There are many articles out there about ICMP and PING. This article solely focuses on ICMP traffic passing through Adaptive Security Appliance. With the default configurations ASA will allow a host to ping the interface to which is connected to. However, ping from an internal host to the internet would normally fail.
By default, traffic from Higher Security Zone to (Inside) Lower Security Zone (Outside) is allowed without any Access Lists. Return traffic from Outside to Inside will be allowed through because the traffic was initiated from Inside.
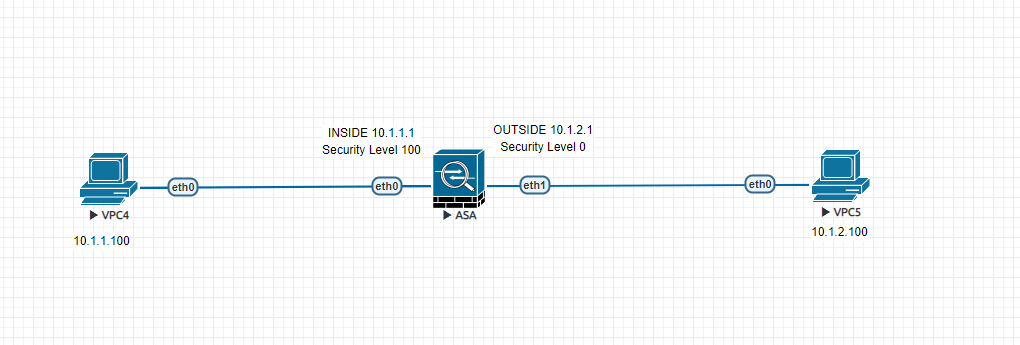
For example, a client accessing a web page on the Internet. When a packet arrives in the Inside interface from the client, the packet is categorized into a flow based on five-tuple which contains the source IP, Source Port, Destination IP, Destination Port and the Layer 4 protocol. ASA then maintains a state table to track these connections/flows. Based on this state table the return traffic from the webserver is allowed through the firewall.
Back to ASA and Ping, ping is part of the ICMP protocol suite and handled differently compared to TCP/UDP. ASA doesn't track ICMP sessions/connections, making it stateless. Because ICMP packets do not themselves contain any connection information. Being stateless, ASA will let the ICMP echo request from Inside to Outside, but it will not allow the ICMP echo reply from Outside to Inside.
Cisco ASA can track ICMP sessions by enabling ICMP Inspection Engine. This results in an ICMP session being tracked, which in turn allows the ICMP reply packets to pass through from Outside to Inside. ICMP inspection can also dynamically allow time-exceeded and destination unreachable messages to pass through the Outside interface. (ICMP traffic has to be initiated from Inside to start with)
Below you will find the ICMP inspection configuration.
policy-map global_policy
class inspection_default
inspect icmpSo now when the client tries and ping the webserver, the ICMP echo-request packet is allowed through. ASA has now started to track this ICMP session. Finally, when the webserver sends echo-reply, ASA determines that this packet is part of an existing session and allows the packet through.
When ICMP Inspection is disabled. Ping from VPC4 to VPC5 would fail. ASA will let the echo request passes through the ASA however, ICMP reply from VPC5 to VPC4 is denied.
VPC4> ping 10.1.2.100
10.1.2.100 icmp_seq=1 timeout
10.1.2.100 icmp_seq=2 timeout
10.1.2.100 icmp_seq=3 timeout
10.1.2.100 icmp_seq=4 timeout
10.1.2.100 icmp_seq=5 timeoutASA logs
%ASA-6-302020: Built outbound ICMP connection for faddr 10.1.2.100/0 gaddr 10.1.1.100/18710 laddr 10.1.1.100/18710
%ASA-3-106014: Deny inbound icmp src outside:10.1.2.100 dst inside:10.1.1.100 (type 0, code 0)Enable ICMP Inspection
TEST-ASA(config)# policy-map global_policy
TEST-ASA(config-pmap)# class inspection_default
TEST-ASA(config-pmap-c)# inspect icmp
TEST-ASA(config-pmap-c)# exit
TEST-ASA(config-pmap)# exit
VPCS> ping 10.1.2.100
84 bytes from 10.1.2.100 icmp_seq=1 ttl=64 time=1.441 ms
84 bytes from 10.1.2.100 icmp_seq=2 ttl=64 time=1.482 ms
84 bytes from 10.1.2.100 icmp_seq=3 ttl=64 time=1.438 msASA now tracks the ICMP connection, therefore, the return ICMP reply is allowed through.




