NAT Gateway enables instances in a private subnet to connect to the Internet but external services cannot initiate a connection with those instances.
Why does High Availability matter?
High availability is crucial for any infrastructure setup, ensuring the continuity and stability of your services. In the context of AWS, achieving high availability for your NAT Gateway means that even if one Availability Zone (AZ) experiences an outage, your instances can continue to access the internet without any interruptions.
Private vs Public subnet
The instances in the public subnet can send outbound traffic directly to the Internet via Internet Gateway (IGW), whereas the instances in the private subnet can't. Instead, the instances in the private subnet can access the Internet by using a NAT gateway that resides in the public subnet.
A typical example is a public-facing web application (public subnet) where the inbound/outbound traffic is routed via the IGW. Back-end servers on the other hand are not publically accessible however, they can still reach out to the Internet for downloading packages or updating OS.

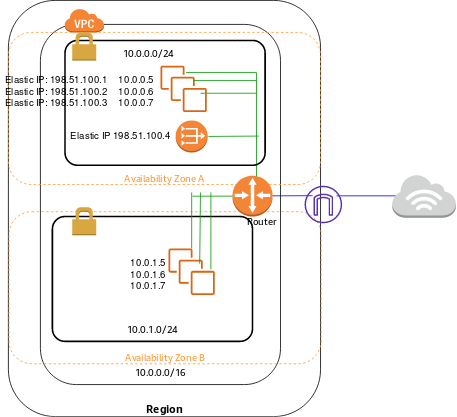
As per the above diagram, instances in the public subnet have routes to the Internet via IGW. Instances in the private subnet have routes to the Internet via NAT gateway. Users on the Internet can also initiate inbound connections to the instances in the public subnet using their public/elastic IP.
How does the NAT gateway work?
Public NAT Gateway
To create a NAT gateway, you must specify the public subnet in which the NAT gateway should reside. An elastic IP address has to be associated with a NAT gateway when it is created. Each NAT gateway is created in a specific Availability Zone and implemented with redundancy in that zone. As you can see above, the NAT gateway was created in AZ-1/public subnet 1a.
The NAT gateway replaces the source IP address of the instances with the IP address of the NAT gateway. For a public NAT gateway, this is the elastic IP address of the NAT gateway.
Private NAT Gateway
A private NAT Gateway does not require Elastic IP and you do not need to attach an IGW with your VPC. Instances in private subnets can connect to other VPCs or on-premises networks through a private NAT gateway.
You can route traffic from the NAT gateway through a transit gateway or a virtual private gateway. You cannot associate an elastic IP address with a private NAT gateway. You can attach an Internet gateway to a VPC with a private NAT gateway, but if you route traffic from the private NAT gateway to the internet gateway, the Internet gateway will drop the traffic.
NAT Gateway HA scenario
NAT Gateway is Highly Available in one Availability Zone, If you have resources in multiple Availability Zones and they share one NAT gateway, and if the NAT gateway’s Availability Zone is down, resources in the other Availability Zones lose Internet access.
In our example above, if AZ 1a goes down, instances in other AZs lose Internet Access.
Depending on your business requirement and fault-tolerant architecture, make sure to create NAT Gateways in at least two Availability Zones.

As you can see above, now we have NAT Gateways in each AZ which provide fault-tolerance against AZ failures.
Reference
Thanks for reading
As always, your feedback and comments are more than welcome.




