up today's journey with IP Fabric. Given that I've only spent a few days getting to know the platform, it's possible I haven't covered everything there is to know. If you think there's something important I missed or if you have specific questions, please don't hesitate to let me know in the comments.