Overview
One of the best features of the Palo Alto firewall is hands-down User-ID. In simple terms, User-ID maps an IP address to a user. So, when you create firewall rules, you can reference the Active Directory usernames/groups instead of solely relying on the subnets or IPs.
User-ID provides many mechanisms to collect User-to-IP mapping information. For example, the User-ID Agent (more on this later) monitors server logs for logon events and listens for syslog messages from authenticating services such as Radius/Cisco ISE. To identify mappings for IP addresses that the agent didn’t map, you can also configure Authentication Policies to redirect HTTP requests to a Captive Portal.
User-ID can be very handy when you want to implement Role-Based Security Policies. Let's say you have three departments within your organization: HR, Marketing and IT, and you want to provide different access for each department. For example, HR has minimal access, Marketing has access to confidential information and IT has full access to all the resources.
If you solely rely on IP addresses then you need to create different subnets for each team and then create Security Rules based on the subnets. You also need to ensure that the users using the correct VLANs or subnets. It can become very difficult to manage and doesn't scale well.
For Wi-Fi, without User-ID, you will need to create different SSID for each department and allocate them to different subnets. For example, HR may connect to 'HR-WIFI' and use '192.168.11.0/24' whereas IT may connect to 'IT-WIFI' and use '192.168.12.0/24'. The firewall rules will reference these subnets and provide a different level of access.
Now imagine having a lot of departments and where do we even begin to manage the wired infrastructure?
User-ID components
- Domain Joined PC/Laptops/Mac (end-user devices)
- Domain Controller / Active Directory
- User-ID Agents
- Terminal Server Agents
- Palo Alto Firewall (of course)
Windows Logon Events
Before we dive further into User-ID, let's look at what happens when end-users login into their computer. This is the most crucial part of the User-ID implementation.
In a nutshell, when a user login to their domain-joined PC, a logon event is generated on the domain controllers that have the username of the user and the IP address of the PC. We can then configure the User-ID agent to poll this information from the domain controller.
User-ID Agents
You can install the User-ID agents on a windows server and then connect the User-ID agent to your domain controllers to read the logon events.
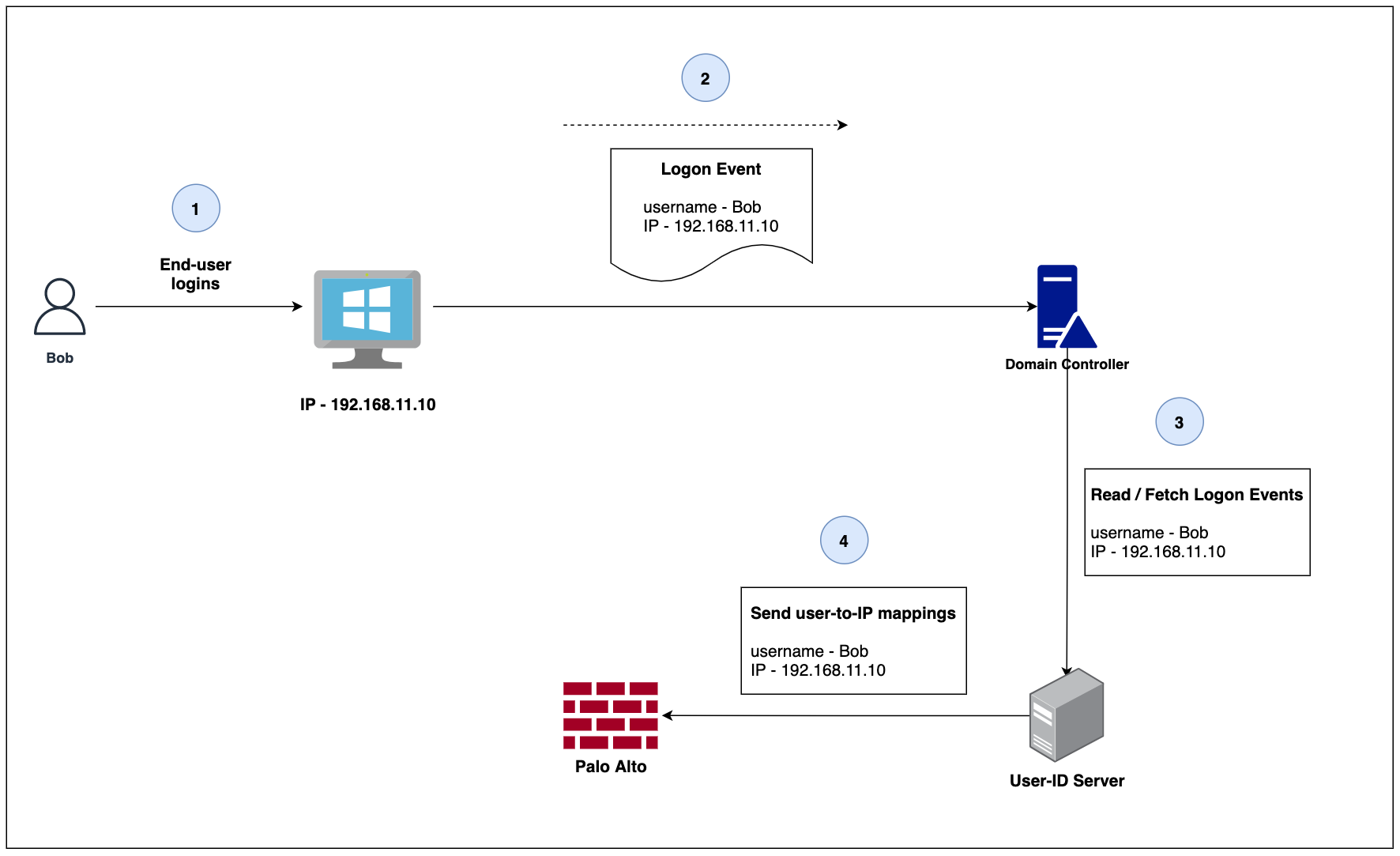
- Users log in with their credential
- A logon event is created and sent out to the Domain Controller.
- User-ID agents read/fetch the information from the Domain controller
- User-ID sends the User-to-IP mappings to the firewall.
Terminal Server Agents
On a system that supports multiple users such as Citrix where multiple users log in to the same physical machine and share the same IP address. You can use Terminal Server (TS) agents in such scenarios.
TS agent identifies individual users by allocating port ranges to each one. The TS agent then informs every connected firewall of the allocated port range so that the firewalls can enforce policy based on users and user groups.
You can specify the number of ports to allocate to each individual user upon login to the terminal server. You can also specify the Port Allocation Maximum Size Per User, which is the maximum number of ports the Terminal Server agent can allocate to an individual user.
For example, if you allocate a start size of 200 and the maximum size of 2000 and 3 users log in to the Citrix system they will get the allocation as follows.
| User | Ports |
|---|---|
| Bob | 20000-21999 |
| Mark | 22000-23999 |
| Simon | 24000-25999 |
Now when the traffic arrives at the firewall, it can differentiate the users based on the source port numbers.
Syslog Messages
To obtain IP-to-username mappings from existing network services that authenticate users such as Cisco ISE, you can configure the User-ID agent to parse Syslog messages from those services.
For example, let's say you authenticate all wireless users with Cisco ISE using 802.1X. With 802.1X every time a user connects to the Wi-Fi, a syslog message is generated that has the information about the username and the IP address. You can configure ISE to send this specific Syslog message to the User-ID agents to parse the message and extract the IP address and username.
Closing Thoughts
In summary, User-ID simplifies policy management, offers improved visibility into user activity, and enhances overall network security.