Overview
You can configure the Palo Alto Firewall to act as a DNS server. All the clients' DNS will point to the firewall’s interface IP. The firewall then sends the queries to the specified DNS servers. Palo Alto DNS proxy can be an alternative to having dedicated DNS servers within a branch office or remote sites. The firewall acts as a man-in-middle for the DNS queries.
Use Cases
You might think why would I ever want to do this? Why don't we just send the DNS queries directly to the DNS servers (Internal or public)? To answer these questions let's look at some of the use cases where the DNS proxy makes sense.
Suppose you have a very small site with just a single firewall and a bunch of users. It won't make sense to have a dedicated DNS server in the branch just for a few users. DNS Proxy can be extremely useful in this scenario where you can configure the firewall to be the DNS server and conditionally forward the queries to upstream DNS servers.
Ideally, you will want to send all the Internal queries to your DC/HQ and everything else to the Public DNS server such as 8.8.8.8 as shown below.
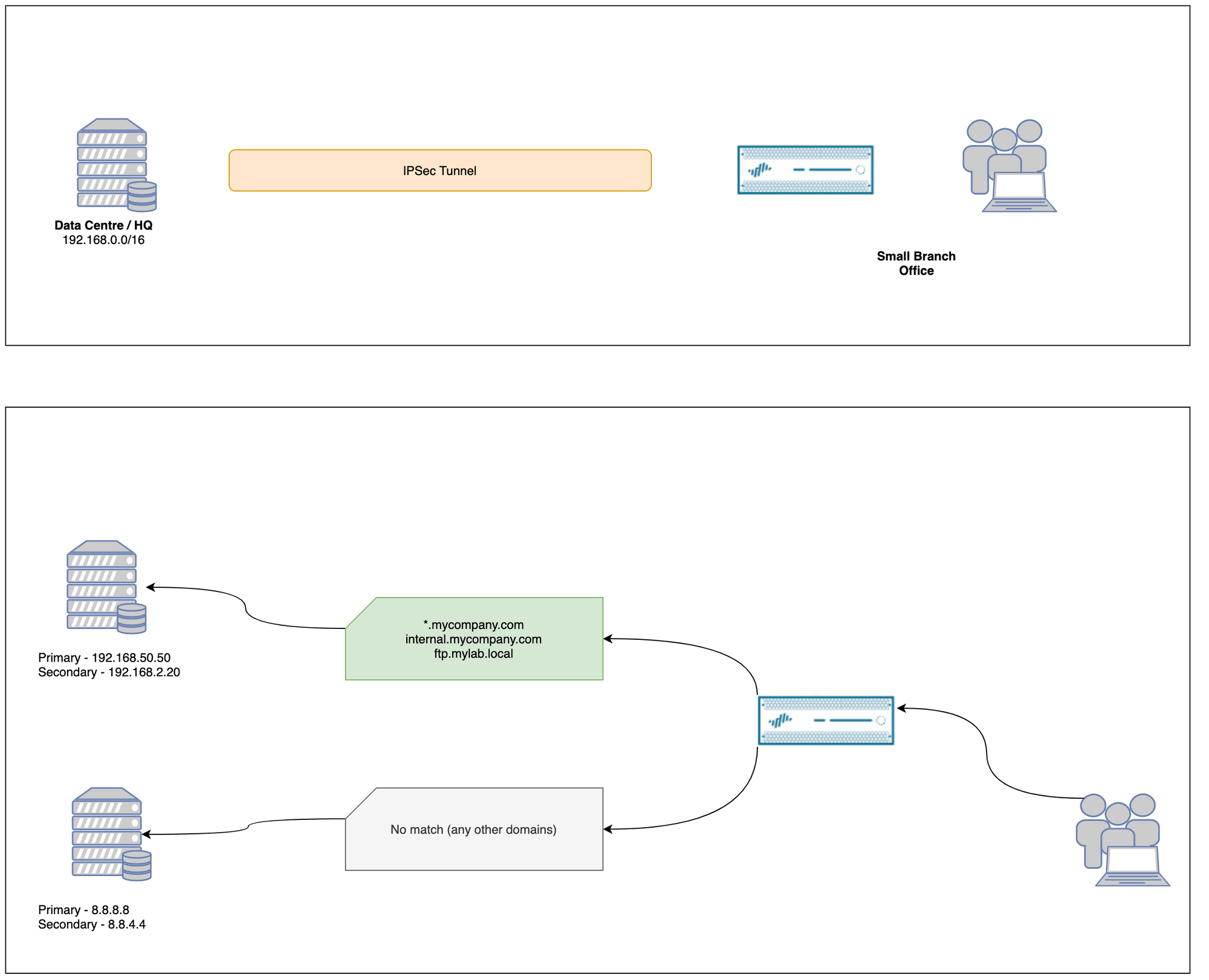
Even if the IPSec tunnel is down, at least the users can resolve public DNS queries using 8.8.8.8 instead of relying on the Internal DNS servers from the HQ.
Configuration
The configuration is very straightforward and requires just a few steps. The clients should point to Palo's interface IP as their DNS server. You can amend your DHCP scope setting to use the interface IP as the DNS server.
Enable DNS Proxy
Navigate to Network > DNS Proxy and Add a new proxy.
- Specify the default Primary and Secondary DNS servers
- Select the interfaces on which DNS proxy should be enabled. In the below figure the DNS proxy is enabled on interface ethernet 1/2
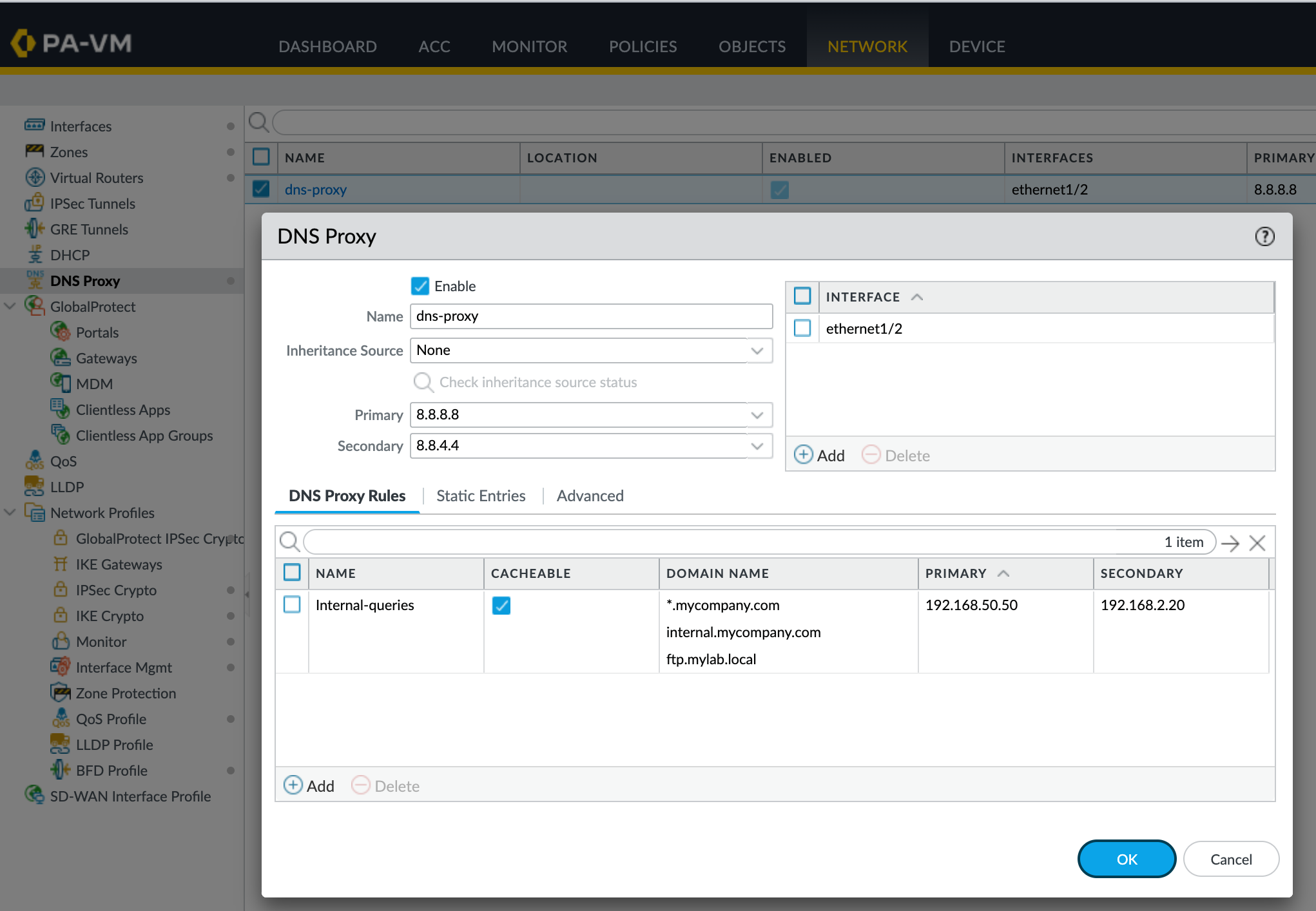
DNS Proxy Rules
DNS Proxy Rules allow you to specify domain names and corresponding primary and secondary DNS servers to resolve queries that match the rule. As shown in the above figure, we want to send specific DNS queries to the Internal DNS servers 192.168.50.50 and 192.168.2.20. If there is no match, the firewall will send the queries to the default DNS servers (8.8.8.8 and 8.8.4.4)
Static Entries
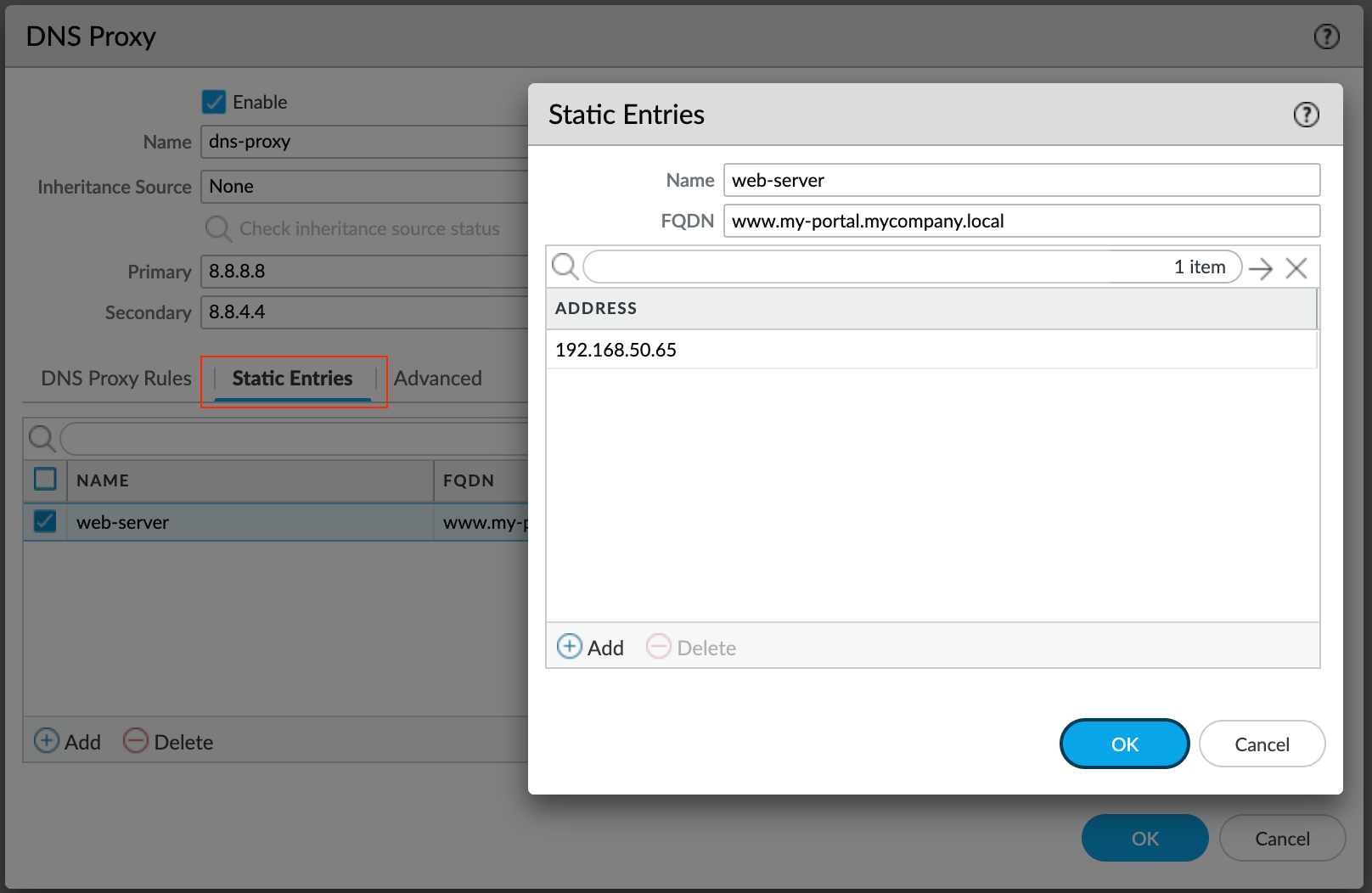
Static Entries allow you to configure static FQDN-to-IP address mappings that the firewall caches and sends to hosts in response to DNS queries.
The example below shows an example of a static entry. This can be useful for Guest Wi-Fi where the clients get public DNS servers but you want to resolve one or two internal domains such as a guest portal or captive portal FQDNs.
Clients in Multiple Interfaces
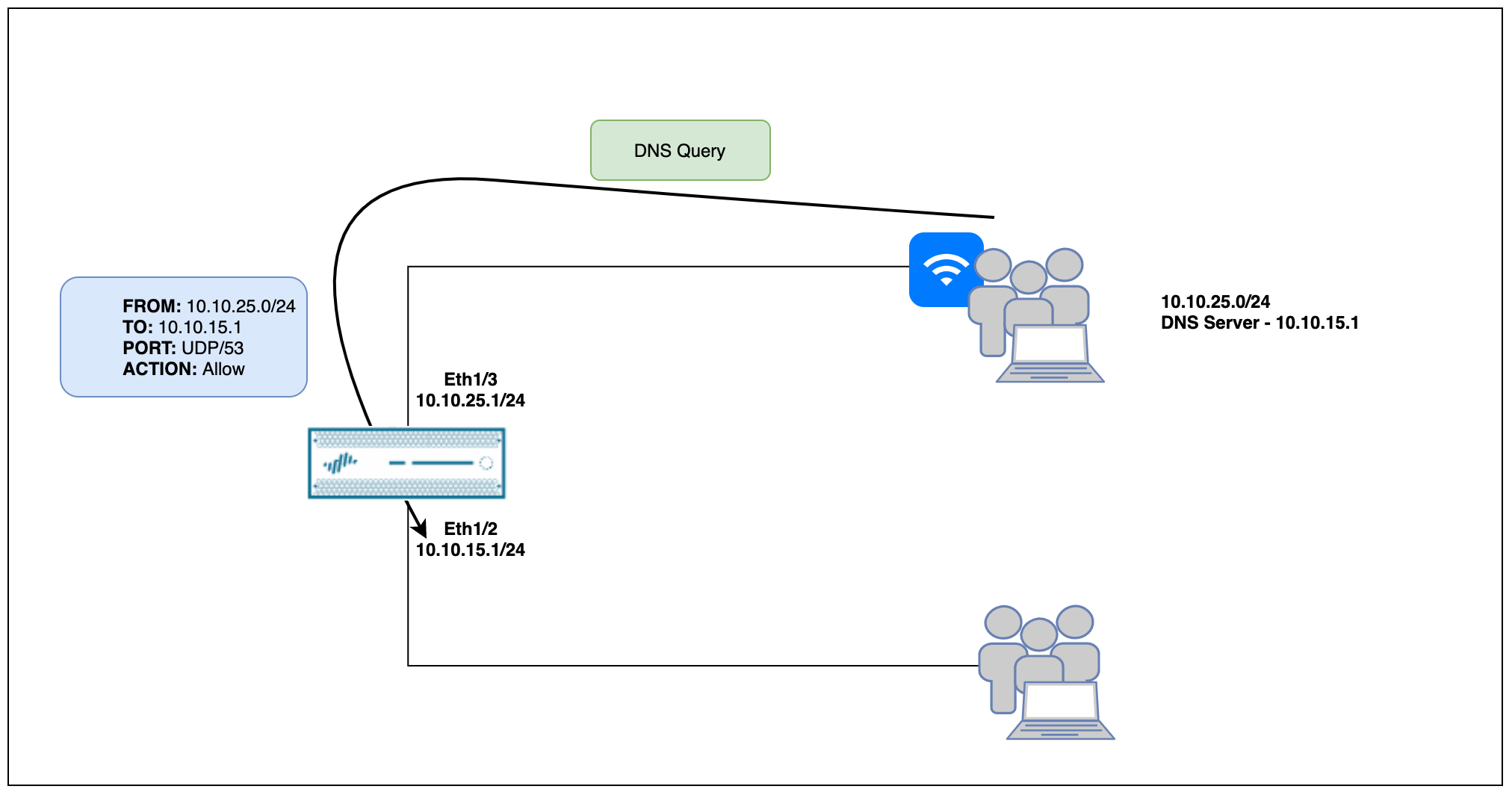
Let's say we have clients behind multiple firewall interfaces such as wired and wireless as shown above. Which interface IP should we choose as the DNS server?
- Two separate DNS IPs for respective clients, 10.10.15.1 for wired/inside clients and 10.10.25.1 for wifi clients.
- Use a single Interface IP as the DNS servers for all the clients.
Well, you can use either method. If you choose to use the latter one, make sure to create a Security Policy to allow the traffic from the client subnet to the interface IP. For example, let's say you want to use 10.10.15.1 as the DNS server IP for the clients behind the Eth1/3 interface, then the security policy should allow traffic from 10.10.25.0/24 to 10.10.15.1 on UDP/53.
Closing up
Palo Alto DNS proxy is a clever little tool which can help you where you don't have dedicated DNS servers or you want to maintain conditional rules based on domain names.
References