In this blog post I will show you how to configure site-to-site VPN between AWS VPC and Palo Alto Firewall. AWS offers two VPN tunnels between a virtual private gateway or a transit gateway on the AWS side, and a customer gateway on the remote side (Palo Alto in our case)
Logical Diagram
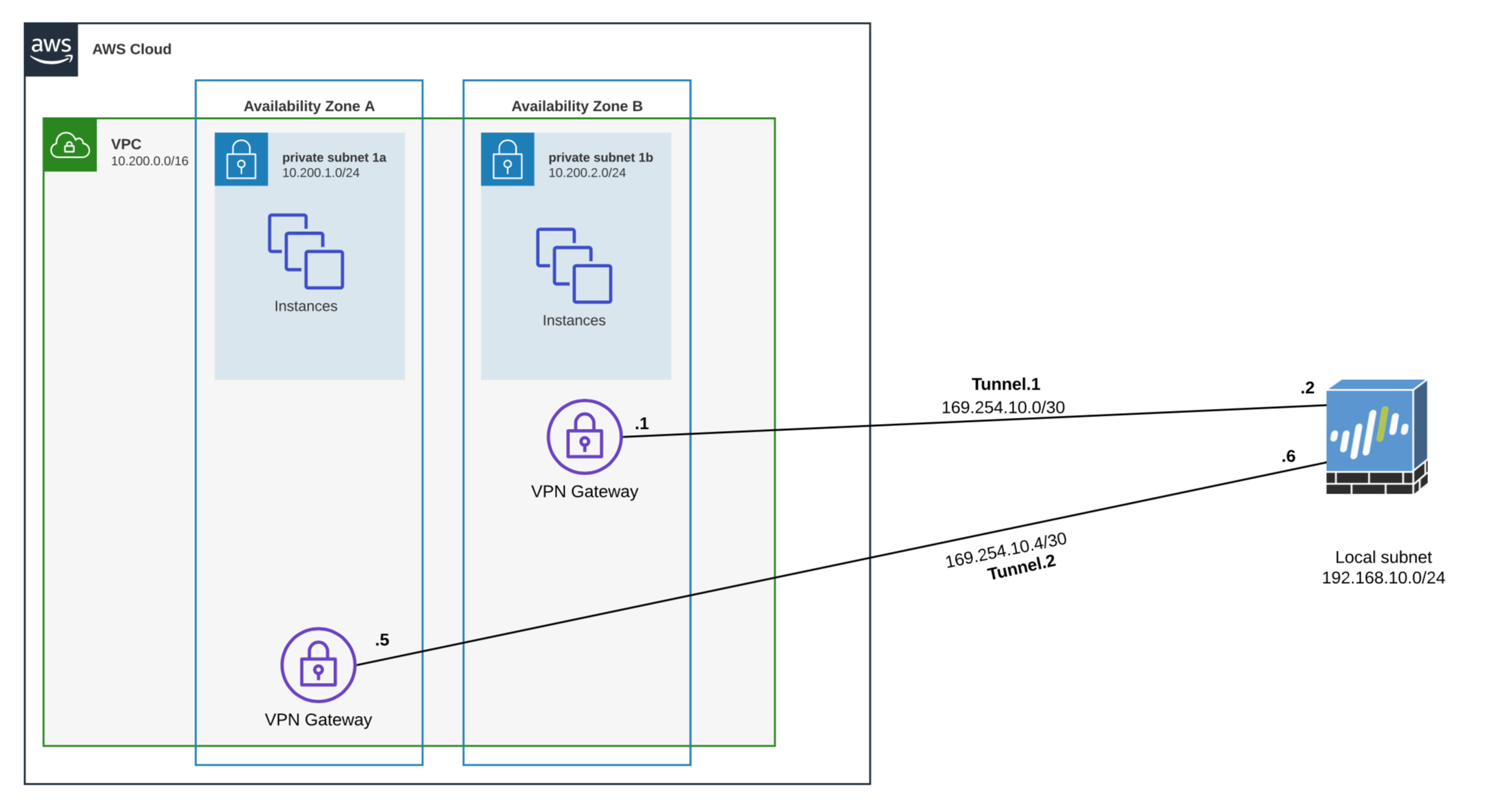
As you can see in the above diagram, there are two logical tunnels between AWS and PA. Each tunnel terminates on different AZ on AWS for redundancy.
Assumptions
- PA public IP - 3.3.3.3
- AWS VPN endpoint public IPs - 1.1.1.1 & 2.2.2.2
- Using the minimum requirement of AES128, SHA1, and DH Group 2.
AWS Configuration
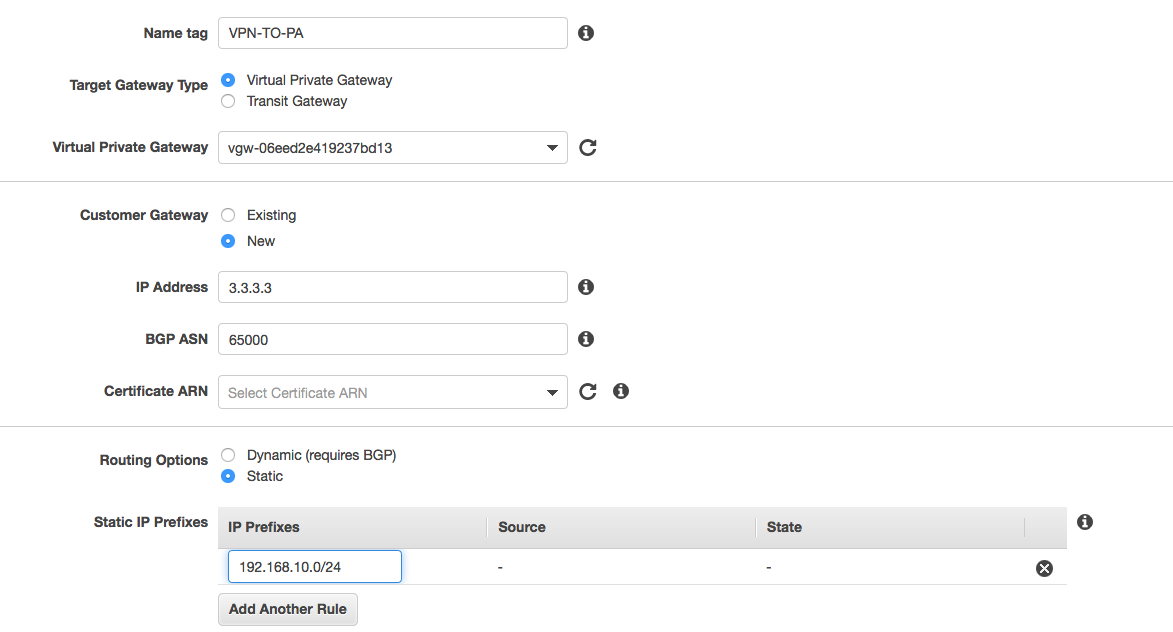
To create a new VPN connection, go to VPC and choose Site-to-Site VPN connection in the navigation pane.
Palo Alto Configuration
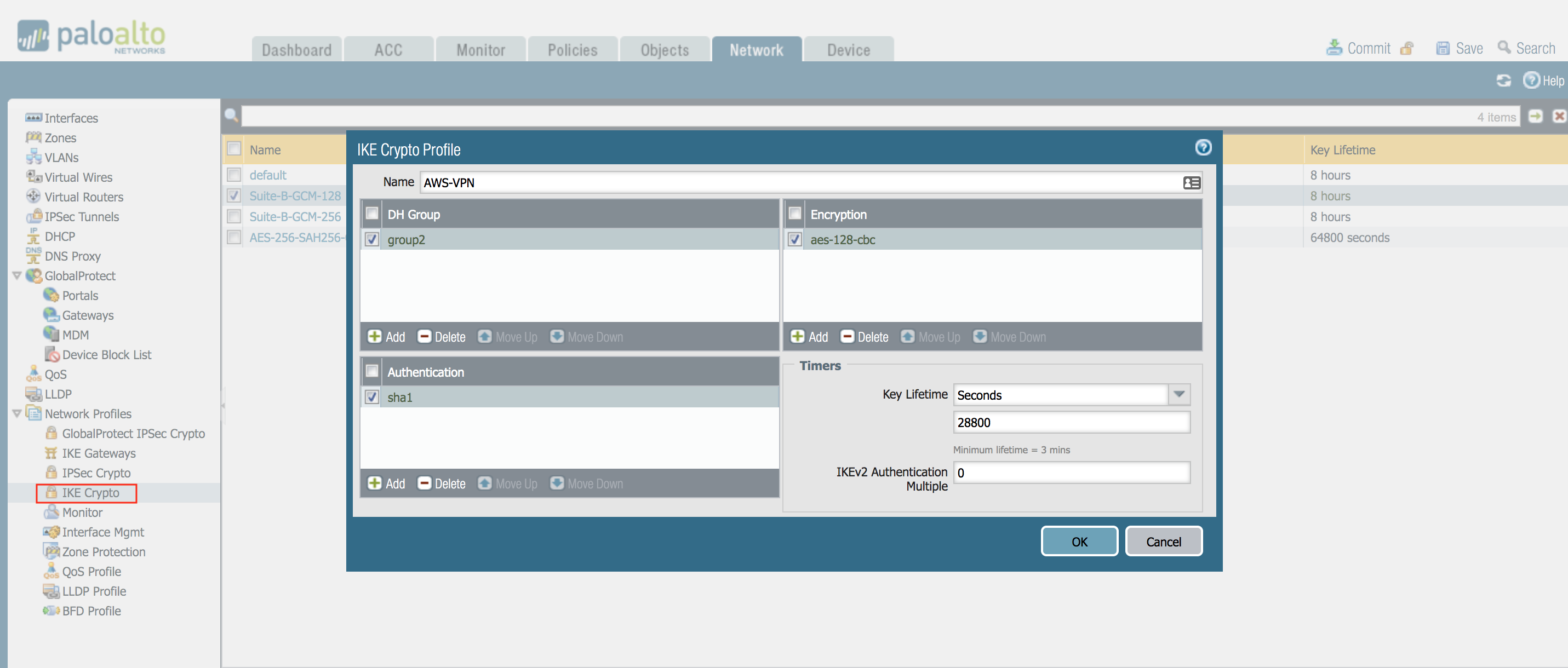
IKE Crypto Profile
Create supported ISAKMP encryption, authentication, Diffie-Hellman, lifetime, and key parameters. Please note, these sample configurations are for the minimum requirement of AES128, SHA1, and DH Group 2.
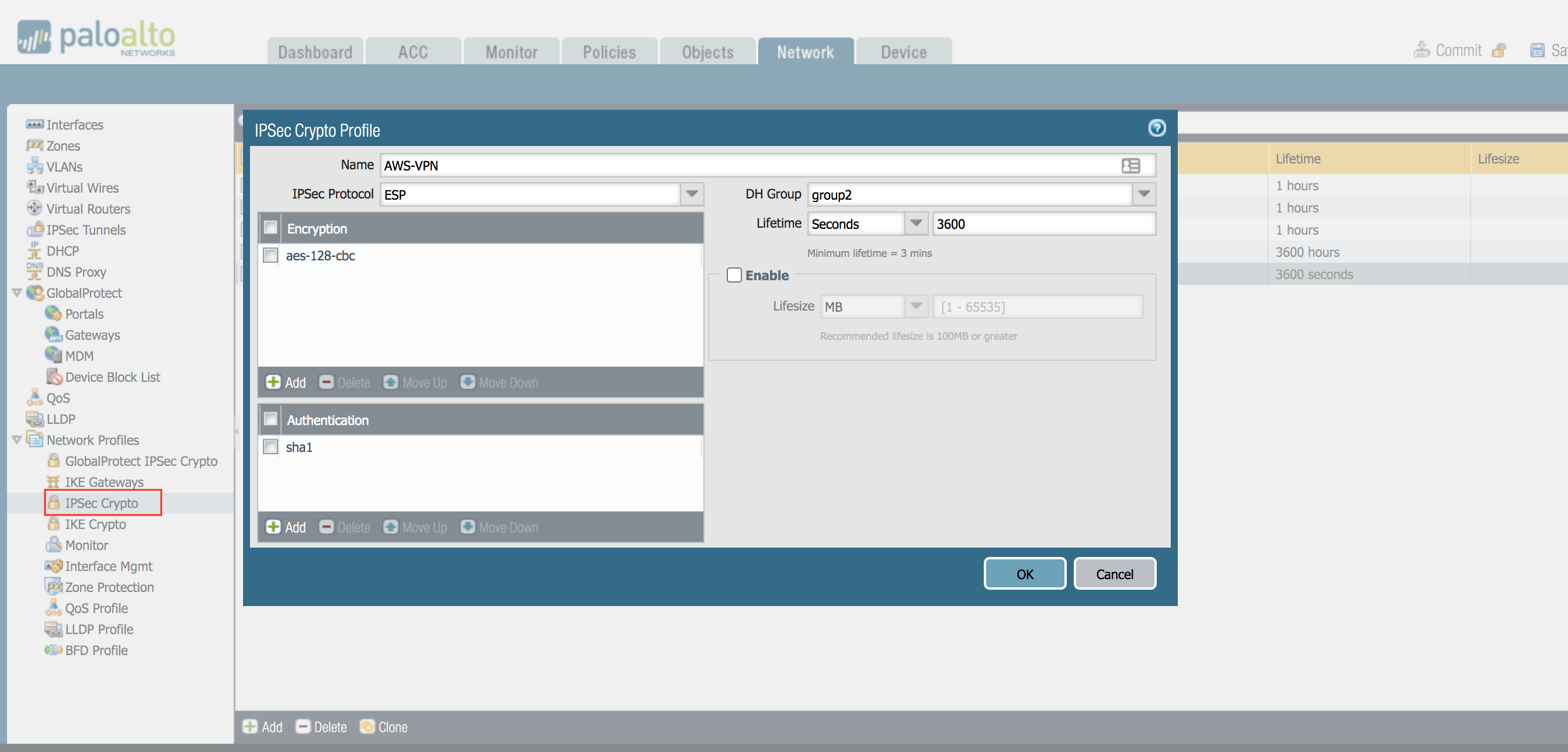
IPSec Crypto Profile
The IPSec profile defines the encryption, authentication, and IPSec mode parameters.
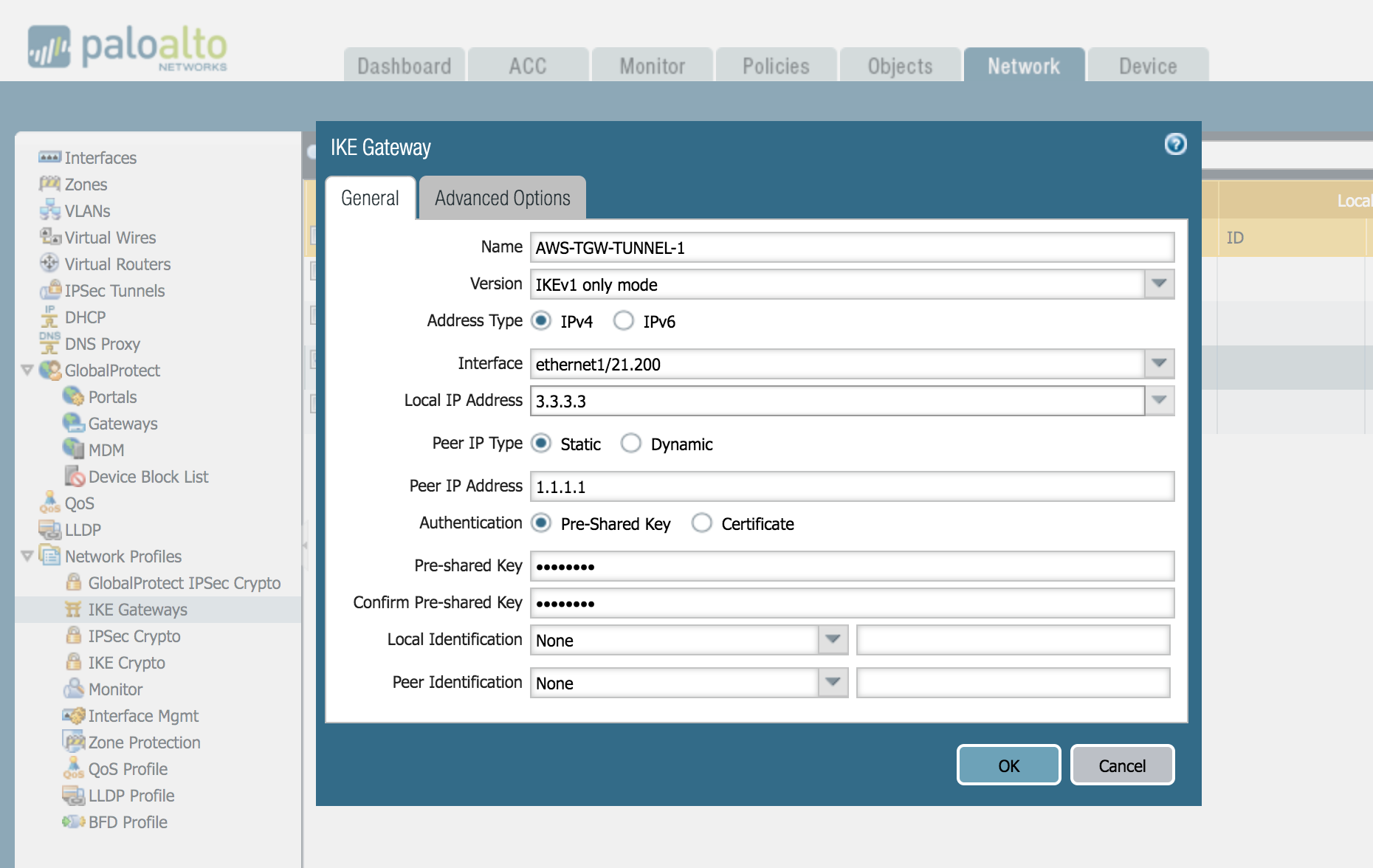
IKE Gateways
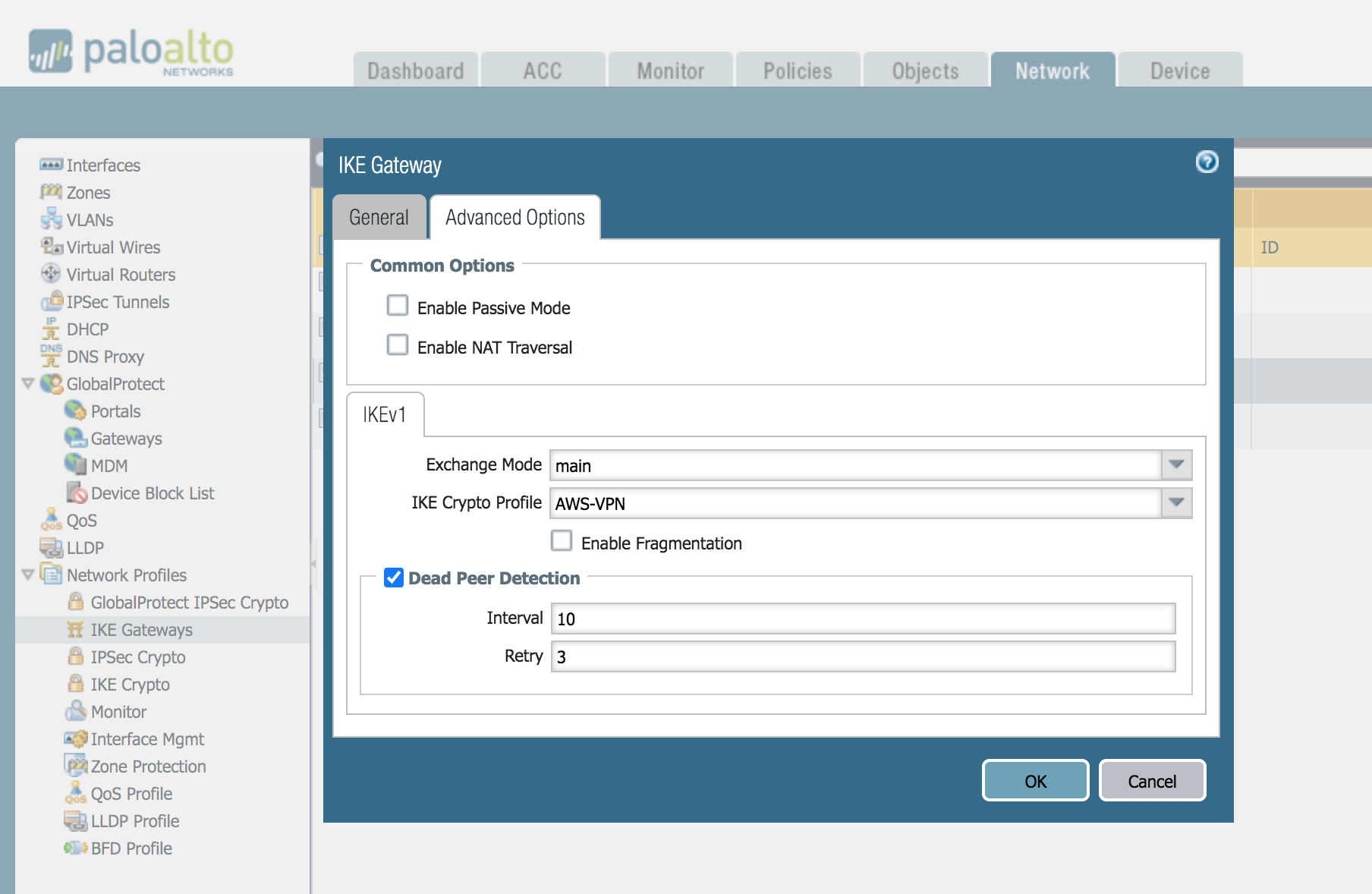
Two Security devices or Firewalls that initiate and terminate VPN connections across the two networks are called the IKE Gateways. Each peer must have an IP address assigned. PA and AWS use pre-shared keys to mutually authenticate each other. The peers must also negotiate the mode, in our case main mode. We also need to select the IKE profile created in the first step. Create 2 X Gateways for both Tunnels.
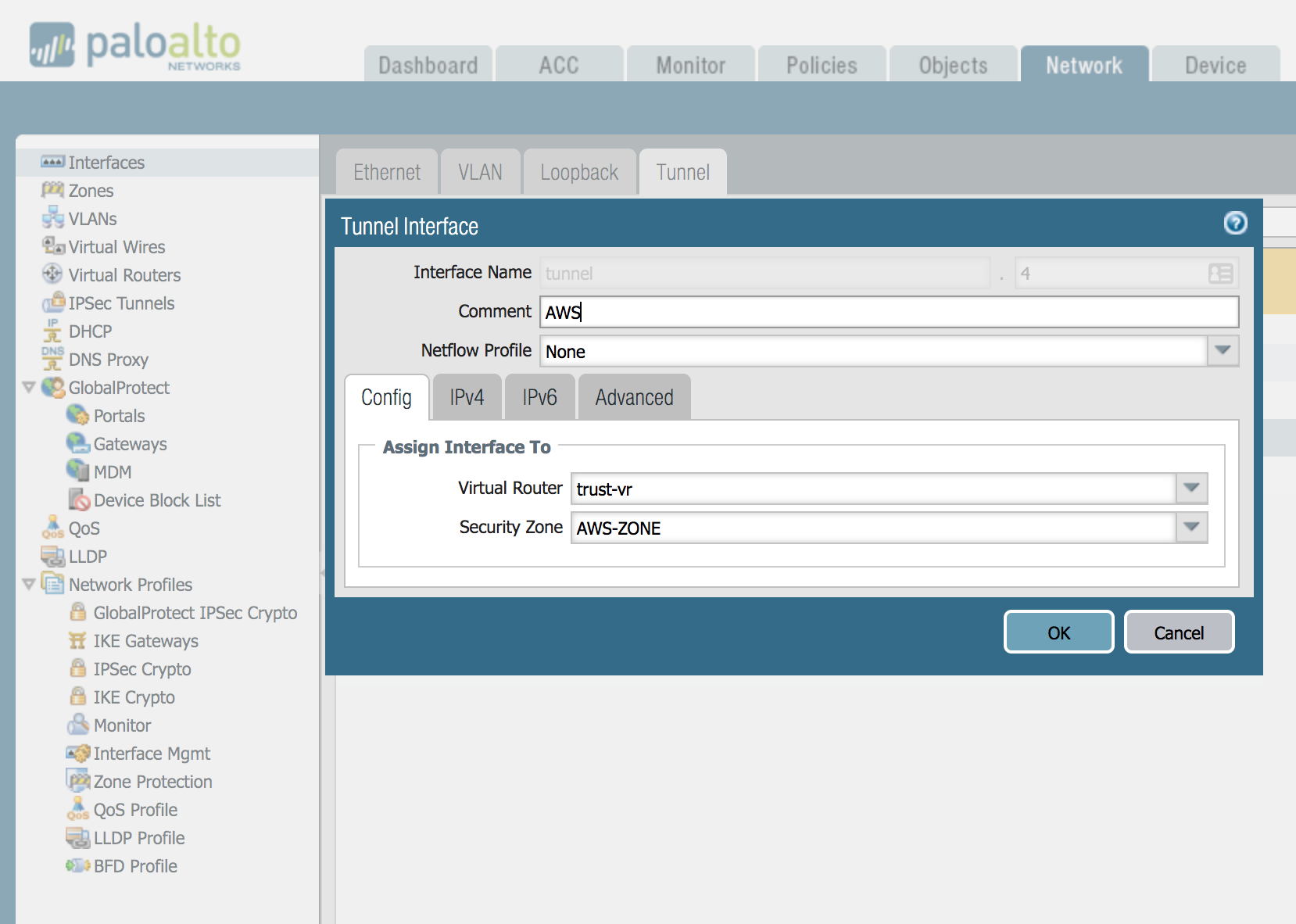
Tunnel Interface
Create 2 x Tunnel interfaces and set the MTU to 1427. You can also assign the interface to the appropriate Virtual Router and Zone.
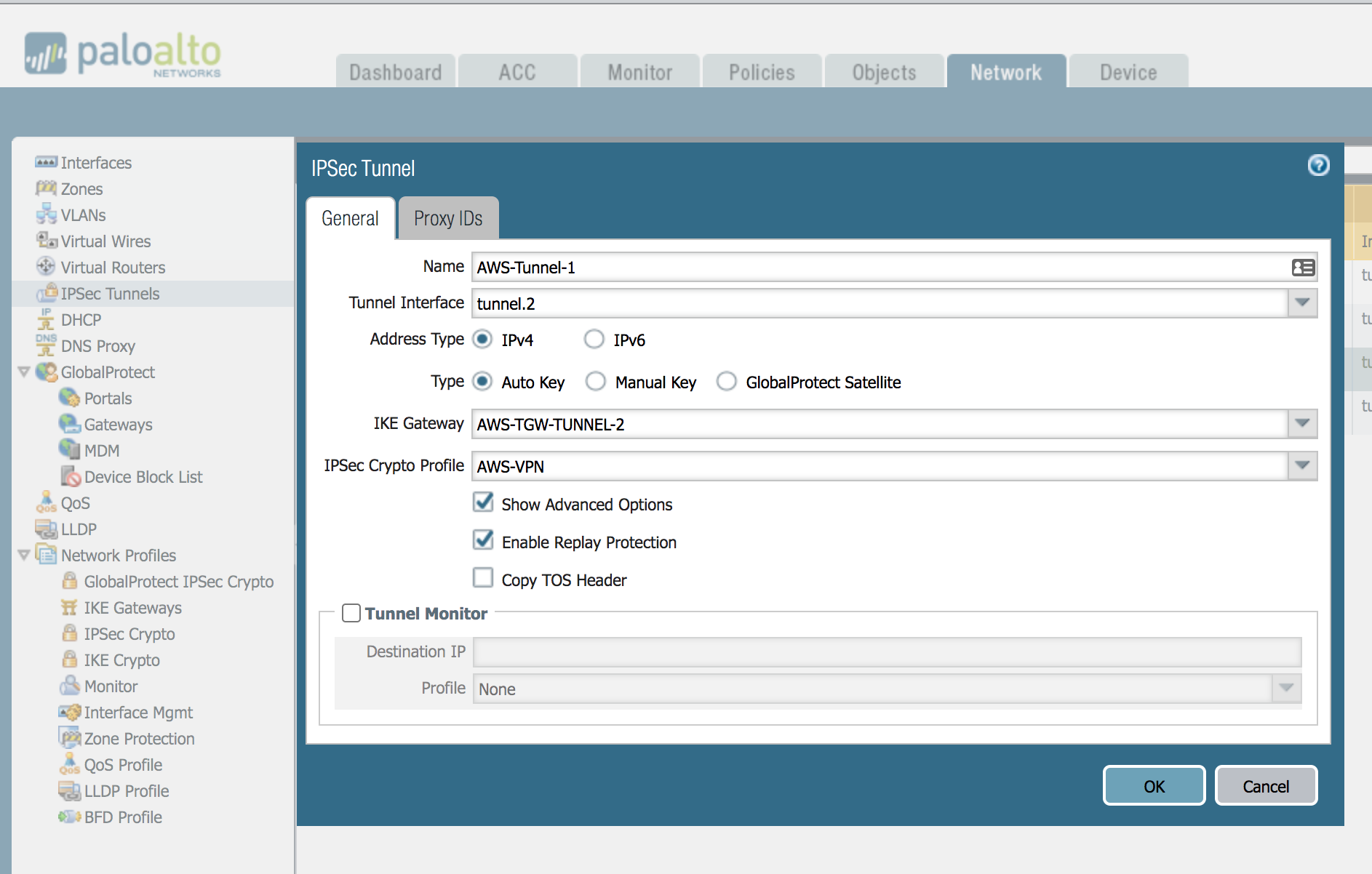
IPSec Tunnel
The IPSec tunnel configuration allows you to authenticate and encrypt the data as it traverses the tunnel. Create 2 x IPSec tunnels.
Monitor profile
Static routing does not allow for failover of traffic between tunnels. If there is a problem with one of the tunnels, we would want to failover the traffic to the second tunnel. This is done by creating a tunnel monitor profile in Palo Alto networks device.
A monitor profile is used to monitor IPSec tunnels and to monitor a next-hop device for policy-based forwarding (PBF) rules. In both cases, the monitor profile is used to specify an action to take when a resource (IPSec tunnel or next-hop device) becomes unavailable.

Policy Based Forwarding (PBF)
To allow for failover between tunnels, we use PBF. We bind the tunnel monitor profile to this policy. When the tunnel monitor reaches its threshold, the policy is removed , and the backup policy becomes active.
Policy-Based Forwarding (PBF) allows you to override the routing table, and specify the outgoing or egress interface based on specific parameters such as source or destination IP address, or type of traffic.
Please create 2 x PBF policies and adjust zone/interface accordingly. Tunnel-2 configuration shown below
- Source Zone- Inside
- Source Address - 192.168.10.0/24
- Destination Address - 10.200.0.0/24
Now one of the Tunnel should come up. In case the Availability Zone associated with the Tunnel goes down, PA will remove the policy from PBF and the traffic will be sent out via the second tunnel.

Reference
https://docs.paloaltonetworks.com/pan-os/8-1/pan-os-admin/policy/policy-based-forwarding
Thanks for reading
As always, your feedback and comments are more than welcome.