Hi all, welcome back to yet another Palo Alto Firewall blog. Have you ever wanted to load partial config from one Palo Alto Firewall to another or from a Firewall to Panorama and vice versa? There could be times when you just want to import all address objects from one Firewall to another, for example. We could do this in multiple ways, but there is a simple way of doing this. Let’s get into how you can achieve this with just a few steps.
To demonstrate this, I have a firewall and Panorama. On the firewall, there are a few address objects, address groups, and a security policy that I want to import into Panorama, inside a specific device group. Let’s walk through the steps.
- Export the configuration - Start by exporting the configuration from the firewall.
- Import it to Panorama - Next, import that configuration into Panorama.
- Identify the XPath of the objects - You'll need to find where the objects you want to copy are located in both the firewall and Panorama. Keep in mind, the XPath for these objects might be slightly different between the firewall and Panorama.
- Copy them over with a command - Finally, run a single command to copy the objects over to the Panorama.
Export the Configuration
In this section, let's look at how to export the configuration from the firewall.
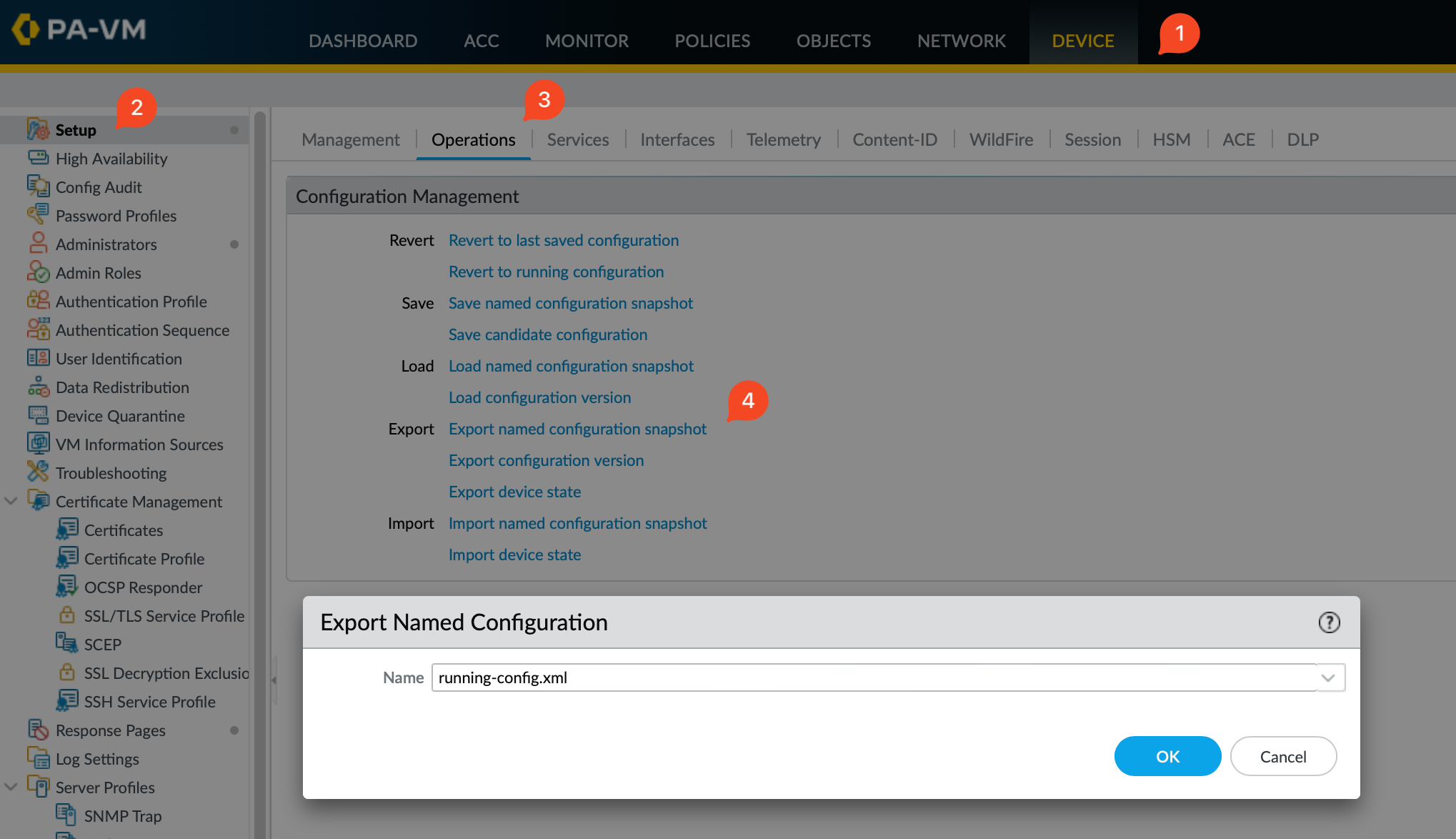
- Start by going to Device > Setup > Operations. Here, you’ll find the option 'Export named configuration snapshot'.
- Choose the 'running-config' from the list to export it to your laptop. I usually rename the file to the name of the firewall for easier identification. So, in this case, you would rename it to
site-01.xml.
Import the configuration to Panorama
After exporting your configuration from the firewall, the next step is to import it into Panorama. Here’s how you can do this.
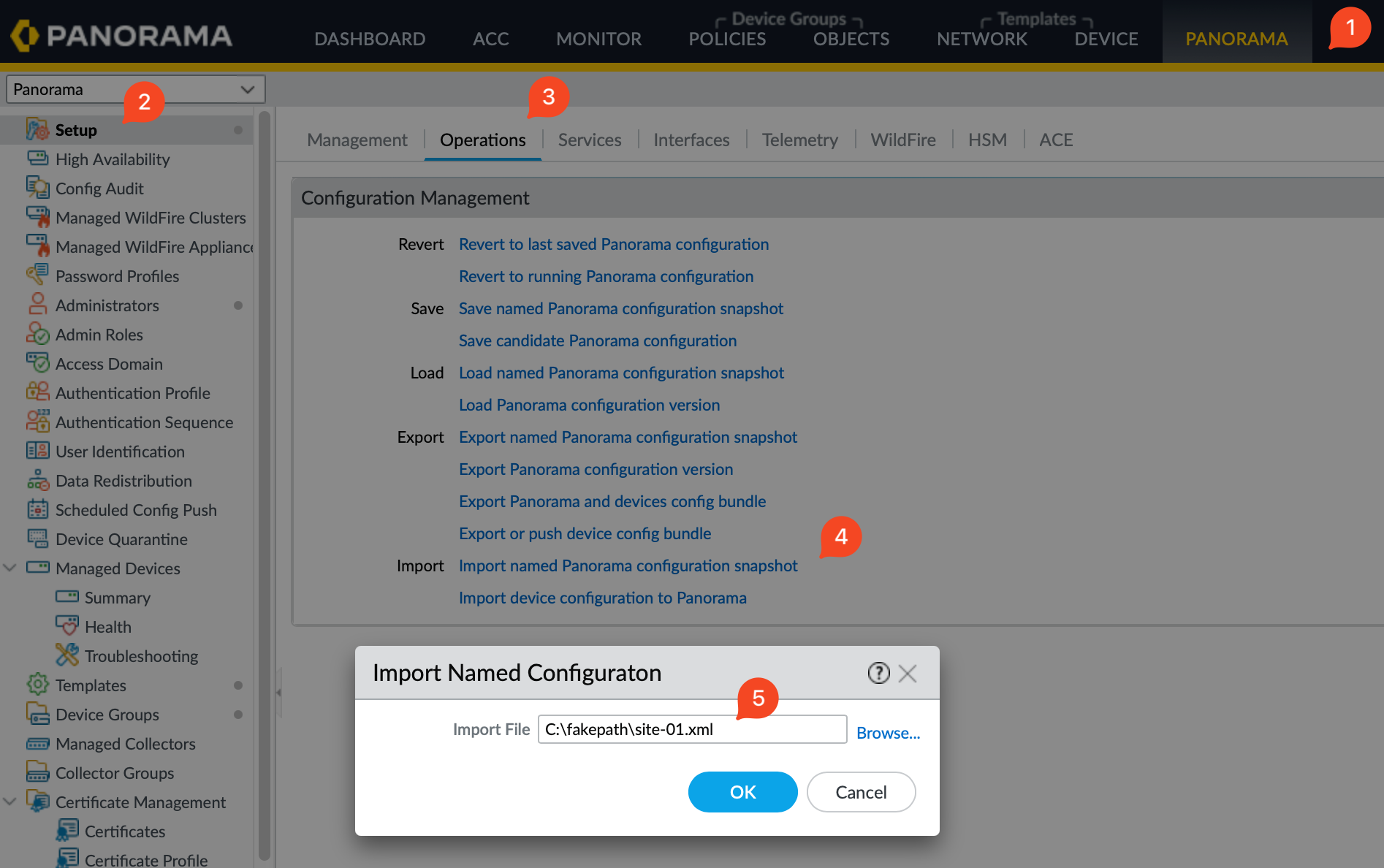
- On the Panorama interface, go to Panorama > Setup > Operations.
- Look for the option to 'Import a named configuration snapshot'. Click on the ‘Import’ option and a window will appear. Use the ‘Browse’ button to locate and select the configuration file you exported from your firewall, in this case,
site-01.xml - After selecting the file, click ‘OK’ to import it into Panorama.
Identify the XPath of the Objects
As you may already know, everything in Palo Alto firewalls is represented in an XML file. For our task, we need to copy all the address objects from the firewall and then paste them into Panorama. First, we need to find out exactly where these address objects are located, or in other words, what's their XPath. The XPath to these objects is slightly different between the firewall and Panorama.
- Use the XML API - The easiest way to find the path is to use the built-in XML API. Navigate to
https://<FIREWALL_IP>/apion your browser. - Browse through the paths - Once you access the API, browse through the paths until you reach the section for address objects. This will show you the exact XPath you need to reference these objects.
Remember, we need to repeat this process for address groups and security policies.
Firewall XPath
To find the XPath for configuration items using the XML API, start by selecting 'Configuration Commands' on the main page. Then navigate through the options until you reach the 'address' section. This may seem a bit complex at first, but with regular use, it becomes straightforward.
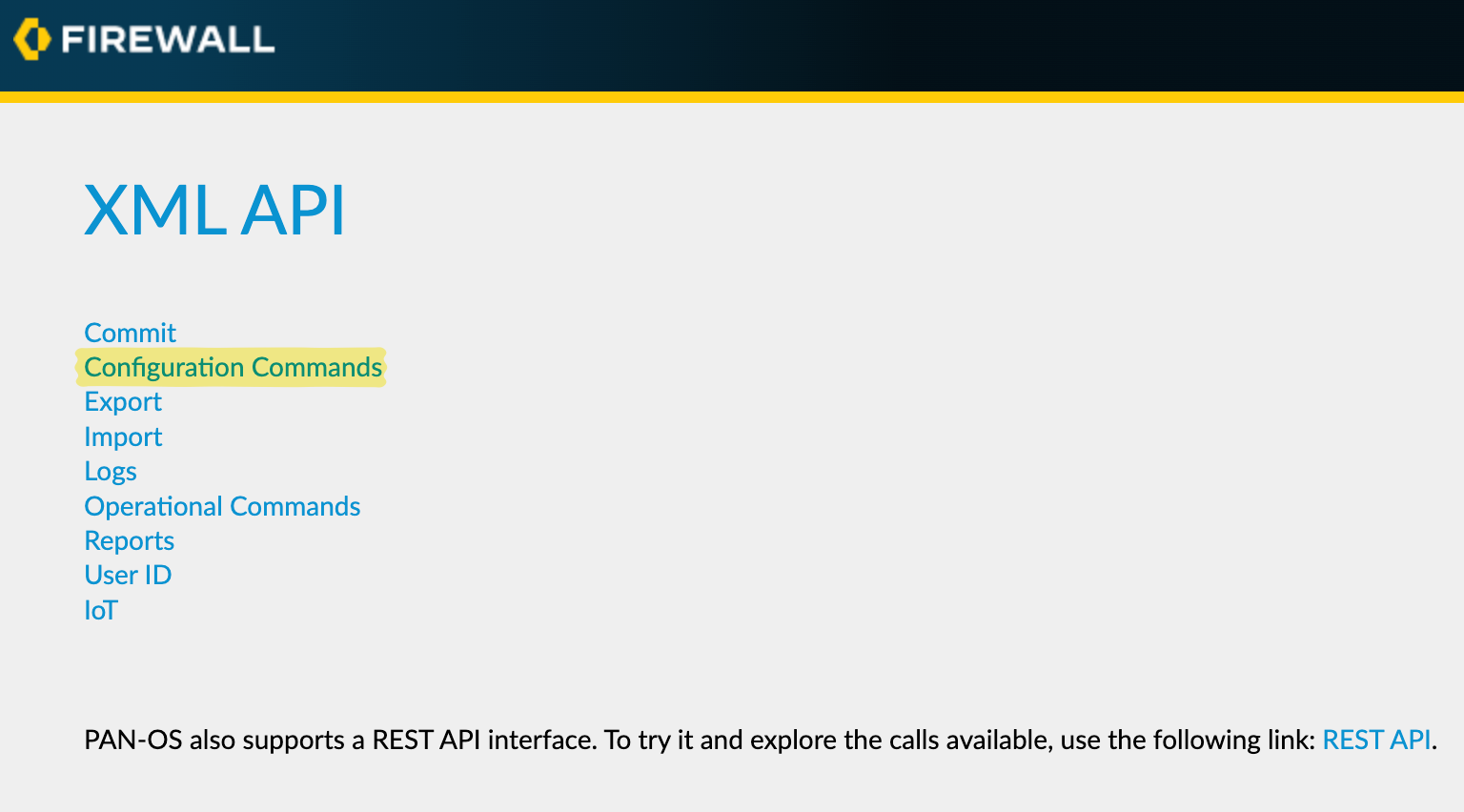
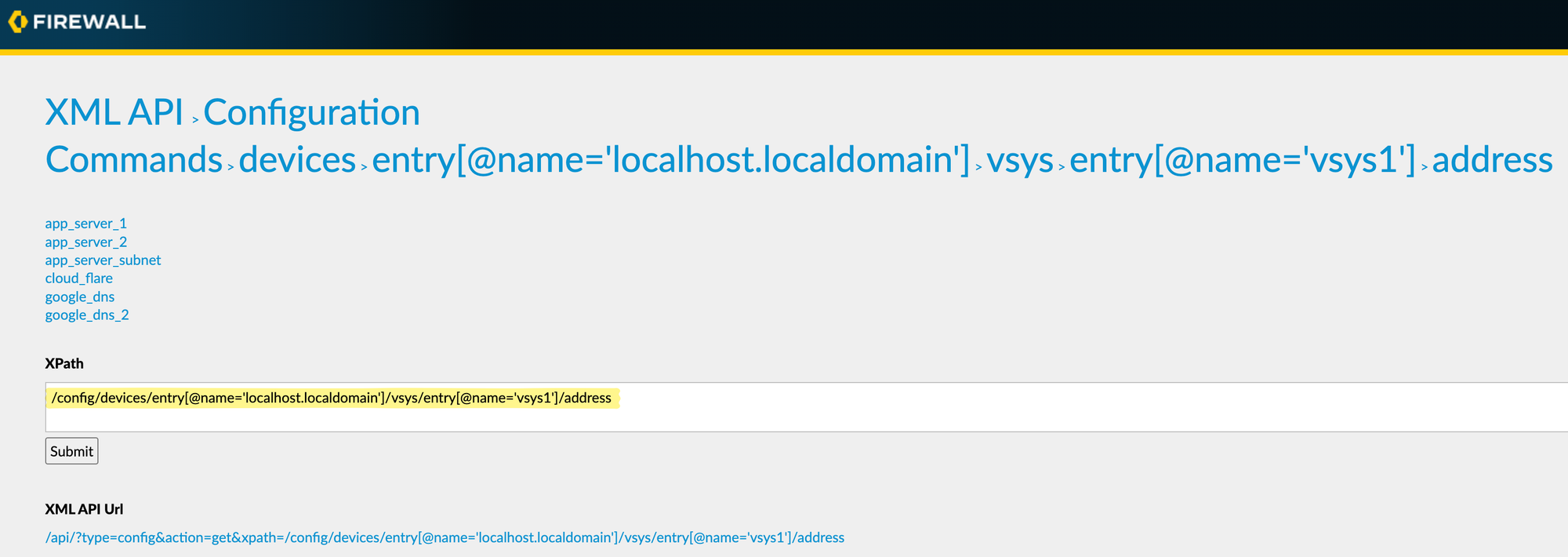
For example, we identified the XPath for address objects on the firewall as shown in the above figure. Here are the XPaths for address, address-groups and security policies on the firewall.
/config/devices/entry[@name='localhost.localdomain']/vsys/entry[@name='vsys1']/address
/config/devices/entry[@name='localhost.localdomain']/vsys/entry[@name='vsys1']/address-group
/config/devices/entry[@name='localhost.localdomain']/vsys/entry[@name='vsys1']/rulebase/security/rulesPanorama XPath
When finding the XPath in Panorama using the XML API, the process is similar to that of the firewall, but the device group must be considered.
Start by navigating through 'Configuration Commands' on the Panorama XML API page until you reach the section for devices and device groups. Here, use the device group you are working with. The XPath for address objects in a device group, as seen in the example, looks similar to that of the firewall but includes an extra layer for the device group.
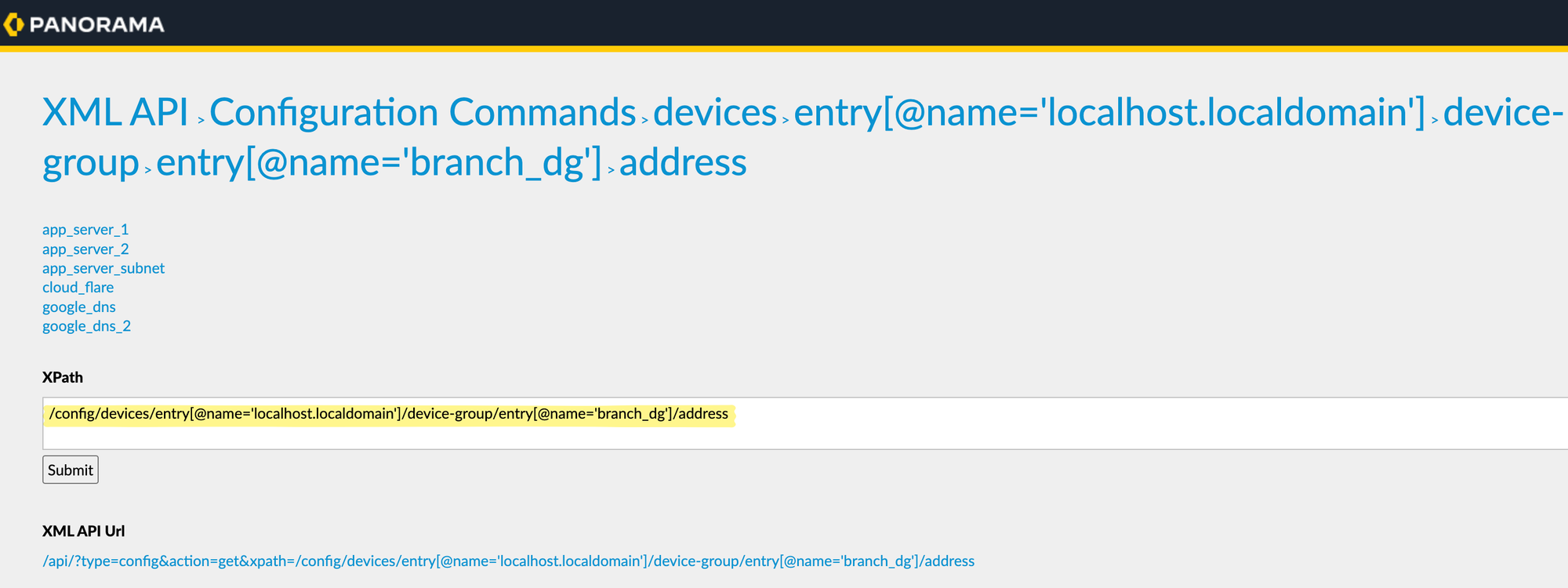
/config/devices/entry[@name='localhost.localdomain']/device-group/entry[@name='branch_dg']/address
/config/devices/entry[@name='localhost.localdomain']/device-group/entry[@name='branch_dg']/address-group
/config/devices/entry[@name='localhost.localdomain']/device-group/entry[@name='branch_dg']/pre-rulebase/security/rulesCopy the Configurations
Finally, to merge the configurations, we use the load config partial command. This command essentially says, "We want to load part of the configuration from a specific file (the one we imported), from a specific section (XPath) into Panorama, to a specific section (XPath)."
This allows for full control over which parts of the configuration are updated in Panorama, making sure that only the intended sections are modified.
admin@panorama-01# load config partial mode merge from-xpath /config/devices/entry[@name='localhost.localdomain']/vsys/entry[@name='vsys1']/address to-xpath /config/devices/entry[@name='localhost.localdomain']/device-group/entry[@name='branch_dg']/address from site-01.xml
Config loaded from site-01.xml
admin@panorama-01# load config partial mode merge from-xpath /config/devices/entry[@name='localhost.localdomain']/vsys/entry[@name='vsys1']/address-group to-xpath /config/devices/entry[@name='localhost.localdomain']/device-group/entry[@name='branch_dg']/address-group from site-01.xml
Config loaded from site-01.xml
admin@panorama-01# load config partial mode merge from-xpath /config/devices/entry[@name='localhost.localdomain']/vsys/entry[@name='vsys1']/rulebase/security/rules to-xpath /config/devices/entry[@name='localhost.localdomain']/device-group/entry[@name='branch_dg']/pre-rulebase/security/rules from site-01.xml
Config loaded from site-01.xmladmin@panorama-01> show config diff
}
}
__vm_series {
- phash $5$rktwgrul$WfAw9.kV6nRrkCzr1yqv0FIBjFFunPovjv0shbII1kA;
+ phash $5$rbrjnuap$ZOjlCeO.vZBBYKaCzyFzSovhfV5LagpjsNK8HxfgWp/;
permissions {
role-based {
panorama-admin yes;
@@ -75,6 +75,66 @@
device-group {
branch_dg {
devices;
+ address {
+ google_dns {
+ ip-netmask 8.8.8.8/32;
+ }
+ cloud_flare {
+ ip-netmask 1.1.1.1;
+ }
+ app_server_1 {
+ ip-netmask 192.168.10.10;
+ }
+ app_server_2 {
+ ip-netmask 192.168.10.11;
+ }
+ app_server_subnet {
+ ip-netmask 192.168.10.0/24;
+ }
+ google_dns_2 {
+ ip-netmask 8.8.4.4;
+ }
+ }
+ address-group {
+ dns_servers {
+ static [ cloud_flare google_dns];
+ }
+ google_dns_servers {
+ static [ google_dns google_dns_2];
+ }
+ }
+ pre-rulebase {
+ security {
+ rules {
+ allow_dns {
+ to any;
+ from any;
+ source any;
+ destination dns_servers;
+ source-user any;
+ category any;
+ application dns;
+ service application-default;
+ source-hip any;
+ destination-hip any;
+ action allow;
+ }
+ ssh_access {
+ to any;
+ from any;
+ source app_server_1;
+ destination any;
+ source-user any;
+ category any;
+ application any;
+ service application-default;
+ source-hip any;
+ destination-hip any;
+ action allow;
+ }
+ }
+ }
+ }
}
}
template {
@@ -183,6 +243,14 @@
device-group {
branch_dg {
id 11;
+ address-group {
+ dns_servers {
+ id 17;
+ }
+ google_dns_servers {
+ id 18;
+ }
+ }
}
}
template {
@@ -206,6 +274,6 @@
}
}
}
- max-internal-id 16;
+ max-internal-id 18;
}
}That's it and commit the changes. Everything we copied from the firewall will now show up in Panorama for us to use.
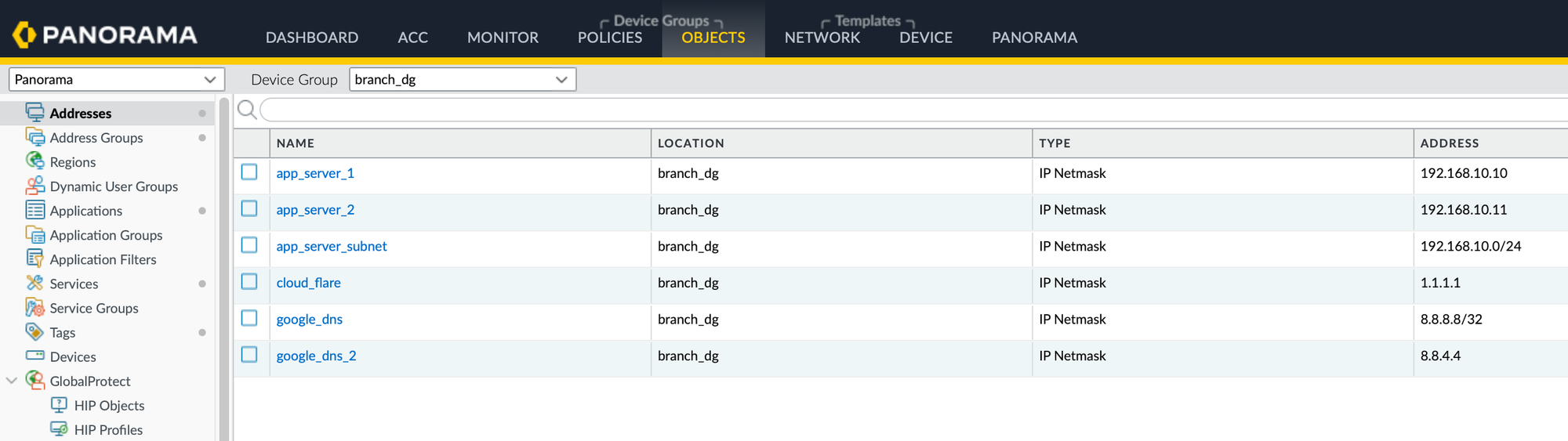
Handling Conflicts
When you use the load config partial mode merge and there are conflicts between the configurations, the objects you are importing take precedence. For example, if there's an existing object in Panorama with the same name as one you're importing but with a different IP address, the IP address in Panorama will be replaced with the one from the imported object.
However, if the existing object includes a description and the imported one does not, then the configurations will simply merge. This means the existing description will be retained.
Merge vs Replace
When using the command to load partial configurations in Panorama, you can choose between 'merge' and 'replace' modes. The 'merge' mode integrates the specified parts of the configuration with existing configs, preserving both the new and existing configurations.
On the other hand, the 'replace' mode is more drastic because it replaces all the objects under the specified XPath with the new configuration. For example, if you already have 100 address objects in Panorama and you use 'replace' to import a few objects from the firewall, it will delete all 100 existing objects and only keep the newly imported ones.