In this blog post, let's have a look at how to configure a Site-to-Site VPN on Cisco ASA firewalls. What if I tell you that configuring site-to-site VPN on the Cisco ASA only requires around 15 lines of configuration? Better yet, you may only need less than 10 lines if you already have another VPN tunnel configured.
This blog post assumes prior knowledge of Cisco ASA CLI syntax and site-to-site VPN fundamentals.
If you are looking to configure Cisco ASA VTI Tunneled-based VPN, please check out my other blog post below.

Diagram
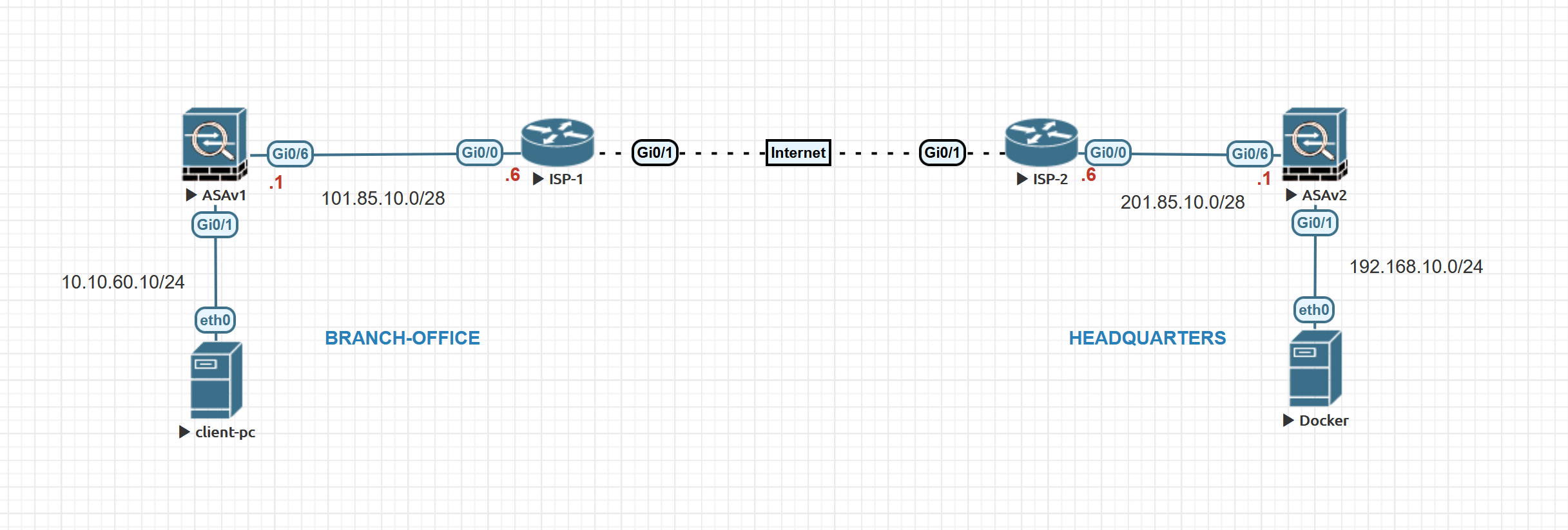
Our ultimate goal here is to set up a site-to-site VPN between the Branch Office and the Headquarters. Let's assume the client-pc (10.10.60.10) in the branch office needs to access a web server (192.168.10.10) in the headquarters.
Cisco ASA non-VPN Configurations
Branch Office
Branch Office ASA
-----------------
interface GigabitEthernet0/1
nameif USERS
security-level 100
ip address 10.10.60.1 255.255.255.0
interface GigabitEthernet0/6
nameif OUTSIDE
security-level 0
ip address 101.85.10.1 255.255.255.248
route OUTSIDE 0.0.0.0 0.0.0.0 101.85.10.6 1
object network ho-server-subnet
subnet 192.168.10.0 255.255.255.0
object network user-subnet
subnet 10.10.60.0 255.255.255.0
nat (USERS,OUTSIDE) dynamic interface
The interface configuration is self-explanatory, ASA has two interfaces, one for the user and another one for the Internet. The default route is pointing to the ISP router with a static route. There are two objects, one for the branch user subnet and another one for the HQ webserver subnet.
The NAT part is quite important because we will talk about that later. As you can see above, I have a dynamic PAT configuration for the user subnet. So, when the user traffic leaves the ASA, the source IP is translated to the IP address of the ASA's outside interface (101.85.10.1)
Headquarters
interface GigabitEthernet0/1
nameif SERVERS
security-level 50
ip address 192.168.10.1 255.255.255.0
interface GigabitEthernet0/6
nameif OUTSIDE
security-level 0
ip address 201.85.10.1 255.255.255.248
route OUTSIDE 0.0.0.0 0.0.0.0 201.85.10.6 1
object network branch-user-subnet
subnet 10.10.60.0 255.255.255.0
object network ho-server-subnet
subnet 192.168.10.0 255.255.255.0
nat (SERVERS,OUTSIDE) dynamic interface
Same as above except for the object names and the IPs.
ASA VPN configurations IKEv1
Please note that if you already have another VPN tunnel then most likely most of the configurations are already done for you. So, please make sure not to change or override them.
Branch Office
- Enable IKEv1 on the outside interface (if not enabled already)
crypto ikev1 enable OUTSIDE2. Create an IKEv1 policy that defines the algorithms/methods to be used for hashing, authentication, DH group, lifetime, and encryption. Please note that these policies should match on both sides. If you already have a policy then you don't need to create them. You can check whether there are any policies by running show run crypto ikev1 command.
crypto ikev1 policy 5
authentication pre-share
encryption aes-256
hash sha
group 5
lifetime 36003. Create a tunnel-group and configure the peer IP address alongside the tunnel pre-shared key (PSK). Please note that the PSKs should match on both sides.
tunnel-group 201.85.10.1 type ipsec-l2l
tunnel-group 201.85.10.1 ipsec-attributes
ikev1 pre-shared-key Cisco1234. Configure the Transform Set which is a combination of security protocols and algorithms that define the way the VPN peers protect data.
crypto ipsec ikev1 transform-set AES-HMAC esp-aes-256 esp-sha-hmac 5. Configure a Crypto Map and apply it to the outside interface. A crypto map defines an IPSec policy that includes an ACL to identify the interesting traffic, peer IP and IKEv1 transform-set that we created in the previous step. If there is already a crypto map applied on the ASA, you only need to add a new entry with the same crypto map name and increment the number instead of creating a new crypto map.
access-list BRANCH-TO-HO extended permit tcp object user-subnet object ho-server-subnet
crypto map VPN-MAP 1 match address BRANCH-TO-HO
crypto map VPN-MAP 1 set peer 201.85.10.1
crypto map VPN-MAP 1 set ikev1 transform-set AES-HMAC
crypto map VPN-MAP 1 set security-association lifetime seconds 3600
crypto map VPN-MAP interface OUTSIDE6. The most crucial part is NAT exemption. As we discussed before, any traffic that is initiated from the user subnet going out to the Internet is NATed to the outside interface's public IP. However, we want the traffic from the branch office to the headquarters to be exempted from the dynamic PAT. So, we need to tell the ASA that if the traffic is initiated from 10.10.60.0/24 and is going out to 192.168.10.0/24, the IP address shouldn't be NAted. The following command just does that.
nat (USERS,OUTSIDE) source static user-subnet user-subnet destination static ho-server-subnet ho-server-subnetHeadquarters Configuration
We just need to mirror the configuration in terms of the IP addresses. Phase-1 and Phase-2 policies should be identical.
crypto ikev1 enable OUTSIDE
crypto ikev1 policy 5
authentication pre-share
encryption aes-256
hash sha
group 5
lifetime 3600
tunnel-group 101.85.10.1 type ipsec-l2l
tunnel-group 101.85.10.1 ipsec-attributes
ikev1 pre-shared-key Cisco123
crypto ipsec ikev1 transform-set AES-HMAC esp-aes-256 esp-sha-hmac
access-list HO-TO-BRANCH extended permit tcp object ho-server-subnet object branch-user-subnet
crypto map HQ-MAP 10 match address HO-TO-BRANCH
crypto map HQ-MAP 10 set peer 101.85.10.1
crypto map HQ-MAP 10 set ikev1 transform-set AES-HMAC
crypto map HQ-MAP 10 set security-association lifetime seconds 3600
crypto map HQ-MAP interface OUTSIDE
nat (SERVERS,OUTSIDE) source static ho-server-subnet ho-server-subnet destination static branch-user-subnet branch-user-subnetThat's all, let's see if the client-pc can access the webserver.
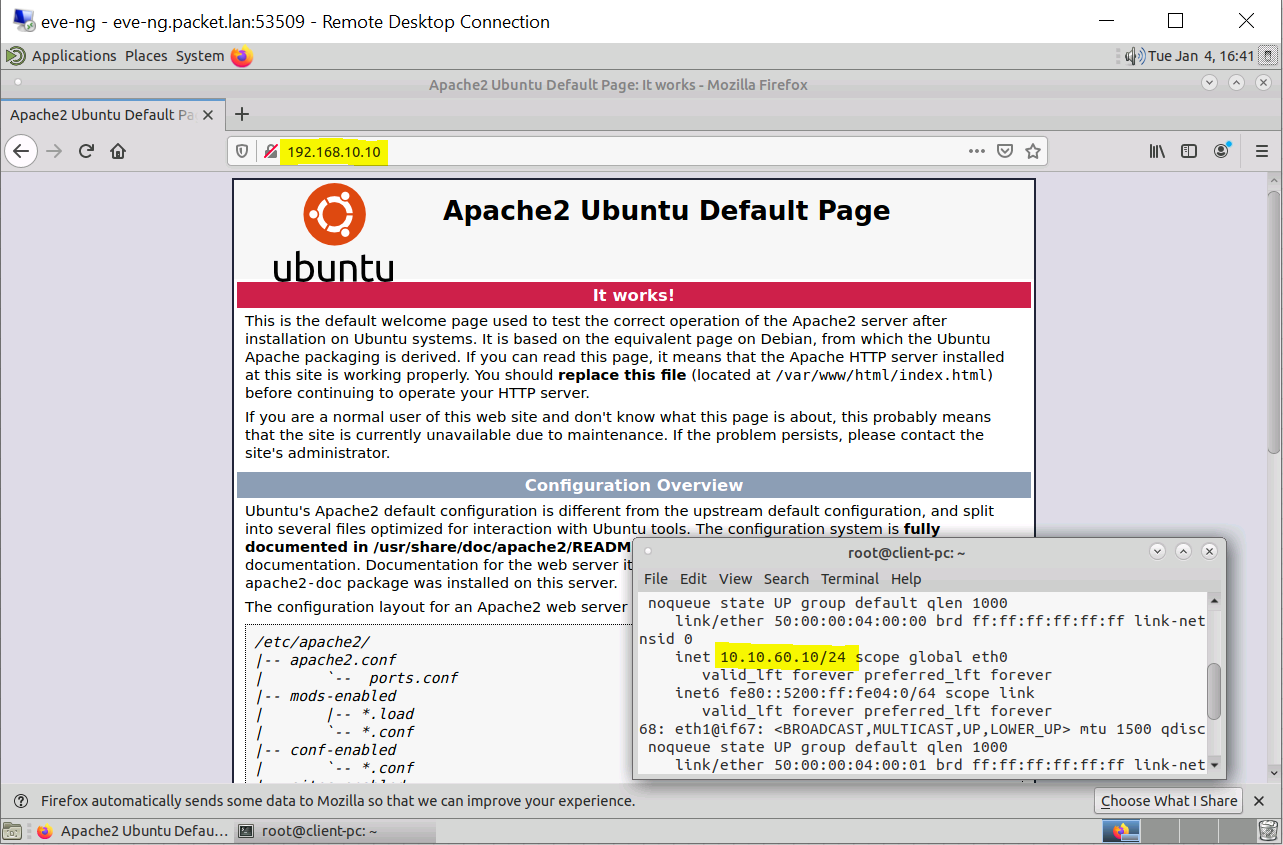
Yes, the client-pc can. There are a few ASA commands that you can use to verify the tunnel status.
Use show crypto isakmp sa to verify the currently active phase - 1 tunnels. As you can see below, branch office ASA initiated the tunnel. Role: initiator using IKEv1.
branch-01# show isa sa
IKEv1 SAs:
Active SA: 1
Rekey SA: 0 (A tunnel will report 1 Active and 1 Rekey SA during rekey)
Total IKE SA: 1
1 IKE Peer: 201.85.10.1
Type : L2L Role : initiator
Rekey : no State : MM_ACTIVE
There are no IKEv2 SAsTo check the status of the phase - 2 IPSec tunnels, you can use show crypto ipsec sa command. #pkts encrypt and #pkts decrypt are a very good indicator if you run into any issues. If you see the 'number of packets' encrypted increasing but the 'number of packets' decrypted stays the same then the issue is with receiving the packets, more likely an issue on the other side. If you see the 'number of packets encrypted' stays the same then our side of the ASA is not sending any traffic through the tunnel.
branch-01# show crypto ipsec sa
interface: OUTSIDE
Crypto map tag: VPN-MAP, seq num: 1, local addr: 101.85.10.1
access-list BRANCH-TO-HO extended permit tcp 10.10.60.0 255.255.255.0 192.168.10.0 255.255.255.0
local ident (addr/mask/prot/port): (10.10.60.0/255.255.255.0/6/0)
remote ident (addr/mask/prot/port): (192.168.10.0/255.255.255.0/6/0)
current_peer: 201.85.10.1
#pkts encaps: 31, #pkts encrypt: 31, #pkts digest: 31
#pkts decaps: 22, #pkts decrypt: 22, #pkts verify: 22
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 31, #pkts comp failed: 0, #pkts decomp failed: 0
#pre-frag successes: 0, #pre-frag failures: 0, #fragments created: 0
#PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0
#TFC rcvd: 0, #TFC sent: 0
#Valid ICMP Errors rcvd: 0, #Invalid ICMP Errors rcvd: 0
#send errors: 0, #recv errors: 0
local crypto endpt.: 101.85.10.1/0, remote crypto endpt.: 201.85.10.1/0
path mtu 1500, ipsec overhead 74(44), media mtu 1500
PMTU time remaining (sec): 0, DF policy: copy-df
ICMP error validation: disabled, TFC packets: disabled
current outbound spi: 7FB999E3
current inbound spi : D9F696BC
ASA VPN configurations IKEv2
I'm going to remove all the IKEv1-related configurations and then re-configure the VPN using IKEv2. The configuration is almost identical to IKEv1.
Branch Office
crypto ikev2 enable OUTSIDE
crypto ikev2 policy 20
encryption aes-256
integrity sha256
group 14
prf sha
lifetime seconds 3600
tunnel-group 201.85.10.1 type ipsec-l2l
tunnel-group 201.85.10.1 ipsec-attributes
ikev2 remote-authentication pre-shared-key Cisco123
ikev2 local-authentication pre-shared-key Cisco123
crypto ipsec ikev2 ipsec-proposal VPN-EXAMPLE
protocol esp encryption aes-256
protocol esp integrity sha-256
crypto map VPN-MAP 1 match address BRANCH-TO-HO
crypto map VPN-MAP 1 set peer 201.85.10.1
crypto map VPN-MAP 1 set ikev2 ipsec-proposal VPN-EXAMPLE
crypto map VPN-MAP 1 set security-association lifetime seconds 3600
crypto map VPN-MAP interface OUTSIDE
Head Office
crypto ikev2 enable OUTSIDE
crypto ikev2 policy 20
encryption aes-256
integrity sha256
group 14
prf sha
lifetime seconds 3600
tunnel-group 101.85.10.1 type ipsec-l2l
tunnel-group 101.85.10.1 ipsec-attributes
ikev2 remote-authentication pre-shared-key Cisco123
ikev2 local-authentication pre-shared-key Cisco123
crypto ipsec ikev2 ipsec-proposal VPN-EXAMPLE
protocol esp encryption aes-256
protocol esp integrity sha-256
crypto map VPN-MAP 1 match address HO-TO-BRANCH
crypto map VPN-MAP 1 set peer 101.85.10.1
crypto map VPN-MAP 1 set ikev2 ipsec-proposal VPN-EXAMPLE
crypto map VPN-MAP 1 set security-association lifetime seconds 3600
crypto map VPN-MAP interface OUTSIDEVerification using show crypto isakmp sa command.
branch-01# show crypto isakmp sa
There are no IKEv1 SAs
IKEv2 SAs:
Session-id:2, Status:UP-ACTIVE, IKE count:1, CHILD count:1
Tunnel-id Local Remote Status Role
6440241 101.85.10.1/500 201.85.10.1/500 READY INITIATOR
Encr: AES-CBC, keysize: 256, Hash: SHA256, DH Grp:14, Auth sign: PSK, Auth verify: PSK
Life/Active Time: 3600/97 sec
Child sa: local selector 10.10.60.0/0 - 10.10.60.255/65535
remote selector 192.168.10.0/0 - 192.168.10.255/65535
ESP spi in/out: 0x35d1507/0xe46501d5 IKEv2 has many new features that make it more reliable and secure but there are many companies that still use IKEv1. One of the benefits of IKEv2 is that it exchanges fewer messages to establish a tunnel compare to IKEv1. IKEv2 uses four messages whereas IKEv1 uses either nine messages (in the main mode) or six messages (in aggressive mode).
Closing Up
Please let me know in the comment section which one did you end up using. As always your comments and feedback are always welcome. If you want to learn about ASA VPN filters, please check out my post here.







